Abstract
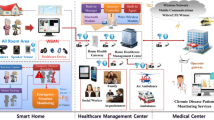
The Internet of Things has opened up new opportunities in healthcare systems. Wireless sensor nodes are used to collect and exchange health-related data in the Internet of Things. In this integration, data is transmitted to medical professionals through unsecured channels to enable them to monitor patients’ conditions in real-time. However, due to the high sensitivity of e-health records, there are key challenges such as security considerations, privacy, and authentication in data transmission in heterogeneous Internet of Things networks. This article examines the solution proposed by Masud and colleagues and points out the existing threats and vulnerabilities, such as node clone/replication attacks. To overcome these drawbacks, we propose an improved lightweight authentication protocol for a smart healthcare system. In the proposed protocol, the mutual authentication process consists of two steps. The doctor sends their information for authentication and the desired sensor node ID to the gateway for communication. After successful confirmation of authentication, the gateway node, in turn, sends a message to the sensor node to complete the authentication process. After confirming the authentication process, the node sends a message to the gateway to complete the authentication process and key agreement. Once the authentication process of the sensor node is confirmed, the gateway sends a message to the medical user based on their authentication along with the session key. The security of the proposed protocol is demonstrated through automatic validation of protocols using tools like ProVerif and internet security programs. Additionally, security features and performance analysis are compared to other schemes. The results show that the improved proposed protocol provides a higher level of security while ensuring computational and communication efficiency. It is also resistant to attacks such as mutual authentication, identity anonymity and untraceability, ensures data privacy, and provides perfect forward secrecy, among others.





Similar content being viewed by others
Data Availability
The data of this paper is the result of simulation and all the data are presented in the form of graphs inside the paper. There is no private data in this article.
References
Puri V, Kataria A, Sharma V (2021) Artificial intelligence-powered decentralized framework for internet of things in healthcare 4.0. Transactions on Emerging Telecommunications Technologies, pp 42–45
Ataei Nezhad M, Barati H, Barati A (2022) An authentication-based secure data aggregation method in internet of things. J Grid Comput 20(3):29
Ahmadi Z, Haghi Kashani M, Nikravan M, Mahdipour E (2021) Fog-based healthcare systems: A systematic review. Multimed Tools Appl 80:36361–36400
Ali G, Dastgir A, Iqbal MW, Anwar M, Faheem M (2023) A hybrid convolutional neural network model for automatic diabetic retinopathy classification from fundus images. IEEE Journal of Translational Engineering in Health and Medicine
Abbas A, Alroobaea R, Krichen M, Rubaiee S, Vimal S, Almansour FM (2021) Blockchain-assisted secured data management framework for health information analysis based on internet of medical things. Personal and Ubiquitous Computing, pp 1–14
Yaghoubi M, Ahmed KH, Miao Y (2022) Wireless body area network (WBAN): a survey on architecture, technologies, energy consumption, and security challenges. Journal of Sensor and Actuator Networks. https://doi.org/10.3390/jsan11040067
Faheem M, Butt RA, Raza B, Alquhayz H, Abbas MZ, Ngadi MA, Gungor VC (2019) A multiobjective, lion mating optimization inspired routing protocol for wireless body area sensor network based healthcare applications. Sensors 19(23):5072
Narwal B, Mohapatra AK (2021) A survey on security and authentication in wireless body area networks. J Syst Archit 113:101883
Deebak BD, Al-Turjman F (2021) Secure-user sign-in authentication for IoT-based eHealth systems. Complex & Intelligent Systems, pp 1–21
Huang J, Wu X, Huang W, Wu X (2021) Design of a data management system for medical internet of things based on mobile platform. Journal of Ambient Intelligence and Humanized Computing, pp 1–13
Dubovitskaya A, Baig F, Xu Z, Shukla R, Zambani PS, Swaminathan A, Wang F (2020) ACTION-EHR: patient-centric blockchain-based electronic health record data management for cancer care. J Med Internet Res 22(8):e13598
Alarood AA, Faheem M, Al-Khasawneh MA, Alzahrani AI, Alshdadi AA (2023) Secure medical image transmission using deep neural network in e-health applications. Healthc Technol Lett 10(4):87–98
Soni M, Singh DK (2022) LAKA: lightweight authentication and key agreement protocol for internet of things based wireless body area network. Wireless Personal Communications. https://doi.org/10.1007/s11277-021-08565-2
Fotouhi M, Bayat M, Das AK, Far HAN, Pournaghi SM, Doostari MA (2020) A lightweight and secure two-factor authentication scheme for wireless body area networks in health-care IoT. Comput Netw 177:107333
Abdi Nasib Far H, Bayat M, Kumar Das A, Fotouhi M, Pournaghi SM, Doostari MA (2021) LAPTAS: lightweight anonymous privacy-preserving three-factor authentication scheme for WSN-based IIoT. Wireless Netw 27(2):1389–1412
Caruccio L, Desiato D, Polese G, Tortora G, Zannone N (2022) A decision-support framework for data anonymization with application to machine learning processes. Inf Sci 613:1–32
Masud M, Gaba GS, Choudhary K, Hossain MS, Alhamid MF, Muhammad G (2021) Lightweight and anonymity-preserving user authentication scheme for IoT-based healthcare. IEEE Internet of Things Journal
Yuanbing W, Wanrong L, Bin L (2021) An improved authentication protocol for smart healthcare system using wireless medical sensor network. IEEE Access
Masud M, Gaba GS, Choudhary K, Alroobaea R, Hossain MS (2021) A robust and lightweight secure access scheme for cloud based E-healthcare services. Peer Peer Netw Appl 14(5):3043–3057
Kamil IA, Ogundoyin SO (2021) A lightweight mutual authentication and key agreement protocol for remote surgery application in tactile internet environment. Comput Commun 170:1–18
Lee TF, Chen WY (2021) Lightweight fog computing-based authentication protocols using physically unclonable functions for internet of medical things. J Inf Secur Appl 59:102817
Ghafouri-Mirsaraei AH, Barati A, Barati H (2022) Asecure three-factor authentication scheme for IoT environments. J Parallel and Distr Comput 169:87–105
Ray PP, Chowhan B, Kumar N, Almogren A (2021) Biothr: electronic health record servicing scheme in IoT-blockchain ecosystem. IEEE Internet Things J 8(13):10857–10872
Zaabar B, Cheikhrouhou O, Jamil F, Ammi M, Abid M (2021) HealthBlock: A secure blockchain-based healthcare data management system. Comput Netw 200:108500
Kumar R, Tripathi R (2021) Towards design and implementation of security and privacy framework for internet of medical things (iomt) by leveraging blockchain and ipfs technology. J Supercomput 77(8):7916–7955
Abbasinezhad-Mood D, Nikooghadam M (2018) Efficient design of a novel ECC-based public key scheme for medical data protection by utilization of NanoPi fire. IEEE Trans Reliab 67(3):1328–1339
Khashan OA, Khafajah NM (2023) Efficient hybrid centralized and blockchain-based authentication architecture for heterogeneous IoT systems. J King Saud Univ- Comput Inf Sci 35(2):726–739
Deebak BD, Al-Turjman F (2023) Secure-user sign-in authentication for IoT-based eHealth systems. Complex & Intell Syst 9(3):2629–2649
Khalid B, Qureshi KN, Ghafoor KZ, Jeon G (2023) An improved biometric based user authentication and key agreement scheme for intelligent sensor based wireless communication. Microprocess. Microsyst 96:104722
Lee J, Yu S, Kim M, Park Y, Das AK (2020) On the design of secure and efficient three-factor authentication protocol using honey list for wireless sensor networks. IEEE Access 8:107046–107062
Challa S, Wazid M, Das AK, Kumar N, Reddy AG, Yoon E-J, Yoo K-Y (2017) Secure signature-based authenticated key establishment scheme for future iot applications. IEEE Access 5:3028–3043
Zhou L, Li X, Yeh K-H, Su C, Chiu W (2019) Lightweight iotbased authentication scheme in cloud computing circumstance. Futur Gener Comput Syst 91:244–251
Farash MS, Turkanović M, Kumari S, Hölbl M (2016) An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the internet of things environment. Ad-Hoc Netw 36:152–176
Sharma G, Kalra S (2019) A lightweight user authentication scheme for cloud-iot based healthcare services. Iran J Sci Technol, Trans Electr Eng 43(1):619–636
Turkanović M, Brumen B, Hölbl M (2014) A novel user authentication and key agreement scheme for heterogeneous Ad-Hoc wireless sensornetworks, based on the internet of things notion. Ad Hoc Netw 20:96–112
Wazid M, Das AK, Shetty S, Rodrigues JPC, Park Y (2019) Ldakmeiot: Lightweight device authentication and key management mechanism for edge-based iot deployment. Sensors 19(24):5539
Acknowledgements
None
Author information
Authors and Affiliations
Contributions
Laleh Khajezadeh: Conception and design of study/review/case series, Acquisition of data, laboratory search, Drafting of article. Hamid Barati: Conception and design of study/review/case series, Analysis and interpretation of data collected, Final approval and guarantor of manuscript. Ali Barati: Acquisition of data, laboratory or clinical/literature search, Analysis and interpretation of data collected, Final approval.
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no conflict of interest.
Ethics approval
This article does not contain any studies with human participants.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Khajehzadeh, L., Barati, H. & Barati, A. A lightweight authentication and authorization method in IoT-based medical care. Multimed Tools Appl (2024). https://doi.org/10.1007/s11042-024-19379-2
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11042-024-19379-2