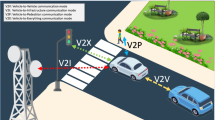
Abstract
Intelligent transportation systems seek to maximize the usage of data generated by the vehicles for road users assistance. Combining vehicular ad hoc network with cloud computing makes it easy for the fixed infrastructures along the roads to collect and analyze safety messages for the benefits of the road users and the transportation authorities. However, security features need to be fully assessed before the adoption of such applications. In this paper, we present a secure vehicle traffic data dissemination and analysis in vehicular cloud computing in which the identity privacy of the vehicles and their generated message is achieved through pseudonym techniques. We use anonymous credential to guarantee the authorization of service demanding vehicles. ID-based signature is applied to assure the authentication of the vehicles for given pseudonyms. The efficient verification of signature on the message and revoked vehicles are achieved through batch verification technique and pseudonymous revocation list, respectively. Traffic estimation methods are applied to mine coarse-grained data collected by road side infrastructures. The merits of the proposed protocol compared to existing ones are shown through extensive simulations.










Similar content being viewed by others
References
Babu P, Rekha NR (2014) Secured gps based traffic monitoring system in pervasive environment. In: Software Engineering and Service Science (ICSESS), 2014 5th IEEE International Conference on, pp. 775–779 (IEEE)
Chim TW, Yiu S, Hui LC, Li VO (2014) Vspn: Vanet-based secure and privacy-preserving navigation. Comp IEEE Trans 63(2):510–524
Cho W, Park Y, Sur C, Rhee KH (2013) An improved privacy-preserving navigation protocol in vanets. J Wireless Mobile Netw Ubiquitous Comput Dependable Appl 4(4):80–92
Committee ITS et al (2006) Ieee trial-use standard for wireless access in vehicular environments-security services for applications and management messages. IEEE Vehic Technol Soc Stand 1609:2006
Eltoweissy M, Olariu S, Younis M (2010) Towards autonomous vehicular clouds. In: Ad hoc networks. Springer, pp 1–16
Festag A, Papadimitratos P, Tielert T (2010) Design and performance of secure geocast for vehicular communication. Vehic Technol IEEE Trans 59(5):2456–2471
Gentry C, Silverberg A (2002) Hierarchical id-based cryptography. In: Advances in cryptologyASIACRYPT 2002. Springer, pp 548–566
Geroliminis N, Daganzo CF (2008) Existence of urban-scale macroscopic fundamental diagrams: Some experimental findings. Trans Res Part B Methodol 42(9):759–770
Haklay M, Weber P (2008) Openstreetmap: user-generated street maps. Pervas Comp IEEE 7(4):12–18
He D, Zeadally S, Xu B, Huang X (2015) An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. Inform Forens Security IEEE Trans 10(12):2681–2691
Herrera JC, Bayen AM (2007) Traffic flow reconstruction using mobile sensors and loop detector data. University of California Transportation Center, California
Hu J, Li G, Yu X, Liu S (2007) Design and application of sae j1939 communication database in city-bus information integrated control system development. In: Mechatronics and Automation, 2007. ICMA 2007. International Conference on. IEEE, pp 3429–3434
Hussain R (2014) Cooperation-aware vanet clouds: providing secure cloud services to vehicular ad hoc networks. J Inform Process Syst 10(1):103–118
Hussain R, Rezaeifar Z, Lee YH, Oh H (2015) Secure and privacy-aware traffic information as a service in vanet-based clouds. Pervas Mobile Comp 24:194–209
Johansson KH, Törngren M, Nielsen L (2005) Vehicle applications of controller area network. In: Handbook of networked and embedded control systems. Springerpp 741–765
Kenney JB (2011) Dedicated short-range communications (dsrc) standards in the united states. Proceed IEEE 99(7):1162–1182
Lee CC, Lai YM (2013) Toward a secure batch verification with group testing for vanet. Wireless Networks 19(6):1441–1449
Lee E, Lee EK, Gerla M, Oh SY (2014) Vehicular cloud networking: architecture and design principles. Commun Magazine IEEE 52(2):148–155
Lee JK, Jeong YS, Park JH (2015) s-itsf: a service based intelligent transportation system framework for smart accident management. Human-centric Comp Inform Sci 5(1):1–9
Li CT, Hwang MS, Chu YP (2008) A secure and efficient communication scheme with authenticated key establishment and privacy preserving for vehicular ad hoc networks. Comp Commun 31(12):2803–2814
Mehran B, Kuwahara M, Naznin F (2012) Implementing kinematic wave theory to reconstruct vehicle trajectories from fixed and probe sensor data. Trans Res Part C Emerg Technol 20(1):144–163
Mohammad SA, Rasheed A, Qayyum A (2011) Vanet architectures and protocol stacks: a survey. In: Communication technologies for vehicles. Springer, pp 95–105
Nakagami M (1960) The m-distribution-a general formula of intensity distribution of rapid fading. Statistical Method of Radio Propagation,
Nkenyereye L, Tama BA, Park Y, Rhee KH (2015) A fine-grained privacy preserving protocol over attribute based access control for vanets. J Wireless Mobile Netw Ubiquitous Comput Dependable Appl 6(2):98–112
Olariu S, Hristov T, Yan G (2013) The next paradigm shift: from vehicular networks to vehicular clouds. Mobile ad hoc networking: cutting edge directions, 2nd edn. John Wiley & Sons, Inc, Hoboken
Olariu S, Khalil I, Abuelela M (2011) Taking vanet to the clouds. Int J Pervas Comp Commun 7(1):7–21
Palomar E, de Fuentes JM, González-Tablas AI, Alcaide A (2012) Hindering false event dissemination in vanets with proof-of-work mechanisms. Trans Res Part C Emerg Technol 23:85–97
Park H, Miloslavov A, Lee J, Veeraraghavan M, Park B, Smith B (2011) Integrated traffic-communication simulation evaluation environment for intellidrive applications using sae j2735 message sets. Trans Res Record J Trans Res Board 2243:117–126
Raya M, Hubaux JP (2007) Securing vehicular ad hoc networks. J Comp Security 15(1):39–68
Seo T, Kusakabe T, Asakura Y (2015) Estimation of flow and density using probe vehicles with spacing measurement equipment. Trans Res Part C Emerg Technol 53:134–150
Sur C, Park Y, Rhee KH (2014) An efficient and secure navigation protocol based on vehicular cloud. International Journal of Computer Mathematics (ahead-of-print), pp 1–20
Torrent-Moreno M, Santi P, Hartenstein H (2005) Fair sharing of bandwidth in vanets. In: Proceedings of the 2nd ACM international workshop on Vehicular ad hoc networks. ACM, pp 49–58
Unterluggauer T, Wenger E (2014) Efficient pairings and ecc for embedded systems. In: Cryptographic Hardware and Embedded Systems–CHES 2014. Springer, pp 298–315
Whaiduzzaman M, Sookhak M, Gani A, Buyya R (2014) A survey on vehicular cloud computing. J Network Comp Appl 40:325–344
Yu R, Zhang Y, Gjessing S, Xia W, Yang K (2013) Toward cloud-based vehicular networks with efficient resource management. Network IEEE 27(5):48–55
Zhang C, Lin X, Lu R, Ho PH (2008) Raise: An efficient rsu-aided message authentication scheme in vehicular communication networks. In: Communications, 2008. ICC’08. IEEE International Conference on, pp 1451–1457. IEEE
Zhang T, Delgrossi L (2012) Vehicle safety communications: protocols, security, and privacy, vol 103. Wiley, USA
Zhu J, Roy S (2003) Mac for dedicated short range communications in intelligent transport system. Commun Magazine IEEE 41(12):60–67
Acknowledgments
This work was supported by the National Research Foundation of Korea (NRF) Grant funded by the Korea government (MSIP) (No. NRF-2014R1A2A1A11052981).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Nkenyereye, L., Park, Y. & Rhee, KH. Secure vehicle traffic data dissemination and analysis protocol in vehicular cloud computing. J Supercomput 74, 1024–1044 (2018). https://doi.org/10.1007/s11227-016-1773-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-016-1773-0