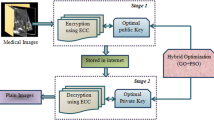
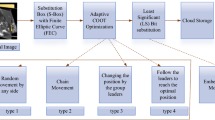
Abstract
In recent years, the Internet of Things (IoT) has grown at an exponential rate, transforming the healthcare business and perhaps leading to the creation of healthcare big data. As a result, there is a requirement to safeguard data from being attacked in order to ensure secure data transfer through the network. Cryptography has been discovered to be a simple and efficient method for safeguarding healthcare big data. At the same time, in cryptography, the best key generation process is viewed as an optimization issue that may be addressed with meta-heuristic algorithms. As a result, the main focus of this research is on the investigation of health care data security in IoT using the ASS-JFO-DHEA model, which combines an innovative hybrid Artificial Shuffle Shepherd Integrated Jellyfish optimization (ASS-JFO) algorithm with Digital Homomorphism Elgamal Algorithm (DHEA) encryption for data security. MATLAB software is used to carry out the execution and experiments for this research. On different benchmark images from a healthcare dataset, the ASS-JFO-DHEA model is experimentally validated. The peak signal to noise ratio, root mean square error, encryption time, mean square error, and other metrics are used to assess the findings.The findings are compared and contrasted as a consequence of this execution, and a variety of encryption algorithms with their optimization techniques from the literature are recognized as having the most intense PSNR values, i.e., 74 dB, generated by the suggested approach.





Similar content being viewed by others
Data and material availability
Data sharing is not applicable to this article as no new data were created or analyzed in this study.
Code availability
Not applicable.
References
Adat, V., Gupta, B.B.: Security in internet of things: issues, challenges, taxonomy, and architecture. Telecommun. Syst.. Syst. 67(3), 423–441 (2018)
Ahmadi, H., et al.: The application of internet of things in healthcare: a systematic literature review and classification. Univ. Access Inf. Soc. 18(4), 837–869 (2019)
Alqaralleh, B.A.Y., et al.: Blockchain-assisted secure image transmission and diagnosis model on internet of medical things environment. In: Personal and Ubiquitous Computing, pp. 1–11 (2021)
Atiewi, S., et al.: Scalable and secure big data IoT system based on multifactor authentication and lightweight cryptography. IEEE Access 8, 113498–113511 (2020)
Balashunmugaraja, B., Ganeshbabu, T.R.: Privacy preservation of cloud data in business application enabled by multi-objective red deer-bird swarm algorithm. Knowl. Based Syst. 236, 107748 (2022)
Calvillo-Arbizu, J., Román-Martínez, I., Reina-Tosina, J.: Internet of things in health: requirements, issues, and gaps. Comput. Methods Prog. Biomed. 208, 106231 (2021)
Denis, R., Madhubala, P.: Hybrid data encryption model integrating multi-objective adaptive genetic algorithm for secure medical data communication over cloud-based healthcare systems. Multimed. Tools Appl. 80(14), 21165–21202 (2021)
Dhanalakshmi, A., Nagarajan, G.: Convolutional neural network-based deblocking filter for SHVC in H. 265. Signal Image Video Proc. 14, 1635–1645 (2020)
Dhawan, S., et al.: SSII: secured and high-quality steganography using intelligent hybrid optimization algorithms for IoT. IEEE Access 9, 87563–87578 (2021)
Elhoseny, M., et al.: A hybrid model of internet of things and cloud computing to manage big data in health services applications. Futur. Gener. Comput. Syst.. Gener. Comput. Syst. 86, 1383–1394 (2018)
Elhoseny, M., et al.: Hybrid optimization with cryptography encryption for medical image security in internet of things. Neural Comput. Appl.Comput. Appl. 32(15), 10979–10993 (2020)
Ghazal, T.M.: Internet of things with artificial intelligence for health care security. Arab. J. Sci. Eng. 1–12 (2021)
Helmi, A.M., ElsayedLotfy, M., Zamel, A.A.: Particle swarm optimization advances in internet of things industry. In: Frontiers in Nature-Inspired Industrial Optimization, pp. 93–110. Springer, Singapore (2022)
Jasim, N.A., Haider, T.H., Rikabi, S.A.L.: Design and implementation of smart city applications based on the internet of things. Int. J. Interact. Mobile Technol. 15(13), 4 (2021)
Jyotheeswari, P., Jeyanthi, N.: Hybrid encryption model for managing the data security in medical internet of things. Int. J. Internet Protoc. Technol. 13(1), 25–31 (2020)
Kalyani, G., Chaudhari, S.: An efficient approach for enhancing security in internet of things using the optimum authentication key. Int. J. Comput. Appl.Comput. Appl. 42(3), 306–314 (2020)
Ku, H., et al.: Privacy-preserving federated learning in medical diagnosis with homomorphic re-encryption. Comput. Stand. Interfaces 80, 103583 (2022)
Kumar, Pr.M., Gandhi, U.D.: Enhanced DTLS with CoAP-based authentication scheme for the internet of things in healthcare application. J. Supercomput. 76(6), 3963–3983 (2020)
Lara-Nino, C.A., Diaz-Perez, A., Morales-Sandoval, M.: Lightweight elliptic curve cryptography accelerator for internet of things applications. Ad Hoc Netw. 103, 102159 (2020)
Lee, C.K.M., et al.: Design and application of Internet of things-based warehouse management system for smart logistics. Int. J. Prod. Res. 56(8), 2753–2768 (2018)
Li, Y., et al.: Deep learning in security of internet of things. IEEE Internet Things J. 9, 22133–22146 (2021)
Mashal, I., et al.: A multi-criteria analysis for an internet of things application recommendation system. Technol. Soc. 60, 101216 (2020)
Nagarajan, G., Minu, R.I.: Wireless soil monitoring sensor for sprinkler irrigation automation system. Wirel. Pers. Commun.. Pers. Commun. 98, 1835–1851 (2018)
Ogundokun, R.O., et al.: Crypto-stegno based model for securing medical information on IOMT platform. Multimed. Tools Appl. 80(21), 31705–31727 (2021)
Pandey, P., Pandey, S.C., Kumar, U.: Security issues of internet of things in health-care sector: an analytical approach. In: Advancement of Machine Intelligence in Interactive Medical Image Analysis, pp. 307–329. Springer, Singapore (2020)
Perwej, Y., et al.: The internet of things (IoT) and its application domains. Int. J. Comput. Appl.Comput. Appl. 975(8887), 182 (2019)
Podder, P., et al.: Review on the security threats of internet of things. arXiv:2101.05614 (2021)
Raghuvanshi, A., et al.: An investigation of various applications and related security challenges of Internet of things. Mater. Today Proc. (2021)
Rana, A., et al.: Internet of medical things-based secure and energy-efficient framework for health care. Big Data 10, 18–33 (2021)
Rani, S.S., et al.: Optimal users based secure data transmission on the internet of healthcare things (IoHT) with lightweight block ciphers. Multimed. Tools Appl. 79(47), 35405–35424 (2020)
Shankar, K.: Improving the security and authentication of the cloud with IoT using hybrid optimization based quantum hash function. J. Intell. Syst. Internet Things 1(2), 61–71 (2021)
Stergiou, C.L., et al.: Secure machine learning scenario from big data in cloud computing via internet of things network. In: Handbook of Computer Networks and Cyber Security, pp. 525–554. Springer, Cham (2020)
Thyagharajan, K.K., Minu, R.I.: Prevalent color extraction and indexing. Int. J. Eng. Technol. 5(6), 4841–4849 (2013)
Tripathi, M.M., et al.: Security in digital healthcare system. In: Pervasive Healthcare, pp. 217–231. Springer, Cham (2022)
Zeadally, S., Das, A.K., Sklavos, N.: Cryptographic technologies and protocol standards for internet of things. Internet Things 14, 100075 (2021)
Zhan, K.: Sports and health big data system based on 5G network and internet of things system. Microprocess. Microsyst.. Microsyst. 80, 103363 (2021)
Zhu, H., et al.: Smart healthcare in the era of internet-of-things. IEEE Consum. Electron. Mag. 8(5), 26–30 (2019)
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
Securing Healthcare Big Data in Industry 4.0: Cryptography Encryption with Hybrid Optimization Algorithm for IoT Applications Chandrashekhar Goswami1 , P. Tamil Selvi2 , Velagapudi Sreenivas3 , J.seetha4 , Ajmeera Kiran5 , Vamsidhar Talasila6 , K.Maithili7 1Department of Computer Science and Engineering, Amity University, Gwalior, India. 2School of Computing Science and Engineering ,Rajalakshmi Engineering College, India. 3 Department of Computer Science and Engineering, Dhanekula Institute of Engineering and Technology Ganguru Vijajayawada, India. 4Department of Computer Science & Engineering, Panimalar Engineering College,India 5 Department of Computer Science & Engineering, MLR Institute of Technology, Dundigal, Hyderabad, Telangana,. India 6Dept.of Computer Science and Engineering, Koneru Lakshmaiah Education Foundation, Vaddeswaram ,India. 7Department of CSE ,KG Reddy College of Engineering and Technology ,Chilukuru village ,Telangana,India chandrashekhargoswami.cse@gmail.com *1 , tamilselvi.p@rajalakshmi.edu.in2 , velagapudisreenivas@gmail.com3 , jsvpec@gmail.com4 , kiranphd.jntuh@gmail.com5 , vamsi@kluniversity.in6 , drmaithili@kgr.ac.in7 Chandrashekhar Goswami : Idea conceptualization, correspondence P.Tamil Selvi : Algorithm specialization Velagapudi Sreenivas :Validation of the results, J.seetha :Writing original draft Ajmeera Kiran : Editing Vamsidhar Talasila :Data collection, validation K.Maithili :Big Data in Industry 4.0 related work & Reviewing .
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Human and animal rights
This article does not contain any studies with human or animal subjects performed by any of the authors.
Informed consent
Informed consent does not apply as this was a retrospective review with no identifying patient information.
Consent to participate
Not applicable.
Consent for publication
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Goswami, C., Tamil Selvi, P., Sreenivas, V. et al. Securing healthcare big data in industry 4.0: cryptography encryption with hybrid optimization algorithm for IoT applications. Opt Quant Electron 56, 366 (2024). https://doi.org/10.1007/s11082-023-05672-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11082-023-05672-1