Abstract
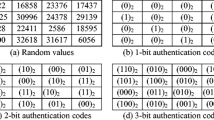
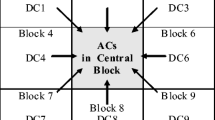
In this paper, we propose a method for image recovery based on Discrete Cosine Transform (DCT) and finding the best matched blocks by using a part of the fractal compression algorithm. At the same time, we propose a new check algorithm for checking if image blocks are tampered. First, the original image is divided into small blocks. The best matched block of each small block is searched in a particular way. Then the matching information is embedded as backup into other blocks. For the ones that fail to find the best matched blocks, DCT is applied on them and then quantized to be the backup. In order to prevent the backup of the tampered blocks from damaging, we generate 3 backups for each block and embed them into different quadrants. On the receiving side, the tampering check bits are extracted to localize the tampered areas, and the backup bits are used to restore the contents of the tampered regions. The experimental results have proved a good restorability of this algorithm, and the lower the tampering rate is, the better quality of restored content can be obtained.











Similar content being viewed by others
References
Xiang, S., Kim, H.J., Huang, J.: Invariant image watermarking based on statistical features in the low-frequency domain. IEEE Trans. Circuits Syst. Video Technol. 18(6), 777–790 (2008)
Farschi, S.M.R., Farschi, H.: A novel chaotic approach for information hiding in image. Nonlinear Dyn. 69(4), 1525–1539 (2012)
Run, R.S., Hong, S.J., Lai, J.L., Kao, T.W., Chen, R.J.: An improved SVD-based watermarking technique for copyright protection. Expert Syst. Appl. 39(1), 673–689 (2012)
Cancellaro, M., Battisti, F., Carli, M., Boato, G., Natale, F.G.B.D.: A commutative digital image watermarking and encryption method in the tree structured Haar transform domain. Signal Process. Image Commun. 26(1), 1–12 (2011)
Chang, C.Y., Wang, H.J., Su, S.J.: Copyright authentication for images with a full counter-propagation neural network. Expert Syst. Appl. 37(12), 7639–7647 (2010)
Hsieh, S.L., Tsai, I.J., Yeh, C.P., Chang, C.M.: An image authentication scheme based on digital watermarking and image secret sharing. Multimed. Tools Appl. 52(2–3), 597–619 (2011)
Li, C.L., Wang, Y.H., Ma, B., Zhang, Z.X.: A novel self-recovery fragile watermarking scheme based on dual-redundant-ring structure. Comput. Electr. Eng. 37(6), 927–940 (2011)
Lin, Z.C., He, J.F., Tang, X.O., Tang, C.K.: Fast, automatic and fine-grained tampered JPEG image detection via DCT coefficient analysis. Pattern Recognit. 42(11), 2492–2501 (2009)
Cao, Y.J., Gao, T.G., Fan, L., Yang, Q.T.: A robust detection algorithm for copy-move forgery in digital images. Forensic Sci. Int. 214(1–3), 33–43 (2011)
Qi, X.J., Xin, X.: A quantization-based semi-fragile watermarking scheme for image content authentication. J. Vis. Commun. Image Represent. 22(2), 187–200 (2011)
Peng, F., Guo, R.S., Li, C.T., Long, M.: A semi-fragile watermarking algorithm for authenticating 2D CAD engineering graphics based on log-polar transformation. Comput. Aided Des. 42(12), 1207–1216 (2010)
Zhu, X.Z., Ho, A.T.S., Marziliano, P.: A new semi-fragile image watermarking with robust tampering restoration using irregular sampling. Signal Process. Image Commun. 22(5), 515–528 (2007)
Fridrich, J., Goljan, M.: Images with self-correcting capabilities. In: 99th International Conference on Image Processing (ICIP), vol. 3, pp. 792–796 (1999)
Zhang, X.P., Wang, S.Z., Qian, Z.X., Feng, G.R.: Reference sharing mechanism for watermark self-embedding. IEEE Trans. Image Process. 20(2), 485–495 (2011)
Qian, Z.X., Feng, G.R., Zhang, X.P., Wang, S.Z.: Image self-embedding with high-quality restoration capability. Digit. Signal Process. 21(2), 278–286 (2011)
Bravo-Solorio, S., Nandi, A.K.: Secure fragile watermarking method for image authentication with improved tampering localization and self-recovery capabilities. Signal Process. 91(4), 728–739 (2011)
Mirzaei, O., Yaghoobi, M., Irani, H.: A new image encryption method: sub-image encryption with hyper chaos. Nonlinear Dyn. 67(1), 557–566 (2012)
Wang, X.Y., Teng, L.: An image blocks encryption algorithm based on spatiotemporal chaos. Nonlinear Dyn. 67(1), 365–371 (2012)
Liu, S.H., Yao, H.X., Gao, W., Liu, Y.L.: An image fragile watermark scheme based on chaotic image pattern and pixel-pairs. Appl. Math. Comput. 185(2), 869–882 (2007)
Zhang, X.P., Wang, S.Z., Qian, Z.X., Feng, G.R.: Self-embedding watermark with flexible restoration quality. Multimed. Tools Appl. 54(2), 385–395 (2011)
Chang, C.C., Chen, K.N., Lee, C.F., Liu, L.J.: A secure fragile watermarking scheme based on chaos-and-hamming code. J. Syst. Softw. 84(9), 1462–1470 (2011)
Chen, W.C., Wang, M.S.: A fuzzy c-means clustering-based fragile watermarking scheme for image authentication. Expert Syst. Appl. 36(2), 1300–1307 (2009)
Zhang, X.P., Wang, S.Z.: Fragile watermarking with error-free restoration capability. IEEE Trans. Multimed. 10(8), 1490–1499 (2008)
Liu, Y.J., Zheng, Y.Q.: Adaptive robust fuzzy control for a class of uncertain chaotic systems. Nonlinear Dyn. 57(3), 431–439 (2009)
Liu, Y.J., Chen, C.L.P., Wen, G.X., Tong, S.C.: Adaptive neural output feedback tracking control for a class of uncertain discrete-time nonlinear systems. IEEE Trans. Neural Netw. 22(7), 1162–1167 (2011)
Hernandez-Avalos, P.A., Feregrino-Uribe, C., Cumplido, R.: Watermarking using similarities based on fractal codification. Digit. Signal Process. 22(2), 324–336 (2012)
Kiani, S., Moghaddam, M.E.: A multi-purpose digital image watermarking using fractal block coding. J. Syst. Softw. 84(9), 1550–1562 (2011)
Liu, Y.J., Wang, W., Tong, S.C., Liu, Y.S.: Robust adaptive tracking control for nonlinear systems based on bounds of fuzzy approximation parameters. IEEE Trans. Syst. Man Cybern., Part A 40(1), 170–184 (2010)
Liu, Y.J., Wang, W.: Adaptive fuzzy control for a class of uncertain nonaffine nonlinear systems. Inf. Sci. 177(18), 3901–3917 (2007)
Liu, Y.J., Tong, S.C., Chen, C.L.P.: Adaptive fuzzy control via observer design for uncertain nonlinear systems with unmodeled dynamics. IEEE Trans. Fuzzy Syst. 21(2), 275–288 (2013)
Zhang, T., Zhuang, Z.: Representation of discrete sequences with high-dimensional iterated function systems. Nonlinear Dyn. 48(1–2), 49–57 (2007)
Zhang, T., Liu, J.L., Zhuang, Z.: Representation of discrete sequences with N-dimensional iterated function systems in tensor form. Nonlinear Dyn. 52(1–2), 89–93 (2008)
He, H.J., Zhang, J.S., Chen, F.: Adjacent-block based statistical detection method for self-embedding watermarking techniques. Signal Process. 89(8), 1557–1566 (2009)
Acknowledgements
This research is supported by the National Natural Science Foundation of China (Nos. 61173183, 60973152, and 60573172), the Doctoral Program Foundation of Institution of Higher Education of China (No. 20070141014), Program for Liaoning Excellent Talents in University (No. LR2012003), the National Natural Science Foundation of Liaoning Province (No. 20082165), and the Fundamental Research Funds for the Central Universities (No. DUT12JB06).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wang, X., Zhang, D. & Guo, X. A novel image recovery method based on discrete cosine transform and matched blocks. Nonlinear Dyn 73, 1945–1954 (2013). https://doi.org/10.1007/s11071-013-0915-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-013-0915-7