Abstract
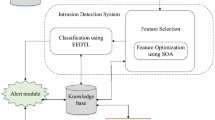
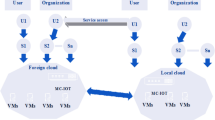
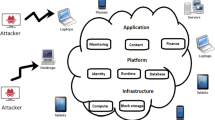
To execute seamless computing along with information sharing, Cloud Computing (CC) plays an important role in measurable resource sharing. But, owing to its open and distributed framework, privacy is a major risk as it is open to attackers. To accomplish their malicious goals, cloud services are abused by intruders. In this paper, using Linear Sigmoid Singleton Deep Neural Network (LS2DNN)with Pearson correlation and Brownian motion induced K-Anonymity (PBKA)centered lightweight privacy preservation technique in the cloud server, an efficient federated learning-based Intrusion Detection System (IDS) is proposed. From the publically available sources, NSL-KDD datasets are downloaded; also, Feature Extraction (FE), null feature removal, and feature mapping are executed. Subsequently, for feature selection, Chebyshev Chaotic Mapping adapted Jaya Optimization Algorithm (C2MJOA) is wielded. Then, for classifying attacked and normal data, the LS2DNNclassifier is utilized.The incoming data from the data owners are privacy preserved via federated learning-centered Pearson correlation and Brownian motion-induced K-Anonymity (PBKA) while testing; moreover, the data is verified for intrusion. Finally, when compared with the prevailing models, the proposed model attained better results.




Similar content being viewed by others
Data availability
Data sharing is not applicable to this article as no datasets were generated or analyzed during the current study.
References
Kene SG, Theng DP (2015) A review on intrusion detection techniques for cloud computing and security challenges, 2nd International Conference on Electronics and Communication Systems, 26–27 Feb 2015, Coimbatore, India
Ghribi S, Meddeb Makhlouf A, Zarai F (2017) Multi-layer cooperative intrusion detection system for cloud environment, 14th International Conference on Wireless Networks and Mobile Systems, July 24–26, 2017, Madrid, Spain
Mehmood Y, Kanwal A, Awais Shibli M, Masood R (2015) Distributed intrusion detection system using mobile agents in cloud computing environment, Conference on Information Assurance and Cyber Security (CIACS), 18–18 Dec 2015, Rawalpindi, Pakistan
Pham V, Seo E, Chung T-M (2020) Lightweight convolutional neural network based intrusion detection system. J Commun 15(11):808–817
Kumar U, Gohil BN (2015) A survey on intrusion detection systems for cloudcomputing environment. Int J Comput Appl 109:6–15
Salek Z, Mousavi Madani F (2016) Multi level intrusion detection system in cloud environment based on trust level, 6th International Conference on Computer and Knowledge Engineering (ICCKE), 20–20 Oct 2016, Mashhad, Iran
Asir Antony Gnana Singh D, Priyadharshini R, JebamalarLeavline E (2018) Cuckoo optimisation based intrusion detection system for cloud computing. Int J Comput Netw Inf Secur 10(11):42–49
Saleh Aljurayban N, Emam A (2015) Framework for cloud intrusion detection system service, 2nd World Symposium on Web Applications and Networking (WSWAN), 21–23 March 2015, Sousse, Tunisia
Li Z, Haitao Xu, Liu Y (2017) A differential game model of intrusion detection system in cloud computing. Int J Distrib Sens Netw 13(1):1–11
Ghosh P, Shakti S, Phadikar S (2016) A cloud intrusion detection systemusing novel PRFCM clustering and KNN based dempster-shafer rule. Int J Cloud Appl Comput 6(4):18–35
Amarudin RF and Widyawan (2020) A systematic literature review of intrusion detection system for network security research trends, datasets and methods, 4th International Conference on Informatics and Computational Sciences (ICICoS), 10–11 Nov 2020, Semarang, Indonesia
Samrin R, Vasumathi D (2017) Review on anomaly based network intrusion detection system, International Conference on Electrical, Electronics, Communication, Computer and Optimization Techniques (ICEECCOT), 15–16 Dec 2017, Mysuru, India
Mishra V, Kumar Vijay V, Tazi S (2016) Intrusion detection system with snort in cloud computing advanced IDS, Springer, Singapore, ISBN: 978–981–10–0127–7
Saranya T, Sridevi S, Deisy C, Chung TD, Ahamed Khan MKA (2020) Performance analysis of machine learning algorithms in intrusion detection system a review. Procedia Comput Sci 171:1251–1260
Ghosh P, Mandal AK, Kumar R (2015) An efficient cloud network intrusion detection system. Adv Intell Syst Comput 339:91–99
Balamurugan V, Saravanan R (2017) Enhanced intrusion detection and prevention system on cloud environment using hybrid classification and OTS generation. Clust Comput 22(3):13027–13039
Samriya JK, Kumar N (2020) A novel intrusion detection system using hybrid clustering optimization approach in cloud computing. Mater Today Proc (In Press). https://doi.org/10.1016/j.matpr.2020.09.614
Patil R, Dudeja H, Gawade S, Modi C (2018) Protocol specific multi thrraded network intrusion detection system (PM-NIDS) for DoS/DDoS attack detection in cloud, 9th International Conference on Computing, Communication and Networking Technologies (ICCCNT), 10–12 July 2018, Bengaluru, India
Alabdulatif A, Khalil I, Kumarage H, Zomaya AY, Yi X (2018) Privacy-preserving anomaly detection in the cloud for quality assured decision-making in smart cities. J Parallel Distrib Comput 127:209–223
Dwivedi S, Vardhan M, Tripathi S (2021) Building an efficient intrusion detection system using grasshopper optimization algorithm for anomaly detection. Cluster Computing 24(4):1–20
Zhou Y, Cheng G, Jiang S, Dai M (2020) Building an efficient intrusion detection system based on feature selection and ensemble classifier. Comput Netw 174:1–21
Mondal A, Goswami RT (2021) Enhanced honeypot cryptographic scheme and privacy preservation for an effective prediction in cloud security. Microprocess Micro Syst 81:1–10
Singh P, Ranga V (2021) Attack and intrusion detection in cloud computing usingan ensemble learning approach. Int J Inf Technol 13(2):565–571
Jaber AN, UlRehman S (2020) FCM–SVM based intrusion detection system for cloud computing environment. Clust Comput 23:3221–3231
Samriya JK, Kumar N (2020) A novel Intrusion detection system using hybrid clustering -optimization approach in cloud computing. Mater Today Proc, pp. 1–6. https://www.researchgate.net/profile/Jitendra-Samriya/publication/346008755_A_novel_intrusion_detection_system_using_hybrid_clusteringoptimization_approach_in_cloud_computing/links/640be22466f8522c3896d678/A-novel-intrusion-detection-system-using-hybrid-clustering-optimization-approach-in-cloud-computing.pdf
Aldallal A, Alisa F (2021) Effective intrusion detection system to secure data in cloud using machine learning. Symmetry 13(12):1–26
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Gupta, R., Alam, T. An efficient federated learning based intrusion detection system using LS2DNN with PBKA based lightweight privacy preservation in cloud server. Multimed Tools Appl 83, 44685–44697 (2024). https://doi.org/10.1007/s11042-023-17401-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-17401-7