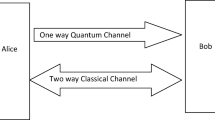
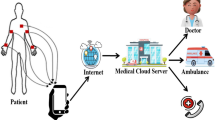
Abstract
Data and information secrecy during storage or transmission has been preserved through the use of cryptography. Consequently, cryptography studies have also progressed from traditional Caesar cipher to the existing cryptographic protocols depending on quantum computing, starting with the latest modular arithmetic-based cryptosystems. The strength of modular arithmetic ciphers lies in the fact that they are computationally difficult to break, but with the advent of quantum computing, even these issues can be cracked with in polynomial time. Research on post-quantum cryptography began in response to this danger, with the goal of creating post-quantum algorithms that are immune to quantum computing. However, cryptographic methods confront a number of other problems, including, but not limited to, availability, integrity, and vulnerability. Despite the researchers’ successes, security is still a major issue for Quantum Computing. Because of its many advantages, cyberspace has quickly become the most common medium for disseminating information. Because of the exponential growth of science and technology, notably quantum computers, cyber security is now the top priority for the Internet and other wireless systems. The fundamental goal of this work is to create a Hybrid Quantum Cryptosystem that can be implemented in Wireless Body Sensor Networks. Using a series of comparisons with existing algorithms, we will determine how well our suggested hybrid algorithm operates in terms of key length, key generation time, decryption and encryption timings, and overall speed. The proposed approach attains 10.3 minimal rate of error, which outperforms the existing state-of-art techniques.








Similar content being viewed by others
Data availability
Data available on request from the authors.
References
Abushgra, A.A., Elleithy, K.M.: A shared secret key initiated by EPR authentication and qubit transmission channels. IEEE Access 5, 17753–17763 (2017)
Almuhaideb, A.M.: Re-AuTh: lightweight Re-authentication with practical key management for wireless body area networks. Arab. J. Sci. Eng. 46(9), 8189–8202 (2021)
Alzahrani, B.A., Irshad, A., Albeshri, A., Alsubhi, K.: A provably secure and lightweight patient-healthcare authentication protocol in wireless body area networks. Wirel. Pers. Commun. 117(1), 47–69 (2021)
Awotunde, J.B., Jimoh, R.G., Folorunso, S.O., Adeniyi, E.A., Abiodun, K.M., Banjo, O.O.: Privacy and security concerns in IoT-based healthcare systems. In: The Fusion of Internet of Things, Artificial Intelligence, and Cloud Computing in Health Care, pp. 105–134. Springer, Cham (2021)
Azees, M., Vijayakumar, P., Karuppiah, M., Nayyar, A.: An efficient anonymous authentication and confidentiality preservation schemes for secure communications in wireless body area networks. Wirel. Netw. 27(3), 2119–2130 (2021)
Benioff, P.: The computer as a physical system: a microscopic quantum mechanical Hamiltonian model of computers as represented by Turing machines. J. Stat. Phys. 22, 563–591 (1980)
Bindel, N., Herath, U., McKague, M., Stebila, D.: Transitioning to a quantum-resistant public key infrastructure. In: Lange, T., Takagi, T. (eds.) Post-Quantum Cryptography, pp. 384–405. Springer, Cham (2017)
Bindel, N., Brendel, J., Fischlin, M., Goncalves, B., Stebila, D.: Hybrid key encapsulation mechanisms and authenticated key exchange. In: Ding, J., Steinwandt, R. (eds.) Post-Quantum Cryptography, pp. 206–226. Springer, Cham (2019)
Braithwaite, M.: Google security blog: experimenting with post-quantum cryptography. (2016)
Chaudhary, S., Singh, A., Chatterjee, K.: Wireless Body Sensor Network (WBSN) Security and Privacy Issues: A Survey (March 19, 2019). Int. J. Comput. Int. IoT, 2(2), (2019) Available at SSRN: https://ssrn.com/abstract=3355560
Chen, Z., Zhou, K., Liao, Q.: Quantum identity authentication scheme of vehicular ad-hoc networks. Int. J. Theor. Phys. 58(1), 40–57 (2019)
Chunka, C., Banerjee, S.: An efficient mutual authentication and symmetric key agreement scheme for wireless body area network. Arab. J. Sci. Eng. 46(9), 8457–8473 (2021)
Denis, R., Madhubala, P.: Hybrid data encryption model integrating multi-objective adaptive genetic algorithm for secure medical data communication over cloud-based healthcare systems. Multimed. Tools Appl. 80(14), 21165–21202 (2021)
Deutsch, D.: Quantum theory, the church-turing principle and the universal quantum computer. Proc. R. Soc. Lond. A400, 97–117 (1985)
Dodis, Y., Katz, J.: Chosen-ciphertext security of multiple encryption. In: Kilian, J. (ed.) Theory of Cryptography, pp. 188–209. Springer, Berlin (2015)
Feynman, R.P.U.: Simulating physics with computers. Int. J. Theor. Phys. 21, 467–488 (1982)
Gautam, A.K., Kumar, R.: A comprehensive study on key management, authentication and trust management techniques in wireless sensor networks. SN Appl. Sci. 3(1), 393 (2021)
Ghosh, C., Parag, A., Datta, S.: Different vulnerabilities and challenges of quantum key distribution protocol: a review’. Int. J. Adv. Res. Comput. Sci. 8(8), 307–311 (2017)
Giacon, F., Heuer, F., Poettering, B.: KEM combiners. In: Abdalla, M., Dahab, R. (eds.) Public-Key Cryptography—PKC 2018, pp. 190–218. Springer, Cham (2018)
Hajar, M.S., Al-Kadri, M.O., Kalutarage, H.K.: A survey on wireless body area networks: architecture, security challenges and research opportunities. Comput. Secur. 104, 102211 (2021)
Harnik, D., Kilian, J., Naor, M., Reingold, O., Rosen, A.: On robust combiners for oblivious transfer and other primitives. In: Advances in Cryptology—EUROCRYPT 2005, pp. 96–113. Springer, Berlin (2015)
Herzberg, A.: Folklore, practice and theory of robust combiners. J. Comput. Secur. 17, 159–189 (2019)
Hohenberger, S., Lewko, A., Waters, B.: Detecting dangerous queries: a new approach for chosen ciphertext security. In: Pointcheval, D., Johansson, T. (eds.) Advances in Cryptology—EUROCRYPT 2012, pp. 663–681. Springer, Berlin (2018)
Hussain, S.J., Irfan, M., Jhanjhi, N.Z., Hussain, K., Humayun, M.: Performance enhancement in wireless body area networks with secure communication. Wirel. Pers. Commun. 116(1), 1–22 (2021)
Iqbal, J., Umar, A.I., Amin, N., Waheed, A.: Efficient and secure attribute-based heterogeneous online/offline signcryption for body sensor networks based on blockchain. Int. J. Distrib. Sens. Netw. 15(9), 1550147719875654 (2019)
Iqbal, J., Waheed, A., Zareei, M., et al.: A lightweight and secure attribute-based multi receiver generalized signcryption scheme for body sensor networks. IEEE Access 8, 200283–200304 (2020)
Jan, S.U., Ali, S., Abbasi, I.A., Mosleh, M.A., Alsanad, A., Khattak, H.: Secure patient authentication framework in the healthcare system using wireless medical sensor networks. J. Healthc. Eng. 2021, 9954089 (2021)
Jao, D., Feo, L.D.: Towards quantum-resistant cryptosystems from super singular elliptic curve isogenies. Pqcrypto 7071, 19–34 (2021)
Kampanakis, P., Panburana, P., Daw, E., Van Geest, D.: The viability of post-quantum X.509 certificates. In: IACR Cryptology ePrint Archive, Report 2018/063. (2018)
Karunarathne, S.M., Saxena, N., Khan, M.K.: Security and privacy in IoT smart healthcare. IEEE Internet Comput. 25(4), 37–48 (2021)
Khan, M.A.R., Shavkatovich, S.N., Nagpal, B., Kumar, A., Haq, M.A., Tharini, V.J., Alazzam, M.B.: Optimizing hybrid metaheuristic algorithm with cluster head to improve performance metrics on the IoT. Theor. Comput. Sci. 927, 87–97 (2022)
Kuwakado, H., Morii, M.: Quantum distinguished between the 3-round Feistel cipher and the random permutation. In: Proceedings of the IEEE International Symposium on Information Theory, Austin, TX, USA, 12–18 June 2019; pp. 2682–2685
Langley, A.: Intent to implement and ship: CECPQ1 for TLS. Google Group. (2016)
Lu, C., Miao, F., Meng, K., Yu, Y.: Threshold quantum secret sharing based on single qubit. Quantum Inf. Process. 17(3), 1–13 (2018)
Manin, Y.: Mathematics and Physics. American Mathematical Society, Providence (1981)
McEliece, R.J.: A public-key cryptosystem based on algebraic. Coding Thv 4244, 114–116 (1978)
Merkle, R.: Secrecy, Authentication, and Public Key Systems; Computer Science Series. UMI Research Press, Ann Arbor (2018)
Miri, J., Nsiri, B., Bouallegue, R.: Certificateless based quantum cryptosystem for ad-hoc UWB-IR. Wirel. Pers. Commun. 114(2), 1805–1823 (2020)
Narwal, B., Mohapatra, A.K.: SAMAKA: secure and anonymous mutual authentication and key agreement scheme for wireless body area networks. Arab. J. Sci. Eng. 46(9), 9197–9219 (2021)
Naveen Kumar, K., Raj Kumar, G.V.S., Praveen Kumar, K.T., Chandra Sekhar, P.: Bitwise operations-based encryption and decryption. Int. J. Comput. Sci. Eng. 3(1), 50–54 (2019)
Nidhya, R., Shanthi, S., Kumar, M.: A novel encryption design for wireless body area network in remote healthcare system using enhanced RSA algorithm. Intell. Syst. Design 1171, 255–263 (2021)
Nielsen, M.A., Chuang, I.: Quantum Computation and Quantum Information. Cambridge University Press, Cambridge (2022)
Qazi, R., Qureshi, K.N., Bashir, F., Islam, N.U., Iqbal, S., et al.: Security protocol using elliptic curve cryptography algorithm for wireless sensor networks. J. Ambient. Intell. Humaniz. Comput. 12(1), 547–566 (2021)
Regev, O.: On lattices, learning with errors, random linear codes, and cryptography. JACM 56, 34 (2019)
Rivest, R., Shamir, A., Adleman, L.: A method for obtaining digital for signatures and public-Key cryptosystems. Commun. ACM 1978(21), 120–126 (2014)
Sandeep, V., Niranjan, A.: Implementation of a modified BB84 algorithm for secure key exchange in a normal network. Int. J. Eng. Res. Technol. 2(14), 48–50 (2021)
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26, 1484–1509 (1997)
Singh, A., Chaudhary, R.R.K., Chatterjee, K.: A novel privacy preservation mechanism for wireless medical sensor networks. Adv. Electron. Commun. Comput. 709, 173–182 (2021)
Sivasangari, A., Ananthi, A., Deepa, D., Rajesh, G., Raajini, X.M.: Security and privacy in wireless body sensor networks using lightweight cryptography scheme. Secur. Priv. Issues IoT Devices Sens. Netw. 3, 43–59 (2021)
Soni, M., Singh, D.K.: LAKA: lightweight Authentication and key agreement protocol for internet of things based wireless body area network. Wirel. Pers. Commun. 127(2), 1067–1084 (2021)
Tharini, V.J., Shivakumar, B.L.: An efficient pruned matrix aided utility tree for high utility itemset mining from transactional database. Int. J. Intell. Syst. Appl. Eng. 11(4s), 46–55 (2023)
Tharini, V.J., Vijayarani, S.: IoT in healthcare: ecosystem, pillars, design challenges, applications, vulnerabilities, privacy, and security concerns. In: Incorporating the Internet of Things in healthcare applications and wearable devices, pp. 1–22. IGI Global, Hershey (2020)
Wan, T., Wang, L., Liao, W., Yue, S.: A lightweight continuous authentication scheme for medical wireless body area networks. Peer-to-Peer Netw. Appl. 14(6), 3473–3487 (2021)
Yan, S.Y.: Integer Factorization and Discrete Logarithms Primality Testing and Integer Factorization in Public-Key Cryptography, pp. 139–191. Springer, Berlin (2004)
Yang, W., Wang, S.: A privacy-preserving ECG-based authentication system for securing wireless body sensor networks. IEEE Internet Things J. 9(8), 6148–6158 (2021)
Zhang, C., Cash, D., Wang, X., Yu, X., Chow, S.S.M.: Combiners for chosen-ciphertext security. In: Dinh, T.N., Thai, M.T. (eds.) Computing and Combinatorics, pp. 257–268. Springer, Cham (2016)
Acknowledgements
No acknowledgement
Funding
No funding is involved in this work.
Author information
Authors and Affiliations
Contributions
Conceptualization, Methodology, Software,Writing- Reviewing and Editing: GOVINDU SURLA & Dr. R. LAKSHMI
Corresponding author
Ethics declarations
Conflict of interest
Conflict of Interest is not applicable in this work.
Consent to participate
No participation of humans takes place in this implementation process.
Human and animal rights
No violation of Human and Animal Rights is involved.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Surla, G., Lakshmi, R. Design and evaluation of novel hybrid quantum resistant cryptographic system for enhancing security in wireless body sensor networks. Opt Quant Electron 55, 1252 (2023). https://doi.org/10.1007/s11082-023-05518-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11082-023-05518-w