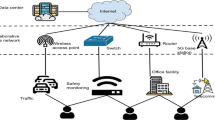
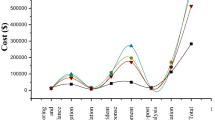
Abstract
The swift advancement of next-generation technologies for wireless communication has led to the cloud computing model becoming a more effective technique of data processing. In addition, cloud computing services are used in edge computing, often referred to as fog computing, to address new IoT challenges. Cloud computing is vulnerable to many infiltration flaws as a result of its Identity Server's shaky connection and dispersed communication features. Since distributed cloud computing systems are widely used, the great majority of research has concentrated on vulnerability scanning and defense. Nevertheless, there is still promise for the creation of fresh intrusion defense and detection methods. As a result, employing an edge computing-based topology of the network, this research proposed a novel hybrid optimal intelligence technique for the detection and authorization of anomalous dangerous behaviors in IoT networks. To discover anomalies in edge computing networks for detecting device behavior, a unique Evolving Neuro-Fuzzy Intelligence for Anomaly Detection (EFNI-AD) method is proposed in this research. Additionally, an Improved Cipher Crypto System (ICCS) is developed to ensure the reliability of data-passing edge devices. The edge device functions as a certification authority (CA) for the specified trusted domain. In this proposed ICCS paradigm, the edge node just verifies the certificate once to eliminate the overhead of edge devices, and once confidence has been established, all communication may be conducted utilizing regional credentials. The Lionized African Buffalo Optimization (LABO) also improves the assault detection system and trust authorization. The simulation findings indicate that the proposed methods outperform the current methods in terms of several performance criteria such as Packet delivery time, End-to-End delay, throughput, Routing overhead, Packet loss, Accuracy, processing time, Packet Delivery Ratio, and Recall. The proposed method provides lower end-to-end delay and a higher packet delivery ratio.

















Similar content being viewed by others
Data availability
Data sharing is not applicable to this article as no new data were created or analyzed in this study.
References
Alfakih, T., et al.: Task offloading and resource allocation for mobile edge computing by deep reinforcement learning based on SARSA. IEEE Access 8, 54074–54084 (2020)
Balamurugan, V., Saravanan, R.: Enhanced intrusion detection and prevention system on cloud environment using hybrid classification and OTS generation. Clust. Comput. 22(6), 13027–13039 (2019)
Bedi, P., et al.: Detection of attacks in IoT sensors networks using machine learning algorithm. Microprocess. Microsyst. 82, 103814 (2021)
Chen, A., Fu, Y., Zheng, X., Lu, G.: An efficient network behavior anomaly detection using a hybrid DBN-LSTM network. Comput. Secur. 114, 102600 (2022)
Dovom, E.M., et al.: Fuzzy pattern tree for edge malware detection and categorization in IoT. J. Syst. Archit. 97, 1–7 (2019)
Ferrer, A.J., Marquès, J.M., Jorba, J.: Towards the decentralised cloud: survey on approaches and challenges for mobile, ad hoc, and edge computing. ACM Comput. Surv. (CSUR) 51(6), 1–36 (2019)
Garg, S., Kaur, K., Kumar, N., Kaddoum, G., Zomaya, A.Y., Ranjan, R.: A hybrid deep learning-based model for anomaly detection in cloud datacenter networks. IEEE Trans. Netw. Serv. Manage. 16(3), 924–935 (2019)
Hasan, M., et al.: Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet of Things 7, 100059 (2019)
Himeur, Y., Ghanem, K., Alsalemi, A., Bensaali, F., Amira, A.: Artificial intelligence based anomaly detection of energy consumption in buildings: a review, current trends and new perspectives. Appl. Energy 287, 116601 (2021)
Hosseinzadeh, M., et al.: A hybrid service selection and composition model for cloud-edge computing in the internet of things. IEEE Access 8, 85939–85949 (2020)
Jeffrey, N., Tan, Q., Villar, J.R.: A review of anomaly detection strategies to detect threats to cyber-physical systems. Electronics 12(15), 3283 (2023)
Kumar, P., Herbert Rav, P., Jelciana, P.: Exploring data security issues and solutions in cloud computing. Procedia Comput. Sci. 125, 691–6972 (2018)
Li, B., et al.: DeepFed: federated deep learning for intrusion detection in industrial cyber-physical systems. IEEE Trans. Ind. Inf. 17(8), 5615–5624 (2020)
Lin, F., et al.: "Fair resource allocation in an intrusion-detection system for edge computing: ensuring the security of Internet of Things devices. IEEE Consumer Electron. Mag. 7(6), 45–50 (2018)
Lin, B., et al.: A time-driven data placement strategy for a scientific workflow combining edge computing and cloud computing. IEEE Trans. Ind. Inf. 15(7), 4254–4265 (2019)
Liu, H., Zhang, Y., Yang, T.: Blockchain-enabled security in electric vehicles cloud and edge computing. IEEE Netw. 32(3), 78–83 (2018)
Liu, P., et al.: Optimization of edge-PLC-based fault diagnosis with random forest in industrial internet of things. IEEE Internet Things J. 7(10), 9664–9674 (2020)
Minh Dang, L., et al.: A survey on internet of things and cloud computing for healthcare. Electronics 8(7), 7684 (2019)
Minu, R.I., Nagarajan, G., Asmaa Munshi, Almukadi, W., Venkatachalam, K., Abouhawwash, M.: An edge based attack detection model (EBAD) for increasing the trustworthiness in IoT enabled smart city environment. IEEE Access 10, 89499–89508 (2022)
Muhammad, G., et al.: Edge computing with cloud for voice disorder assessment and treatment. IEEE Commun. Mag. 56(4), 60–65 (2018)
Pandeeswari, N., Kumar, G.: Anomaly detection system in cloud environment using fuzzy clustering based ANN. Mobile Netw. Appl. 21(3), 494–505 (2016)
Patrikar, Devashree R., and MayurRajramParate. Anomaly detection using edge computing in video surveillance system." arXiv preprint arXiv:2107.02778 (2021).
Peng, Y., et al.: Hierarchical edge computing: a novel multi-source multi-dimensional data anomaly detection scheme for industrial internet of things. IEEE Access 7, 111257–111270 (2019)
Punitha, A., Angel, A., Indumathi, G.: A novel centralized cloud information accountability integrity with ensemble neural network based attack detection approach for cloud data. J. Ambient Intell. Humaniz. Comput. 12(5), 4889–4900 (2021)
Qi, Q., Tao, F.: A smart manufacturing service system based on edge computing, fog computing, and cloud computing. IEEE Access 7, 86769–86777 (2019)
Qureshi, K.N., Jeon, G., Piccialli, F.: Anomaly detection and trust authority in artificial intelligence and cloud computing. Comput. Netw. 184, 107647 (2021)
Rabbani, M., et al.: A hybrid machine learning approach for malicious behaviour detection and recognition in cloud computing. J. Netw. Comput. Appl. 151, 102507 (2020)
Sajith, P.J., Nagarajan, G.: Intrusion detection system using deep belief network & particle swarm optimization. Wireless Pers. Commun. 125(2), 1385–1403 (2022)
Sajith, P.J., Nagarajan, G.: Network intrusion detection system using ANFIS classifier. Soft. Comput. 27(3), 1629–1638 (2023)
Sangaiah, A.K., et al.: Enforcing position-based confidentiality with machine learning paradigm through mobile edge computing in real-time industrial informatics. IEEE Trans. Ind. Inf. 15(7), 4189–4196 (2019)
Sha, K., et al.: A survey of edge computing-based designs for IoT security1. Digital Commun. Netw. 6(2), 195–202 (2020)
Shahzadi, S., et al.: Multi-access edge computing: open issues, challenges and future perspectives. J. Cloud Comput. 6(1), 1–13 (2017)
Singh, S., et al.: Machine learning assisted security and privacy provisioning for edge computing: a survey. IEEE Internet Things J. 9(1), 236–260 (2021)
Somula, R.S., Sasikala, R.: A survey on mobile cloud computing: mobile computing+ cloud computing (MCC= MC+ CC). Scalable Comput. Pract. Exp. 19(4), 309–337 (2018)
Sunyaev, Ali: Cloud computing. In: Internet computing, pp. 195–236. Springer, Cham (2020)
Tan, H., Gui, Z., Chung, I.: A secure and efficient certificateless authentication scheme with unsupervised anomaly detection in VANETs. IEEE Access 6, 74260–74276 (2018)
Varghese, B., RajkumarBuyya: Next generation cloud computing: new trends and research directions. Future Generat. Comput. Syst. 79, 849–861 (2018)
Verma, C, and R Pandey. Mobile cloud computing integrating cloud, mobile computing, and networking services through virtualization. In: Research anthology on architectures, frameworks, and integration strategies for distributed and cloud computing. IGI Global, 2021. 209–226.
Wang, Z.: Research on digital economy and human resources based on fuzzy clustering and edge computing. Secur. Commun. Netw. 2021, 1–8 (2021)
Xiao, Y., et al.: Edge computing security: state of the art and challenges. Proc. IEEE 107(8), 1608–1631 (2019)
Xu, S., Qian, Y., Hu, R.Q.: Data-driven edge intelligence for robust network anomaly detection. IEEE Trans. Netw. Sci. Eng. 7(3), 1481–1492 (2019)
Yazdani, M., Jolai, F.: Lion optimization algorithm (LOA): a nature-inspired metaheuristic algorithm. J. Comput. Design Eng. 3(1), 24–36 (2016)
Zhang, J., et al.: Data security and privacy-preserving in edge computing paradigm: survey and open issues. IEEE Access 6, 18209–18237 (2018)
Author information
Authors and Affiliations
Contributions
Dr. NP: Idea conceptualization, correspondence. Dr. JV: Algorithm specialization A: Validation of the results Dr.SR: Algorithm specialization Dr. NV: Writing original draft SVA: Editing AR: Data collection, validation. Dr. BS: Reviewing
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Human and animal rights
This article does not contain any studies with human or animal subjects performed by any of the authors.
Informed consent
Informed consent does not apply as this was a retrospective review with no identifying patient information.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Prakash, N., Vignesh, J., Ashwin, M. et al. Enabling secure and efficient industry 4.0 transformation through trust-authorized anomaly detection in cloud environments with a hybrid AI approach. Opt Quant Electron 56, 251 (2024). https://doi.org/10.1007/s11082-023-05781-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11082-023-05781-x