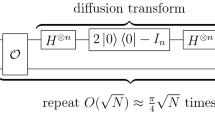
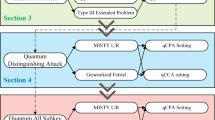
Abstract
Exploiting quantum mechanisms, quantum attacks have the potential ability to break the cipher structure. Recently, Ito et al. proposed a quantum attack on Feistel-2* structure (Ito et al.’s attack) based on the Q2 model. However, it is not realistic since the quantum oracle needs to be accessed by the adversary, and the data complexity is high. To solve this problem, a quantum all-subkeys-recovery (ASR) attack based on multi-equations quantum claw-finding is proposed, which takes a more realistic model, the Q1 model, as the scenario, and only requires 3 plain-ciphertext pairs to quickly crack the 6-round Feistel-2* structure. First, we proposed a multi-equations quantum claw-finding algorithm to solve the claw problem of finding multiple equations. In addition, Grover’s algorithm is used to speedup the rest subkeys recovery. Compared with Ito et al.’s attack, the data complexity of our attack is reduced from \(O(2^n)\) to O(1), while the time complexity and memory complexity are also significantly reduced.




Similar content being viewed by others
Data availability
All data generated or analyzed during this study are included in this published article [and its supplementary information files].
References
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 41(2), 303–332 (1999)
Grover, L.K.: A fast quantum mechanical algorithm for database search. In: Proceedings of STOC’96, pp. 212-219 (1996)
Long, G.: Grover algorithm with zero theoretical failure rate. Phys. Rev. A 64(2), 022307 (2001)
Toyama, F., van Dijk, W., Nogami, Y.: Quantum search with certainty based on modified grover algorithms: optimum choice of parameters. Quantum Inf. Process. 12(5), 1897–1914 (2013)
Gregor, L., Alexander, M.: Grover meets simon-quantumly attacking the fxconstruction. In: International Conference on the Theory and Application of Cryptology and Information Security, pp. 161-178 (2017)
Hidenori, K., Masakatu, M.: Quantum distinguisher between the 3-round Feistel cipher and the random permutation. In: 2010 IEEE International Symposium on Information Theory, IEEE, pp. 2682-2685 (2010)
Daniel, R.S.: On the power of quantum computation. SIAM J. Comput. 26(5), 1474–1483 (1997)
Hidenori, K., Masakatu, M.: Security on the quantum-type even-mansour cipher. In: 2012 International Symposium on Information Theory and its Applications, IEEE, pp. 312-316 (2012)
Kaplan, M., Leurent, G., Leverrier, A., Naya-Plasencia, M.: Breaking symmetric cryptosystems using quantum period finding. In: Robshaw, M., Katz, J. (eds.) Advances in Cryptology-CRYPTO 2016. Springer, Berlin (2016)
Santoli, T., Schaffner, C.: Using simon’s algorithm to attack symmetric-key cryptographic primitives. Quantum Inf. Comput. 17, 65–78 (2017)
Shi, T., Chen, H., Guan, J.: Collision attacks against AEZ-PRF for authenticated encryption AEZ. China Commun. 15(2), 46–53 (2018)
Xu, Y., Liu, W., Yu, W.: Quantum forgery attacks on COPA, AES-COPA and marble authenticated encryption algorithms. Quantum Inf. Process. 20(4), 1–21 (2021)
Xavier, B., María, N.-P., André, S.: On quantum slide attacks. In: Kenneth G. Paterson and Douglas Stebila eds., Selected Areas in Cryptography-SAC, pp. 492-519 (2020)
Dong, X., Wang, X.: Quantum key-recovery attack on feistel structures. Sci. China Inf. Sci. 61(10), 1–7 (2018)
Dong, X., Li, Z., Wang, X.: Quantum cryptanalysis on some generalized feistel schemes. Sci. China Inf. Sci. 62(2), 22501 (2019)
Dong, X., Dong, B., Wang, X.: Quantum attacks on some feistel block ciphers. Des. Codes Crypt. 88(6), 1–25 (2020)
Hosoyamada, A., Sasaki, Y.: Quantum Demiric-Seluk Meet-in-the-Middle Attacks: Applications to 6-Round Generic Feistel Constructions. In: International Conference on Security and Cryptography for Networks, pp. 386-403 (2018)
Kaplan, M., Leurent, G., Leverrier, A., Naya-Plasencia, M.: Quantum differential and linear cryptanalysis. IACR Trans. Symmetric Cryptol. 2016(1), 71–94 (2016)
Feistel, H.: Cryptography and computer privacy. Sci. Am. 228(5), 15–23 (1973)
Coppersmith, D.: The data encryption standard (des) and its strength against attacks. IBM J. Res. Dev. 38(3), 243–250 (1994)
Aoki, K., Ichikawa, T., Kanda, M.e.a.: Camellia: A 128-Bit Block Cipher Suitable for Multiple Platforms - Design andAnalysis. In: Stinson D.R., Tavares S. (eds) Selected Areas in Cryptography. SAC 2000. Lecture Notes in Computer Science, vol. 2012. pp. 39-56 (2001)
Adams, C.: The cast-128 encryption algorithm. RFC 81(4), 864–894 (1997)
Yang, D., Qi, W., Tian, T.: All-subkeys-recovery attacks on a variation of feistel-2 block ciphers. IET Inf. Secur. 11(5), 230–234 (2017)
Ito, G., Hosoyamada, A., Matsumoto, R., Sasaki, Y., Iwata, T.: Quantum chosen-ciphertext attacks against Feistel ciphers. In: Matsui, M. (ed.) Topics in Cryptology-CT-RSA 2019. Springer, Berlin (2019)
Isobe, T., Shibutani, K.: Generic key recovery attack on Feistel scheme. In: Sako, K., Sarkar, P. (eds.) Advances in Cryptology - ASIACRYPT 2013. Springer, Berlin (2013)
Andris, A.: Quantum walk algorithm for element distinctness. SIAM J. Comput. 37(1), 210–239 (2007)
Zhang, S.: Promised and distributed quantum search. In: Wang, L. (ed.) Computing and Combinatorics. COCOON 2005. Springer, Berlin (2005)
Grover, L.K.: A framework for fast quantum mechanical algorithms. In: Proceedings of STOC’98, pp.53-62 (1998)
Yang, G., Zhu, B., Suder, V., Aagaard, M.D., Gong, G.: The simeck family of lightweight block ciphers. Lecture Notes Artificial Intelligence, pp 307–329 (2015)
Kolbl, S., Roy, A.: A brief comparison of Simon and Simeck. In: Lightweight Cryptography for Security and Privacy: 5th International Workshop, LightSec 2016, Aksaray, Turkey, September 21-22, 2016, Revised Selected Papers 5 (pp. 69-88). Springer International Publishing
Brandon, L., Hai, P., Rainer, S.: Reducing the cost of implementing the advanced encryption standard as a quantum circuit. IEEE Trans. Quantum Eng. 1, 2500112 (2020)
Wang, Z., Wei, S., Long, G.: A quantum circuit design of AES requiring fewer quantum qubits and gate operations. Front. Phys. 17(4), 41501 (2022)
Wang, Z., Wei, S., Long, G.L., Hanzo, L.: Variational quantum attacks threaten advanced encryption standard based symmetric cryptography. Sci. China Inform. Sci. 65(10), 200503 (2022)
Acknowledgements
This work is supported by the National Natural Science Foundation of China (62071240) the Innovation Program for Quantum Science and Technology (2021ZD0302902), and the Priority Academic Program Development of Jiangsu Higher Education Institutions (PAPD).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
Authors have no conflict of interest to declare.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Liu, W., Wang, M. & Li, Z. Quantum all-subkeys-recovery attacks on 6-round Feistel-2* structure based on multi-equations quantum claw finding. Quantum Inf Process 22, 142 (2023). https://doi.org/10.1007/s11128-023-03877-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-023-03877-7