Abstract
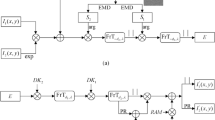
In this paper, the security of an optical cryptosystem based on interference and equal modulus decomposition (EMD) has been evaluated. The security strength of the asymmetric cryptosystem has been enhanced by combining interference and EMD to generate four phase-only masks (POMs). Compared to the previous interference- or EMD-based cryptosystems where only one POM is the private key, the number of private keys in this system increases (i.e., four POMs) consequently increasing the key space of the cryptosystem. Moreover, due to additional private keys as unknown parameters in iterative procedures, this cryptosystem with silhouette removal is immune to special attacks which the EMD-based cryptosystems are vulnerable to. It seems that the security strength of the optical cryptosystem based on interference and EMD has been improved; however, we have noticed that the two POMs used as private key are still related to the ciphertexts and can be potentially utilized to attack the cryptosystem. According to the POMs generation principle, a relationship between private keys and ciphertexts could be derived and used as additional constraints to investigate the iterative attacks. Based on this finding, new iterative ciphertext-only attacks with different constraints have been proposed to crack the cryptosystem. In addition, we found that the POMs \(P_2(u,v)\) and \(P_4(u,v)\) which are used as private keys have low key sensitivity, which may lead to information leak. Numerical simulations have been carried out to validate the feasibility and effectiveness of the proposed attacks.









Similar content being viewed by others
References
Abuturab, M.R.: Color image security system using double random-structured phase encoding in gyrator transform domain. Appl. Opt. 51(15), 3006–3016 (2012)
Cai, J., Shen, X., Lei, M., Lin, C., Dou, S.: Asymmetric optical cryptosystem based on coherent superposition and equal modulus decomposition. Opt. Lett. 40, 475–478 (2015)
Chen, W., Chen, X.: Iterative phase retrieval for simultaneously generating two phase-only masks with silhouette removal in the interference-based optical encryption. Opt. Commun. 331, 133–138 (2014)
Chen, W., Javidi, B., Chen, X.: Advances in optical security systems. Adv. Opt. Photon. 6(2), 120–155 (2014)
Chen, H., Liu, Z., Zhu, L., Tanougast, C., Blondel, W.: Asymmetric color cryptosystem using chaotic Ushiki map and equal modulus decomposition in fractional Fourier transform domains. Opt. Lasers Eng. 112, 7–15 (2019)
Deng, X.: Asymmetric optical cryptosystem based on coherent superposition and equal modulus decomposition: comment. Opt. Lett. 40(16), 3913 (2015)
Hai, H., Pan, S., Liao, M., Lu, D., He, W., Peng, X.: Cryptanalysis of random-phase-encoding-based optical cryptosystem via deep learning. Opt. Express 27(15), 21204–21213 (2019)
Javidi, B., et al.: Roadmap on optical security. J. Opt. 18(8), 083001 (2016)
Kumar, P., Joseph, J., Singh, K.: Optical image encryption based on interference under convergent random illumination. J. Opt. 12(9), 095402 (2010)
Liu, Z., Guo, Q., Xu, L., Ahmad, M.A., Liu, S.: Double image encryption by using iterative random binary encoding in gyrator domain. Opt. Express 18(11), 12033–12043 (2010)
Liu, L., Shan, M., Zhong, Z., Liu, B.: Multiple-image encryption and authentication based on optical interference by sparsification and space multiplexing. Opt. Laser Technol. 122, 105858 (2020)
Li, J., Li, J., Shen, L., Pan, Y., Li, R.: Optical image encryption and hiding based on a modified Mach-Zehnder interferometer. Opt. Express 22(4), 4849–4860 (2014)
Li, G., Yang, W., Li, D., Situ, G.: Ciphertext-only attack on double random-phase encryption: experimental demonstration. Opt. Express 25(8), 8690–8697 (2017)
Luan, G., Li, A., Chen, Z., Huang, C.: Asymmetric optical image encryption with silhouette removal using interference and equal modulus decomposition. IEEE Photonics J. 12(2), 1–8 (2020)
Peng, X., Wei, H., Zhang, P.: Chosen-plaintext attack on lensless double-random phase encoding in the Fresnel domain. Opt. Lett. 31(22), 3261–3263 (2006a)
Peng, X., Zhang, P., Wei, H.: Known-plaintext attack on optical encryption based on double random phase keys. Opt. Lett. 31(8), 1044–1046 (2006b)
Qin, W., Peng, X.: Asymmetric cryptosystem based on phase-truncated Fourier transforms. Opt. Lett. 35(2), 118–120 (2010)
Refregier, P., Javidi, B.: Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 20(7), 767–769 (1995)
Situ, G., Zhang, J.: Double random-phase encoding in the Fresnel domain. Opt. Lett. 29(14), 1584–1586 (2004)
Unnikrishnan, G., Joseph, J., Singh, K.: Optical encryption by double-random phase encoding in the fractional Fourier domain. Opt. Lett. 2512, 887–889 (2000)
Wang, Y., Quan, C., Tay, C.J.: Asymmetric optical image encryption based on an improved amplitude-phase retrieval algorithm. Opt. Lasers Eng. 78, 8–16 (2016a)
Wang, Y., Quan, C., Tay, C.J.: New method of attack and security enhancement on an asymmetric cryptosystem based on equal modulus decomposition. Appl. Opt. 55(4), 679–689 (2016a)
Wang, W., Wang, X., Xu, B., Chen, J.: Optical image encryption and authentication using phase-only computer-generated hologram. Opt. Lasers Eng. 146, 106722 (2021)
Wei, H., Wang, X.: Optical multiple-image authentication and encryption based on phase retrieval and interference with sparsity constraints. Opt. Laser Technol. 142, 107257 (2021)
Weng, D., Zhu, N., Wang, Y., Xie, J., Liu, J.: Experimental verification of optical image encryption based on interference. Opt. Commun. 284(10–11), 2485–2487 (2011)
Xiong, Y., Quan, C., Tay, C.J.: Multiple image encryption scheme based on pixel exchange operation and vector decomposition. Opt. Lasers Eng. 101, 113–121 (2018a)
Xiong, Y., He, A., Quan, C.: Specific attack and security enhancement to optical image cryptosystem based on two random masks and interference. Opt. Lasers Eng. 107, 142–148 (2018b)
Xiong, Y., He, A., Quan, C.: Cryptoanalysis on optical image encryption systems based on vector decomposition technique in the Fourier domain. Appl. Opt. 58(12), 3301–3309 (2019)
Xiong, Y., Du, J., Quan, C.: Security analysis on optical image hiding with silhouette removal based on the interference. Opt. Lasers Eng. 142, 106612 (2021)
Zhang, Y., Wang, B.: Optical image encryption based on interference. Opt. Lett. 33(21), 2443–2445 (2008)
Zhang, L., Zhou, Y., Huo, D., Li, J., Zhou, X.: Multiple-image encryption based on double random phase encoding and compressive sensing by using a measurement array preprocessed with orthogonal-basis matrices. Opt. Laser Technol. 105, 162–170 (2018)
Zhong, Z., Qin, H., Liu, L., Zhang, Y., Shan, M.: Silhouette-free image encryption using interference in the multiple-parameter fractional Fourier transform domain. Opt. Express 25(6), 6974–6982 (2017)
Acknowledgements
The authors acknowledge the financial support provided by the Fundamental Research Funds for the Central Universities (JUSRP121051) and Jiangsu Entrepreneurship and Innovation Talent Program (JSSCBS20210844).
Funding
Funding support from Fundamental Research Funds for the Central Universities (JUSRP121051) and Jiangsu Entrepreneurship and Innovation Talent Program (JSSCBS20210844).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Xiong, Y., Kumar, R. Security analysis on asymmetric optical cryptosystem based on interference and equal modulus decomposition. Opt Quant Electron 54, 507 (2022). https://doi.org/10.1007/s11082-022-03918-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11082-022-03918-y