Abstract
RFID systems became widespread in variety of applications because of their simplicity in manufacturing and usability. In the province of critical infrastructure protection, RFID systems are usually employed to identify and track people, objects and vehicles that enter restricted areas. The most important vulnerability which is prevalent among all protocols employed in RFID systems is against relay attacks. Until now, to protect RFID systems against this kind of attack, the only approach is the utilization of distance-bounding protocols which are not applicable over low-cost devices such as RFID passive tags. This work presents a novel technique using emerging quantum technologies to detect relay attacks on RFID systems. Recently, it is demonstrated that quantum key distribution (QKD) can be implemented in a client–server scheme where client only requires an on-chip polarization rotator that may be integrated into a handheld device. Now we present our technique for a tag–reader scenario which needs similar resources as the mentioned QKD scheme. We argue that our technique requires less resources and provides lower probability of false alarm for the system, compared with distance-bounding protocols, and may pave the way to enhance the security of current RFID systems.



Similar content being viewed by others
Notes
Normally Hilbert space is defined with additional conditions which we are not concerned with in this paper.
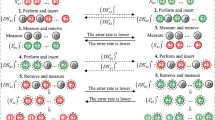
Qubits could be prepared by the reader or a third party resource for the use of tag.
References
Desmedt, Y.: Major security problems with the unforgeable Feige-Fiat-Shamir proofs of identity and how to overcome them. In: Proceedings of the Sixth Worldwide Congress on Computer and Communications Security and Protection, pp. 147–159 (1988)
Issovits, W., Hutter, M.: Weaknesses of the ISO/IEC 14443 protocol regarding relay attacks. In: Proceedings of the IEEE International Conference on RFID Technologies and Applications, pp. 335–342 (2011)
Thevenon, P., Savry, O., Tedjini, S.: On the weakness of contactless systems under relay attacks. In: Proceedings of the Nineteenth IEEE International Conference on Software, Telecommunications and Computer Networks, pp. 1–5 (2011)
Yang, T., Kong, L., Xin, W., Hu, J., Chen, Z.: Resisting relay attacks on vehicular passive keyless entry and start systems. In: Proceedings of the Nineth IEEE International Conference on Fuzzy Systems and Knowledge Discovery, pp. 2232–2236 (2012)
Jannati, H., Falahati, A.: An RFID search protocol secured against relay attack based on distance bounding approach. Wirel. Pers. Commun. 85(3), 711–726 (2015)
Hancke, G.P.: A practical relay attack on ISO 14443 proximity cards. Technical Report 2005-02, University of Cambridge Computer Laboratory, Cambridge (2005)
Miles, S.B., Sarma, S.E., Williams, J.R. (eds.): RFID Technology and Applications. Cambridge University Press, Cambridge (2008)
Brands, S., Chaum, D.: Distance-bounding protocols. In: Proceedings of the Advances in Cryptology (EUROCRYPT’93), vol. 765 of LNCS, pp. 344–359 (1993)
Hancke, G.P., Kuhn, M.: An RFID distance bounding protocol. In: Proceedings of the first International Conference on Security and Privacy for Emergent Areas in Communications Networks (SecureComm’05), pp. 67–73 (2005)
Lee, S., Kim, J.S., Hong, S.J., Kim, J.: Distance bounding with delayed responses. IEEE Commun. Lett. 16(9), 1478–1481 (2012)
Trujillo-Rasua, R., Martin, B., Avoine, G.: Distance bounding facing both mafia and distance frauds. IEEE Trans. Wirel. Commun. 13(10), 5690–5698 (2014)
Jannati, H., Falahati, A.: Analysis of relay, terrorist fraud and distance fraud attacks on RFID systems. Int. J. Crit. Infrastruct. Prot. 11, 51–61 (2015)
Clulow, J., Hancke, G., Kuhn, M., Moore, T.: So near and yet so far: distance bounding attacks in wireless networks. In: Proceedings of the third European Workshop on Security and Privacy in Ad-Hoc and Sensor Networks (ESAS’06), vol. 4357 of LNCS, pp. 83–97, Springer, berlin (2006)
Hancke, G.P.: Design of a secure distance-bounding channel for RFID. J. Netw. Comput. Appl. 34(3), 877–887 (2011)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, pp. 175–179 (1984)
Zhang, P., Aungskunsiri, K., Martyn-Lopez, E., Wabnig, J., Lobino, M., Nock, R.W., Munns, J., Bonneau, D., Jiang, P., Li, H.W., Laing, A., Rarity, J.G., Niskanen, A.O., Thompson, M.G., OBrien, J.L.: Reference frame independent quantum key distribution server with telecom tether for on-chip client. Phys. Rev. Lett. 112(13), 1–5 (2014)
Nielsen, M.A., Chuang, I.L.: Quantum Computation and Quantum Information. Cambridge University Press, Cambridge (2000)
Gisin, N., Fasel, S., Kraus, B., Zbinden, H., Ribordy, G.: Trojan-horse attacks on quantum-key-distribution systems. Physical Review A 73(2) (2006)
Cai, Q.Y.: Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A 351(1), 23–25 (2006)
Sun, Z., Zhang, C., Wang, B., Li, Q., Long, D.: Improvements on multiparty quantum key agreement with single particles. Quantum Inf. Process. 12(11), 3411–3420 (2013)
Lin, J., Hwang, T.: New circular quantum secret sharing for remote agents. Quantum Inf. Process. 12(1), 685–697 (2013)
Lucamarini, M., Choi, I., Ward, M.B., Dynes, J.F., Yuan, Z.L., Shields, A.J.: Practical security bounds against the trojan-horse attack in quantum key distribution. Physical Review X 5(3), (2015)
Mandal, K., Fan, X., Gong, G.: Warbler: A lightweight pseudorandom number generator for EPC C1 Gen2 tags. Workshop on RFID and IoT Security (RFIDSec’12 Asia), Taipei, Taiwan, pp.73–84 (2012)
EPCglobal (2013) EPC Radio-Frequency Identity Protocols Class-1 Gen-2 UHF RFID Protocol for Communications at 860 MHz–960 MHz. http://www.epcglobalinc.org/standards/uhfc1g2
Choi, S.M., Moon, B.H.: Implementation of energy efficient LDPC code for wireless sensor node. In: Proceedings of the International Conference on Communication and Networking, vol. 266 of CCIS, pp. 248–257, Springer, Berlin (2011)
Piyade, B., Zhang, C., Roberts, M.: 16-bit Parallel Input CRC, VLSI Design Project, Department of Electrical and Computer Engineering, Duke University. http://people.ee.duke.edu/sjmorizio/ece261/2008.projects (2008). Accessed 22 Oct (2013)
Gao, L., Ma, M., Shu, Y., Wei, Y.: An ultralightweight RFID authentication protocol with CRC and permutation. J. Netw. Comput. Appl. 41, 37–46 (2014)
Acknowledgments
We thank Elham Kashefi and Anna Pappa for their useful discussions.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Jannati, H., Ardeshir-Larijani, E. Detecting relay attacks on RFID communication systems using quantum bits. Quantum Inf Process 15, 4759–4771 (2016). https://doi.org/10.1007/s11128-016-1418-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-016-1418-5