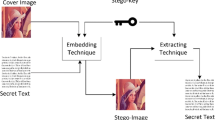
Abstract
Transferring multimedia content without detection has gained traction over time. Employing steganography for hiding secret data, viz. passwords, medical information, and private messages, has become the norm. This work involves hiding confidential information in the images. It aims to increase the payload capacity by adaptively choosing the embedding pixel location, using hamming distance, and increasing the number of bits embedded per pixel using threshold while retaining the image quality. The secret PHI information was embedded into the medical cover image by choosing the pixels, such that the embedding order was random. The randomness in the embedding order was achieved by generating a random sequence using a Combined Logistical Tent map. (CLT map). The random sequence was used as the key to choose all the pixels, but in a random order for embedding. Two different ways can generate the CLT map. One is by generating the Logistical map sequence and Tent map sequence and performing the XOR operation of both sequences. The other way is to generate the CLT map sequence through governing equations. The algorithm is designed to perform embedding for images of various modalities, viz. effectively., Grayscale, RGB and DICOM. The algorithm was tested for over 100 images across databases. The test results were satisfactory. The resultant stego image has an acceptable range of Peak Signal to Noise Ratio (PSNR) values above 40 dB and Structural Similarity Index (SSIM) values above 0.9. The stego images with visually imperceptible secret information are good quality and could effectively mitigate steganalysis.



















Similar content being viewed by others
Data availability
Data sharing not applicable to this article as no datasets were generated or analysed during the current study.
References
Ahmad MA, Elloumi M, Samak AH, Al-Sharafi AM, Alqazzaz A, Kaid MA, Iliopoulos C (2022) Hiding patients’ medical reports using an enhanced wavelet steganography algorithm in DICOM images. Alex Eng J 61(12):10577–10592. https://doi.org/10.1016/j.aej.2022.03.056
Ansari AS, Mohammadi MS, Parvez MT (2020) A multiple-format steganography algorithm for color images. IEEE Access 8:83926–83939. https://doi.org/10.1109/ACCESS.2020.2991130
Cao Z, Yin Z, Hu H, Gao X, Wang L (2016) High capacity data hiding scheme based on (7, 4) Hamming code. Springerplus 5(1):1–13. https://doi.org/10.1186/s40064-016-1818-0
Chatterjee A, Ghosal SK, Sarkar R (2020) LSB based steganography with OCR: an intelligent amalgamation. Multimed Tools Appl 79(17–18):11747–11765. https://doi.org/10.1007/s11042-019-08472-6
Cheng J, Chen Z, Yang R (2018) An efficient histogram-preserving steganography based on block. Eurasip J Image Video Process 2018(1):1–13. https://doi.org/10.1186/s13640-018-0306-6
Chervyakov N, Lyakhov P, Nagornov N (2020) Analysis of the quantization noise in discrete wavelet transform filters for 3D medical imaging. Appl Sci 10(4):1223. https://doi.org/10.3390/app10041223
“DICOM Library - Anonymize, Share, View DICOM files ONLINE.” (n.d.) https://www.dicomlibrary.com/?manage=02ef8f31ea86a45cfce6eb297c274598. Accessed 16 Apr. 2021
“Downloads available.” (n.d.) http://www.pcir.org/researchers/downloads_available.html. Accessed 16 Apr. 2021
Duan X, Guo D, Liu N, Li B, Gou M, Qin C (2020) A New High Capacity Image Steganography Method Combined with Image Elliptic Curve Cryptography and Deep Neural Network. IEEE Access 8:25777–25788. https://doi.org/10.1109/ACCESS.2020.2971528
Duan X, Wang W, Liu N, Yue D, Xie Z, Qin C (2020) StegoPNet: Image Steganography With Generalization Ability Based on Pyramid Pooling Module. IEEE Access 8:195253–195262. https://doi.org/10.1109/access.2020.3033895
Elhadad A, Ghareeb A, Abbas S (2021) A blind and high-capacity data hiding of DICOM medical images based on fuzzification concepts. Alexandria Eng J 60(2):2471–2482. https://doi.org/10.1016/j.aej.2020.12.050
El-Khamy SE, Korany NO, Mohamed AG (2020) A New Fuzzy-DNA Image Encryption and Steganography Technique. IEEE Access 8:148935–148951. https://doi.org/10.1109/ACCESS.2020.3015687
Faragallah OS, El-Hoseny H, El-Shafai W, Abd El-Rahman W, El-Sayed HS, El-Rabaie ESM, Abd El-Samie FE, Geweid GG (2020) A comprehensive survey analysis for present solutions of medical image fusion and future directions. IEEE Access 9:11358–11371. https://doi.org/10.1109/ACCESS.2020.3048315
Hameed MA, Hassaballah M, Aly S, Awad AI (2019) An adaptive image steganography method based on histogram of oriented gradient and PVD-LSB techniques. IEEE Access 7:185189–185204. https://doi.org/10.1109/ACCESS.2019.2960254
Hamzaoui R, Saupe D (2006) In: Barni M (ed) Fractal Image Compression. Document and Image Compression, vol 968. CRC Press, pp 168–169 ISBN 9780849335563. Retrieved 5 April 2011
Huang L-C, Chiou S-F, Hwang M-S (2021) A Reversible Data Hiding Based on Histogram Shifting of Prediction Errors for Two-Tier Medical Images. Informatica 32(1):69–84. https://doi.org/10.15388/20-infor422
“Image Databases.” (n.d.) http://www.imageprocessingplace.com/root_files_V3/image_databases.htm. Accessed 16 Apr. 2021
Jayapandiyan JR, Kavitha C, Sakthivel K (2020) Enhanced Least Significant Bit Replacement Algorithm in Spatial Domain of Steganography Using Character Sequence Optimization. IEEE Access 8:136537–136545. https://doi.org/10.1109/ACCESS.2020.3009234
Karakus S, Avci E (2020) A new image steganography method with optimum pixel similarity for data hiding in medical images. Med Hypotheses 139:109691. https://doi.org/10.1016/j.mehy.2020.109691
Kasapbasi MC (2019) A New Chaotic Image Steganography Technique Based on Huffman Compression of Turkish Texts and Fractal Encryption with Post-Quantum Security. IEEE Access 7:148495–148510. https://doi.org/10.1109/ACCESS.2019.2946807
Kim P-H, Ryu K-W, Jung K-H (2020) Reversible data hiding scheme based on pixel-value differencing in dual images. Int J Distrib Sens Networks 16(7):155014772091100. https://doi.org/10.1177/1550147720911006
Lawnik M (2018) Combined logistic and tent map. J Phys Conf Ser 1141(1):12132. https://doi.org/10.1088/1742-6596/1141/1/012132
Lin C-C, Lin J, Chang C-C (2021) Reversible Data Hiding for AMBTC Compressed Images Based on Matrix and Hamming Coding. Electronics 10(3):281. https://doi.org/10.3390/electronics10030281
Nashat D, Mamdouh L (2019) An efficient steganographic technique for hiding data. J Egypt Math Soc 27(1):57. https://doi.org/10.1186/s42787-019-0061-6
Phadikar A, Jana P, Mandal H (2019) Reversible Data Hiding for DICOM Image Using Lifting and Companding. Cryptography 3:21. https://doi.org/10.3390/cryptography3030021
Rustad S, Setiadi DRIM, Syukur A, Andono PN (2021) Inverted LSB image steganography using adaptive pattern to improve imperceptibility. J King Saud Univ - Comput Inf Sci 34:3559–3568. https://doi.org/10.1016/j.jksuci.2020.12.017
“Sample DICOM files.” (n.d.) https://www.rubomedical.com/dicom_files/index.html. Accessed 20 Jul 2023
Su A, Ma S, Zhao X (2020) Fast and Secure Steganography Based on J-UNIWARD. IEEE Signal Process Lett 27:221–225. https://doi.org/10.1109/LSP.2020.2964485
Su GD, Lin CC, Chang CC (2021) Privacy-Preserving Reversible Data Hiding for Medical Images Employing Local Rotation. J Healthc Eng 2021:5709513. https://doi.org/10.1155/2021/5709513
Verma V, Muttoo SK, Singh VB (2020) Enhanced payload and trade-off for image steganography via a novel pixel digits alteration. Multimed Tools Appl 79(11–12):7471–7490. https://doi.org/10.1007/s11042-019-08283-9
Wazirali R, Alasmary W, Mahmoud MMEA, Alhindi A (2019) An Optimized Steganography Hiding Capacity and Imperceptibly Using Genetic Algorithms. IEEE Access 7:133496–133508. https://doi.org/10.1109/ACCESS.2019.2941440
Welstead ST (1999) Fractal and wavelet image compression techniques. SPIE Publication, https://spie.org/Publications/Book/353798
Zhang W, Li S (2008) A coding problem in steganography. Des Codes Crypt 46(1):67–81. https://doi.org/10.1007/s10623-007-9135-9
Zhang Y, Luo X, Guo Y, Qin C, Liu F (2019) Zernike Moment-Based Spatial Image Steganography Resisting Scaling Attack and Statistic Detection. IEEE Access 7:24282–24289. https://doi.org/10.1109/ACCESS.2019.2900286
Acknowledgments
Authors thank the Department of Science & Technology, New Delhi, for the FIST funding (SR/FST/ET-I/2018/221(C)). The authors thank Intrusion LAB at School of Electrical & Electronics Engineering, SASTRA Deemed University, for providing infrastructural support to carry out this research work.
Funding
DST FIST funding (SR/FST/ET-I/2018/221(C)).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Ethics approval
This article contains no studies with human participants performed by authors.
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Manikandan, V., Amirtharajan, R. Cartesian coordinated adaptive hiding for payload peaking. Multimed Tools Appl 83, 17135–17162 (2024). https://doi.org/10.1007/s11042-023-16208-w
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-16208-w