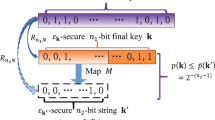
Abstract
Quantum key distribution can provide information-theoretic security keys. In practice, the eavesdropper may attack the transmitted quantum state, which makes some information leakage to the generated key. The security of the final key depends on how difficult it is for the eavesdropper to guess the key. The guessing probability is bounded by the trace distance between the practical generated quantum state and the ideal quantum state and hence can be applied to estimate security of quantum key distribution. With the trace distance \(\varepsilon \) and the secret key length n, we prove that the guessing probability can reach the upper bound \(\varepsilon +2^{-n}\) in some special cases. We show that different attacking strategies will give different numbers of guesses, sometimes even completely subversive differences, to get the final key. Our results demonstrate that the appropriate security parameter \(\varepsilon \) should be carefully selected to guarantee the security of the generated key.
Similar content being viewed by others
Data Availability
The data that support the findings of this study are available from the corresponding authors on request.
References
Bennett, C.H., Brassard, G.: Quantum cryptography: Public key distribution and coin tossing. In: roceedings of IEEE international conference on computers, systems and signal processing, Bangalore, India. New York: IEEE, 175–179 (1984)
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283, 2050 (1999)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85, 441 (2000)
Renner, R.: Security of quantum key distribution. Int. J. Quantum Inf. 6(01), 1–127 (2008)
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N.J., et al.: The security of practical quantum key distribution. Rev. Mod. Phys. 81(3), 1301 (2009)
Li, H.W., Wang, S., Huang, J.Z., et al.: Attacking a practical quantum-key-distribution system with wavelength-dependent beam-splitter and multiwavelength sources. Phys. Rev. A 84(6), 062308 (2011)
Li, H.W., Xu, Z.M., Cai, Q.Y.: Small imperfect randomness restricts security of quantum key distribution. Phys. Rev. A 98, 062325 (2018)
Kraus, B., Gisin, N., Renner, R.: Lower and upper bounds on the secret-key rate for quantum key distribution protocols using one-way classical communication. Phys. Rev. Lett. 95, 080501 (2005)
Renner, R., Gisin, N., Kraus, B.: Information-theoretic security proof for quantum-key-distribution protocols. Phys. Rev. A 72, 012332 (2005)
Portmann, C., Renner, R.: Cryptographic security of quantum key distribution. Preprint at: arxiv.org/abs/1409.3525 (2014)
Portmann, C., Renner, R.: Security in quantum cryptography. Preprint at: arxiv.org/abs/2102.00021 (2021)
Tomamichel, M., Schaffner, C., Smith, A., et al.: Leftover hashing against quantum side information. IEEE Trans. Inf. Theory 57, 5524 (2011)
Holenstein, T., Renner, R.: On the randomness of independent experiments. IEEE Trans. Inf. Theory 57, 1865 (2011)
Tomamichel, M., Colbeck, R., Renner, R.: A fully quantum asymptotic equipartition property. IEEE Trans. Inf. Theory 55, 5840 (2009)
Wang, X.B., Wang, J.T., Qin, J.Q., et al.: Guessing probability in quantum key distribution. NPJ Quantum Inf. 6, 45 (2020)
Yuen, H.P.: Security of quantum key distribution. IEEE Access 4, 724 (2016)
De, A., Portmann, C., Vidick, T., et al.: Trevisan’s extractor in the presence of quantum side information. SIAM J. Comput. 41, 915 (2009)
Radhakrishnan, J., Ta-Shma, A.: Bounds for dispersers, extractors, and depth-two superconcentrators. SIAM J. Discret. Math. 13(1), 2–24 (2000)
Konig, R., Renner, R., Schaffner, C.: The operational meaning of min and max-entropy. IEEE Trans. Inf. Theory 55, 4337 (2009)
Arnon-Friedman, R.: Reductions to IID in device-independent quantum information processing. PhD thesis, arXiv:1812.10922, (2018)
Tomamichel, M.: A framework for non-asymptotic quantum information theory. PhD thesis, arXiv:1203.2142, (2012)
Tomamichel, M., Lim, C., Gisin, N., et al.: Tight finite-key analysis for quantum cryptography. Nat. Commun. 3, 634 (2012)
Dupuis, F., Fawzi, O., Renner, R.: Entropy accumulation. Commun. Math. Phys. 379, 867–913 (2020)
Zhang, Y., Knill, E., Bierhorst, P.: Certifying quantum randomness by probability estimation. Phys. Rev. A 98(4), 040304 (2018)
Qian, Y.J., Li, H.W., He, D.Y., et al.: Countermeasure against probabilistic blinding attack in practical quantum key distribution systems. Chin. Phys. B 24, 090305 (2015)
Massey, J.L.: Guessing and entropy. In: proceedings of the IEEE international symposium on information theory. 204 (1994)
Pliam, J.: The disparity between work and entropy in cryptology. Cryptology ePrint Archive, Report 1998/024, (1998)
Hanson, E.P., Katariya, V., Datta, N., et al.: Guesswork with quantum side information. arXiv:2001.03598, (2020)
Acknowledgements
The author would like to thank Yan-Bao Zhang, Christopher Portmann, Marcin Pawlowski, Rong Wang and Zhen-Qiang Yin for their helpful discussions. This work is supported by the National Natural Science Foundation of China (Grant No. U2130205), the National Key Research and Development Program of China (Grant No. 2020YFA0309702) and the Natural Science Foundation of Henan (Grant No. 202300410532).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Li, HW., Shi, JH., Cai, QY. et al. Estimating security of the quantum key distribution from the guesswork. Quantum Inf Process 21, 142 (2022). https://doi.org/10.1007/s11128-022-03487-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-022-03487-9