Abstract
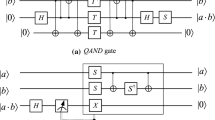
In recent years, the quantum implementation of symmetric ciphers has received much attention. In this paper, we investigate the construction of quantum circuits based on different gate sets for the SM4 block cipher, which is the national standard of commercial cryptography of China and is standardized in ISO/IEC. First, we construct reversible circuits using Pauli-X gates, CNOT gates and Toffoli gates (i.e., the NCT gate set) for the SM4 S-box, based on which we design two circuits for the SM4 S-box with Clifford+T gates by applying the quantum And gate and existing decomposition scheme of the Toffoli gate, respectively. In addition, we propose a new in-place 1 implementation for the linear transformation in the SM4 round function. Finally, taking the qubit consumption and the \(T{\cdot } M\) value (the product of qubit consumption and nonlinear gate depth of a quantum circuit) as metrics, we investigate the application of various circuits we designed to the construction of quantum circuits for SM4. The results show that we can always construct a subroutine/stand-alone circuit based on the NCT gate set, or based on Clifford+T gates for SM4 with fewer qubits or lower \(T {\cdot } M\) value than existing state-of-the-art implementations.






Similar content being viewed by others
Data availability
The datasets generated during and/or analyzed during the current study are available at https://github.com/Supporting-Material/The-SM4-Sbox-in-quantum.
Notes
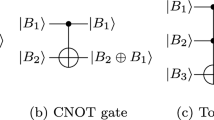
Note that the qubit cannot be copied. The operation of coping the value stored in a qubit can be completed by introducing an ancilla qubits \(|0\rangle \) and then utilizing the CNOT gate that takes \(|0\rangle \) as the target qubit.
References
Grover, L.K.: A fast quantum mechanical algorithm for database search. In: Gary L. Miller, (ed), In: Proceedings of the Twenty-Eighth Annual ACM Symposium on the Theory of Computing, Philadelphia, Pennsylvania, USA, May 22-24, 1996, pp. 212–219. ACM (1996)
Simon, D.R.: On the power of quantum computation. SIAM J. Comput. 26(5), 1474–1483 (1997)
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26(5), 1484–1509 (1997)
Daemen, J., Rijmen, V.: The Design of Rijndael: AES—The Advanced Encryption Standard. Information Security and Cryptography. Springer, Berlin (2002)
Almazrooie, M., Samsudin, A., Abdullah, R., Mutter, K.N.: Quantum reversible circuit of AES-128. Quantum Inf. Process. 17(5), 112 (2018)
Grassl, M., Langenberg, B., Roetteler, M., Steinwandt, R.: Applying Grover’s algorithm to AES: quantum resource estimates. In: Takagi, T., (eds.), Post-Quantum Cryptography—7th International Workshop, PQCrypto 2016, Fukuoka, Japan, February 24-26, 2016, Proceedings, vol. 9606 of Lecture Notes in Computer Science, pp. 29–43. Springer, (2016)
Huang, Z., Sun, S.: Synthesizing quantum circuits of aes with lower t-depth and less qubits. In: Agrawal, S., Lin, D. (eds.), Advances in Cryptology - ASIACRYPT 2022 - 28th International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, December 5-9, 2022, Proceedings, Part III, volume 13793 of Lecture Notes in Computer Science, pp. 614–644. Springer (2022)
Jang, K., Baksi, A., Song, G., Kim, H., Seo, H., Chattopadhyay, A.: Quantum analysis of aes. IACR Cryptol. ePrint Arch. 2022, 683 (2022)
Jaques, S., Naehrig, M., Roetteler, M., Virdia, F.: Implementing grover oracles for quantum key search on AES and lowmc. In: Canteaut, A., Ishai, Y., (eds.), Advances in Cryptology - EUROCRYPT 2020 - 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, May 10-14, 2020, Proceedings, Part II, volume 12106 of Lecture Notes in Computer Science, pp. 280-310. Springer (2020)
Kim, P., Han, D., Jeong, K.C.: Time-space complexity of quantum search algorithms in symmetric cryptanalysis: applying to AES and SHA-2. Quantum Inf. Process. 17(12), 1–39 (2018)
Langenberg, B., Pham, H., Steinwandt, R.: Reducing the cost of implementing the advanced encryption standard as a quantum circuit. IEEE Trans. Quantum Eng. 2020(1), 1–12 (2020)
Li, Z., Cai, B., Sun, H., Liu, H., Wan, L., Qin, S., Wen, Q., Gao, F.: Novel quantum circuit implementation of Advanced Encryption Standard with low costs. Sci. China Phys. Mech. Astron. 65(9), 290311 (2022)
Li, Z., Gao, F., Qin, S., Wen, Q.: New record in the number of qubits for a quantum implementation of AES. IACR Cryptol. ePrint Arch. 2023, 018 (2023)
Lin, D., Xiang, Z., Xu, R., Zhang, S., Zeng, X.: Optimized Quantum Implementation of AES. IACR Cryptol. ePrint Arch. 2023, 146 (2023)
Wang, Z., Wei, S., Long, G.: A quantum circuit design of AES requiring fewer quantum qubits and gate operations. Front. Phys. 17(4), 1–7 (2022)
Zou, J., Wei, Z., Sun, S., Liu, X., Wu, W.: Quantum circuit implementations of AES with fewer qubits. In: Moriai, S., Wang, H. (eds.), Advances in Cryptology - ASIACRYPT 2020 - 26th International Conference on the Theory and Application of Cryptology and Information Security, Daejeon, South Korea, December 7-11, 2020, Proceedings, Part II, volume 12492 of Lecture Notes in Computer Science, pp. 697–726. Springer (2020)
Standardization Administration of the P. R. China: GB/T32907-2016. In: Information Security Technology-SM4 Block Cipher Algorithm (2016)
Lin, D., Xiang, Z., Zhang, R., Zhang, S., Zeng, X.: Quantum implementation of SM4 (in Chinese). J. Cryptol. Res. 8(6), 999–1018 (2021)
Zou, J., Li, L., Wei, Z., Luo, Y., Liu, Q., Wu, W.: New quantum circuit implementations of SM4 and SM3. Quantum Inf. Process. 21(5), 1–38 (2022)
Abbasi, I., Afzal, M.: A compact S-Box design for SMS4 block cipher. In: IT Convergence and Services, Lecture Notes in Electrical Engineering, pp. 641–658. Springer (2011)
Bai, X., Xu, Y., Guo, L.: Securing SMS4 cipher against differential power analysis and its VLSI implementation. In: 2008 11th IEEE Singapore International Conference on Communication Systems, Guangzhou, China, November 19-21, 2008, pp. 167–172. IEEE Xplore (2008)
Martínez-Herrera, A.F., Mex-Perera, C., Nolazco-Flores, J.: Merging the camellia, SMS4 and AES s-boxes in a single s-box with composite bases. In: Desmedt, Y. (eds.), 16th International Conference, ISC 2013, Dallas, Texas, November 13-15, 2013, Proceedings, volume 7807 of Lecture Notes in Computer Science, pp. 209–217. Springer (2013)
Wei, Z., Sun, S., Hu, L., Wei, M., Boyar, J., Peralta, R.: Scrutinizing the Tower Field Implementation of the \(\mathbb{F} _{2^8}\) Inverter-with Applications to AES, Camellia, and SM4. IACR Cryptol. ePrint Arch. 2019, 738 (2019)
Albrecht, M.R., Rechberger, C., Schneider, T., Tiessen, T., Zohner, M.: Ciphers for MPC and FHE. In: Oswald, E., Fischlin, M. (eds.), Advances in Cryptology - EUROCRYPT 2015 - 34th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, April 26-30, 2015, Proceedings, Part I, volume 9056 of Lecture Notes in Computer Science, pp. 430-454. Springer (2015)
Zou, J., Wei, Z., Sun, S., Luo, Y., Liu, Q., Wu, W.: Some efficient quantum circuit implementations of camellia. Quantum Inf. Process. 21(4), 1–27 (2022)
Xiang, Z., Zeng, X., Lin, D., Bao, Z., Zhang, S.: Optimizing implementations of linear layers. IACR Trans. Symmetric Cryptol. 2020(2), 120–145 (2020)
Shende, V.V., Prasad, A.K., Markov, I.L., Hayes, J.P.: Synthesis of reversible logic circuits. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 22(6), 710–722 (2003)
Jean, J., Peyrin, T., Sim, S.M., Tourteaux, J.: Optimizing implementations of lightweight building blocks. IACR Trans. Symmetric Cryptol. 2017(4), 130–168 (2017)
Amy, M., Maslov, D., Mosca, M., Roetteler, M.: A meet-in-the-middle algorithm for fast synthesis of depth-optimal quantum circuits. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 32(6), 818–830 (2013)
Funding
This work was supported by the National Key Research and Development Program of China (Grant No.2021YFA1000600), the National Natural Science Foundation of China (Grant No.62272147) and the Wuhan Science and Technology Bureau (Grant No.2022010801020328).
Author information
Authors and Affiliations
Contributions
Da Lin and Zejun Xiang derived the methodology. Runqing Xu simulated the theoretical results. Xiangyong Zeng and Shasha Zhang provided data and format analysis. All authors contributed to the preparation of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors have no competing interests to declare that are relevant to the content of this article.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A: NCT-based circuit of the SM4 S-box
1.1 A.1 The reversible circuit of \(H_1\)
1.2 A.2 The reversible circuit of \(H_2\) with Toffoli depth 6
1.3 A.3 The reversible circuit of \(H_2\) with Toffoli depth 5
1.4 A.4 The reversible circuit of \(H_3\)

Appendix B: Binary matrix corresponds to L

Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Lin, D., Xiang, Z., Xu, R. et al. Quantum circuit implementations of SM4 block cipher based on different gate sets. Quantum Inf Process 22, 282 (2023). https://doi.org/10.1007/s11128-023-04002-4
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-023-04002-4