Abstract
Quantum secret sharing is a method for sharing a secret quantum state among a number of individuals such that certain authorized subsets of participants can recover the secret shared state by collaboration and other subsets cannot. In this paper, we first propose a method for sharing a quantum secret in a basic (2, 3) threshold scheme, only by using qubits and the 7-qubit CSS code. Based on this (2, 3) scheme, we propose a new (n, n) scheme, and we also construct a quantum secret sharing scheme for any quantum access structure by induction. Secondly, based on the techniques of performing quantum computation on 7-qubit CSS codes, we introduce a method that authorized subsets can perform universal quantum computation on this shared state, without the need for recovering it. This generalizes recent attempts for doing quantum computation on (n, n) threshold schemes.













Similar content being viewed by others
Notes
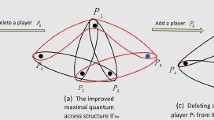
More precisely, if the discarded share contains no important data, which means it is not included in any minimal authorized set, the resulting access structure is still maximal. This means that the purification produces a redundant share, that is what we desire.
References
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Blakley, G.R., et al.: Safeguarding cryptographic keys. Proc. Natl. Comput. Conf. 48, 313–317 (1979)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829 (1999)
Karlsson, A., Koashi, M., Imoto, N.: Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 59(1), 162 (1999)
Smith, A.D.: Quantum secret sharing for general access structures. arXiv preprint arXiv:quant-ph/0001087 (2000)
Cleve, R., Gottesman, D., Lo, H.-K.: How to share a quantum secret. Phys. Rev. Lett. 83, 648–651 (1999)
Gottesman, D.: Theory of quantum secret sharing. Phys. Rev. A 61, 042311 (2000)
Imai, H., Müller-Quade, J., Nascimento, A.C., Tuyls, P., Winter, A.: A quantum information theoretical model for quantum secret sharing schemes. arXiv preprint arXiv:quant-ph/0311136 (2003)
Bai, C.-M., Li, Z.-H., Xu, T.-T., Li, Y.-M.: A generalized information theoretical model for quantum secret sharing. Int. J. Theor. Phys. 55(11), 4972–4986 (2016)
Bennett, C.H., Bessette, F., Brassard, G., Salvail, L., Smolin, J.: Experimental quantum cryptography. J. Cryptol. 5(1), 3–28 (1992)
Gröblacher, S., Jennewein, T., Vaziri, A., Weihs, G., Zeilinger, A.: Experimental quantum cryptography with qutrits. New J. Phys. 8(5), 75 (2006)
Liang, W.-Y., Li, M., Yin, Z.-Q., Chen, W., Wang, S., An, X.-B., Guo, G.-C., Han, Z.-F.: Simple implementation of quantum key distribution based on single-photon bell-state measurement. Phys. Rev. A 92, 012319 (2015)
Broadbent, A., Fitzsimons, J., Kashefi, E.: Proceedings of the 50th Annual IEEE Symposium on Foundations of Computer Science (2009)
Barz, S., Kashefi, E., Broadbent, A., Fitzsimons, J.F., Zeilinger, A., Walther, P.: Demonstration of blind quantum computing. Science 335(6066), 303–308 (2012)
Ouyang, Y., Tan, S.-H., Fitzsimons, J.F.: Quantum homomorphic encryption from quantum codes. Phys. Rev. A 98, 042334 (2018)
Karimipour, V., Asoudeh, M.: Quantum secret sharing and random hopping: using single states instead of entanglement. Phys. Rev. A 92, 030301 (2015)
Bagherinezhad, S., Karimipour, V.: Quantum secret sharing based on reusable Greenberger–Horne–Zeilinger states as secure carriers. Phys. Rev. A 67, 044302 (2003)
Song, X.-L., Liu, Y.-B., Deng, H.-Y., Xiao, Y.-G.: (t, n) threshold d-level quantum secret sharing. Sci. Rep. 7(1), 6366 (2017)
Gordon, G., Rigolin, G.: Generalized quantum-state sharing. Phys. Rev. A 73(6), 062316 (2006)
Qin, H., Dai, Y.: Proactive quantum secret sharing. Quantum Inf. Process. 14(11), 4237–4244 (2015)
Ouyang, Y., Tan, S.-H., Zhao, L., Fitzsimons, J.F.: Computing on quantum shared secrets. Phys. Rev. A 96(5), 052333 (2017)
Fortescue, B., Gour, G.: Reducing the quantum communication cost of quantum secret sharing. IEEE Trans. Inf. Theory 58(10), 6659–6666 (2012)
Bai, C.-M., Li, Z.-H., Si, M.-M., Li, Y.-M.: Quantum secret sharing for a general quantum access structure. Eur. Phys. J. D 71(10), 255 (2017)
Knill, E., Laflamme, R., Viola, L.: Theory of quantum error correction for general noise. Phys. Rev. Lett. 84, 2525–2528 (2000)
Gottesman, D.: Stabilizer codes and quantum error correction. arXiv preprint arXiv:quant-ph/9705052 (1997)
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature 299(5886), 802–803 (1982)
Calderbank, A.R., Shor, P.W.: Good quantum error-correcting codes exist. Phys. Rev. A 54, 1098–1105 (1996)
Gottesman, D., Chuang, I.L.: Demonstrating the viability of universal quantum computation using teleportation and single-qubit operations. Nature 402(6760), 390 (1999)
Zhou, X., Leung, D.W., Chuang, I.L.: Methodology for quantum logic gate construction. Phys. Rev. A 62, 052316 (2000)
Bennett, C.H., Brassard, G., Mermin, N.D.: Quantum cryptography without Bell’s theorem. Phys. Rev. Lett. 68, 557–559 (1992)
Dunjko, V., Fitzsimons, J.F., Portmann, C., Renner, R.: Composable security of delegated quantum computation. In: International Conference on the Theory and Application of Cryptology and Information Security, pp. 406–425. Springer, Berlin (2014)
Acknowledgements
We thank the referees, specially one of them, whose very careful reading of the manuscript and very valuable comments led to a much better presentation of this article. This work was done with a support from the research council of the Sharif University of Technology, and with the financial support from Sharif University of Technology under Grant No. G951418, and with partial support from Iran National Science Foundation under the Grant INSF-96011347.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Bassirian, R., Boreiri, S. & Karimipour, V. Computing on quantum shared secrets for general quantum access structures. Quantum Inf Process 18, 109 (2019). https://doi.org/10.1007/s11128-019-2224-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-019-2224-7