Abstract
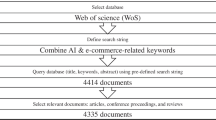
Information cascades and network externalities have been increasingly influential in explaining the many market outcomes of information technology (IT), but their application to ethical issues of IT has been limited. This study proposes a conceptual model of unethical intention of software piracy by integrating information cascades and network externalities in terms of a theoretical perspective from the literature of economics. In the conceptual model, unethical intention of software piracy is proposed to be influenced by the network benefits of using pirated software, while the network benefits are proposed to be affected by the overall adopter base of pirated software directly and indirectly through the availability of pirated complementary software. Accordingly, whereas the perception of others’ piracy is proposed to be influenced by the overall adopter base of pirated software, the unethical intention of software piracy is proposed to be influenced indirectly by the perception of others’ piracy through the perceived signal that piracy seems a good idea. Finally, this study also provides the conclusion and limitation.
Similar content being viewed by others
References
Asvanund A., Clay K., Krishnan R., Smith M.D.: An empirical analysis of network externalities in peer-to-peer music-sharing networks. Inf. Syst. Res. 15, 155–174 (2004)
Bikhchandani S., Hirshleifer D., Welch I.: A theory of fads, fashion, custom and cultural change as informational cascades. J. Polit. Econ. 100, 992–1026 (1992)
Bikhchandani S., Hirshleifer D., Welch I.: Learning from the behavior of others: conformity, fads, and informational cascades. J. Econ. Perspect. 12, 151–170 (1998)
Crotts J.C., Erdmann R.: Does national culture influence consumers’ evaluation of travel services? A test of Hofstede’s model of cross-cultural differences. Manag. Serv. Qual. 10, 410–419 (2000)
Dann G.: Limitations in the use of nationality and country of residence variables. In: Pearce, D., Butler, R.(eds) Tourism Research: Critiques and Challenges, pp. 88–112. Routledge, London (1993)
Deephouse D.L.: Does isomorphism legitimate? Acad. Manag. J. 39, 1024–1039 (1996)
DiMaggio P.J., Powell W.W.: The iron cage revisited: institutional isomorphism and collective rationality in organizational fields. Am. Sociol. Rev. 48, 147–160 (1983)
Gupta P.B., Gould S.J., Pola B.: To pirate or not to pirate: A comparative study of the ethical versus other influences on the consumer’s software acquisition-mode decision. J. Bus. Ethics 55, 255–274 (2004)
Haveman H.A.: Follow the leader: mimetic isomorphism and entry into new markets. Adm. Sci. Quart. 38, 593–627 (1993)
Katz M.L., Shapiro C.: Network externalities, competition, and compatibility. Am. Econ. Rev. 75, 424–440 (1985)
Katz M.L., Shapiro C.: Technology adoption in the presence of network externalities. J. Polit. Econ. 94, 822–841 (1986)
Katz M.L., Shapiro C.: Systems Competition and Network Effects. J. Econ. Perspect. 8, 93–115 (1994)
Kauffman R.J., McAndrews J., Wang Y.M.: Opening the black box of network externalities in network adoption. Inf. Sys. Res. 11, 61–82 (2000)
King S.P., Lampe R.: Network externalities, price discrimination and profitable piracy. Inf. Econ. Pol. 15, 271–290 (2003)
Liebowitz S.J., Margolis S.E.: Are network externalities a new source of market failure? Res. Law Econ. 17, 1–22 (1995)
Lin, C.P.: Modeling educational quality and student loyalty: a quantitative approach based on the theory of information cascades. Qual. Quant. (in press)
Schilling M.A.: Technology success and failure in winner-take-all markets: the impact of learning orientation, timing, and network externalities. Acad. Manag. J. 45, 387–398 (2002)
Shapiro C., Varian H.R.: Information Rules: A Strategic Guide to the Network Economy. Harvard Business School Press, Cambridge (1999)
Sims R.R., Cheng H.K., Teegen H.: Toward a profile of student software piraters. J. Bus. Ethics 15, 839–849 (1996)
Song, J., Walden, E. A.: Consumer behavior in the adoption of peer-to-peer technologies: an empirical examination of information cascades and network externalities. In: Proceedings of the 9th Americas Conference on Information Systems (AMCIS) (Tampa, Florida), pp. 1801–1810 (2003)
Tingling P., Parent M.: Mimetic isomorphism and technology evaluation: does limitation transcend judgment? J. Assoc. Inf. Syst. 3, 113–143 (2003)
Van Hove L.: Electronic money and the network externalities theory: lessons for real life. Netnomics Econ. Res. Electron. Netw. 1, 137–171 (1999)
Wagner S.C., Sanders G.L.: Considerations in ethical decision-making and software piracy. J. Bus. Ethics 29, 161–167 (2001)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Joe, SW., Lin, SY. & Chiu, CK. Modeling the unethical intention of software piracy: a qualitative integration of network externalities and information cascades. Qual Quant 44, 191–198 (2010). https://doi.org/10.1007/s11135-008-9188-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11135-008-9188-5