Abstract
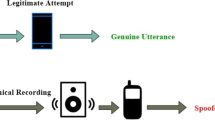
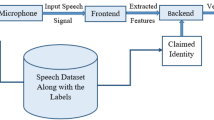
Speaker-verification-system (SVS) is automated nowadays to improve the authenticity score of digital applications. However, spoofs in the audio signal have reduced the integrity score of the audio signal, which has tended to cause less authentication exactness score. Considering this, spoof recognition objectives emerged in this field to find the different types of spoofs with high exactness scores. Attracting the widest spoof forecasting score is impossible due to harmful and different spoof features. So, the present study built a novel Dove-based Recurrent Spoof Recognition System (DbRSRS) to identify the spoofing behaviour and its types from the trained audio data. The noise features were filtered in the primary stage to mitigate the complexity of spoof recognition. Moreover, the noise features filtered data is taken to the classification phase for feature selection and spoof recognition. Here, the spoof types were classified based on the different class features. Once the Spoof is identified, it is specified under different spoof classes. Here, the optimal dove features are utilized to tune the DbRSRS classification parameters. This process helped to earn the finest spoof recognition score than the recently published associated model. Henceforth, the recorded highest spoof forecasting accuracy was 99.2%, and the reported less error value was 0.05%. Thus, attaining the highest spoof prediction exactness score with less error value might improve the SVS performance.








Similar content being viewed by others
Data availability
Data sharing not applicable to this article as no datasets were generated or analyzed during the current study.
References
Alhumoud SO, Al Wazrah AA (2022) Arabic sentiment analysis using recurrent neural networks: a review. Artif Intell Rev 55(1):707–748. https://doi.org/10.1007/s10462-021-09989-9
Bharath KP, Kumar MR (2022) Replay spoof detection for speaker verification system using magnitude-phase-instantaneous frequency and energy features. Multimed Tools Appl 81:39343–39366. https://doi.org/10.1007/s11042-022-12380-7
Chettri B, Kinnunen T, Benetos E (2020) Deep generative variational autoencoding for replay spoof detection in automatic speaker verification. Comput Speech Lang 63:101092. https://doi.org/10.1016/j.csl.2020.101092
Chugh T, Jain AK (2020) Fingerprint spoof detector generalization. IEEE Trans Inf Forensics Secur 16:42–55. https://doi.org/10.1109/TIFS.2020.2990789
Dang Y, Benzaïd C, Yang B, Taleb T, Shen Y (2022) Deep ensemble learning based GPS spoofing detection for cellular-connected UAVs. IEEE Internet Things J 9(24):25068–25085. https://doi.org/10.1109/JIOT.2022.3195320
Daniel N, Anitha A (2021) Texture and quality analysis for face spoofing detection. Comput Electr Eng 94:107293. https://doi.org/10.1016/j.compeleceng.2021.107293
Dua M, Sadhu A, Jindal A, Mehta R (2022) A hybrid noise robust model for multireplay attack detection in Automatic speaker verification systems. Biomed Signal Process Control 74:103517. https://doi.org/10.1016/j.bspc.2022.103517
Dua M, Jain C, Kumar S (2022) LSTM and CNN based ensemble approach for spoof detection task in automatic speaker verification systems. J Ambient Intell Humaniz Comput 13(4):1985–2000. https://doi.org/10.1007/s12652-021-02960-0
Hanilçi C (2018) Linear prediction residual features for automatic speaker verification anti-spoofing. Multimed Tools Appl 77:16099–16111. https://doi.org/10.1007/s11042-017-5181-0
Huszár VD, Adhikarla VK (2021) Live spoofing detection for automatic human activity recognition applications. Sensors 21(21):7339. https://doi.org/10.3390/s21217339
Iliev Y, Ilieva G (2023) A Framework for Smart Home System with Voice Control Using NLP Methods. Electronics 12(1):116. https://doi.org/10.3390/electronics12010116
Kinnunen T, Delgado H, Evans N, Lee KA, Vestman V, Nautsch A, Todisco M, Wang X, Sahidullah M, Yamagishi J, Reynolds DA (2020) Tandem assessment of spoofing countermeasures and automatic speaker verification: Fundamentals. IEEE/ACM Trans Audio Speech Lang Process 28:2195–2210. https://doi.org/10.1109/TASLP.2020.3009494
Kwon KC, Shim DS (2020) Performance analysis of direct gps spoofing detection method with ahrs/accelerometer. Sensors 20(4):954. https://doi.org/10.3390/s20040954
Mingote V, Miguel A, Ortega A, Lleida E (2023) Class token and knowledge distillation for multi-head self-attention speaker verification systems. Digit Signal Process 133:103859. https://doi.org/10.1016/j.dsp.2022.103859
Nainan S, Kulkarni V (2021) Enhancement in speaker recognition for optimized speech features using GMM, SVM and 1-D CNN. Int J Speech Technol 24(4):809–822. https://doi.org/10.1007/s10772-020-09771-2
Nassif AB, Shahin I, Hamsa S, Nemmour N, Hirose K (2021) CASA-based speaker identification using cascaded GMM-CNN classifier in noisy and emotional talking conditions. Appl Soft Comput 103:107141. https://doi.org/10.1016/j.asoc.2021.107141
Neelima M, Santi Prabha I (2020) Spoofing Detection and Countermeasure in Automatic Speaker Verification System using Dynamic Features. Int J Recent Technol Eng (IJRTE) 8(5):3676–3680. https://doi.org/10.35940/ijrte.E6582.018520
Neelima M, Santiprabha I (2020) Mimicry voice detection using convolutional neural networks. 2020 International Conference on Smart Electronics and Communication (ICOSEC), IEEE. https://doi.org/10.1109/ICOSEC49089.2020.9215407
Qin Z, Zhao P, Zhuang T, Deng F, Ding Y, Chen D (2023) A survey of identity recognition via data fusion and feature learning. Inf Fusion 91:694–712. https://doi.org/10.1016/j.inffus.2022.10.032
Rahmeni R, Aicha AB, Ayed YB (2022) Voice spoofing detection based on acoustic and glottal flow features using conventional machine learning techniques. Multimed Tools Appl 81:31443–31467. https://doi.org/10.1007/s11042-022-12606-8
Ross A, Banerjee S, Chowdhury A (2020) Security in smart cities: A brief review of digital forensic schemes for biometric data. Pattern Recogn Lett 138:346–354. https://doi.org/10.1016/j.patrec.2020.07.009
Rostami M, Oussalah M, Berahmand K et al (2023) Community Detection Algorithms in Healthcare Applications: A Systematic Review. IEEE Access 11:30247–30272. https://doi.org/10.1109/ACCESS.2023.3260652
Rostami AM, Homayounpour MM, Nickabadi A (2023) Efficient attention branch network with combined loss function for automatic speaker verification spoof detection. Circuits Syst Signal Process 42:4252–4270. https://doi.org/10.1007/s00034-023-02314-5
Sankar MSA, Sathidevi PS (2023) A Wideband Scalable Bit Rate Mixed Excitation Linear Prediction-Enhanced Speech Coder by Preserving Speaker-Specific Features. Circuits Syst Signal Process 42:3437–3463. https://doi.org/10.1007/s00034-022-02277-z
Saritha B, Laskar MA, Laskar RH (2023) A Comprehensive Review on Speaker Recognition. Advances in Speech and Music Technology 3–23. https://doi.org/10.1007/978-3-031-18444-4_1
Schmidt E, Gatsis N, Akopian D (2020) A GPS spoofing detection and classification correlator-based technique using the LASSO. IEEE Trans Aerosp Electron Syst 56(6):4224–4237. https://doi.org/10.1109/TAES.2020.2990149
Semanjski S, Semanjski I, De Wilde W, Muls A (2020) Use of supervised machine learning for GNSS signal spoofing detection with validation on real-world meaconing and spoofing data—Part I. Sensors 20(4):1171. https://doi.org/10.3390/s20041171
Sheikhpour R, Berahmand K, Forouzandeh S (2023) Hessian-based semi-supervised feature selection using generalized uncorrelated constraint. Knowl Based Syst 269:110521. https://doi.org/10.1016/j.knosys.2023.110521
Su MC, Chen JH, Utami AM, Lin SC, Wei HH (2022) Dove swarm optimization algorithm. IEEE Access 10:46690–46696. https://doi.org/10.1109/ACCESS.2022.3170112
Sun W, Song Y, Chen C, Huang J, Kot AC (2020) Face spoofing detection based on local ternary label supervision in fully convolutional networks. IEEE Trans Inf Forensics Secur 15:3181–3196. https://doi.org/10.1109/TIFS.2020.2985530
Wei X, Wang Y, Sun C (2022) PerDet: Machine-Learning-Based UAV GPS Spoofing Detection Using Perception Data. Remote Sens 14(19):4925. https://doi.org/10.3390/rs14194925
Yang J, Wang H, Das RK, Qian Y (2021) Modified magnitude-phase spectrum information for spoofing detection. IEEE/ACM Trans Audio Speech Lang Process 29:1065–1078. https://doi.org/10.1109/TASLP.2021.3060810
Zhang Y, Jiang F, Duan Z (2021) One-class learning towards synthetic voice spoofing detection. IEEE Signal Process Lett 28:937–941. https://doi.org/10.1109/LSP.2021.3076358
Zhang H, Wang L, Lee KA, Liu M et al (2023) Meta-generalization for domain-invariant speaker verification. IEEE/ACM Trans Audio Speech Lang Process 31:1024–1036. https://doi.org/10.1109/TASLP.2023.3244518
Zhu Y, Mak B (2023) Bayesian Self-Attentive Speaker Embeddings for Text-Independent Speaker Verification. IEEE/ACM Trans Audio Speech Lang Process 31:1000–1012. https://doi.org/10.1109/TASLP.2023.3244502
Acknowledgements
None.
Funding
This research did not receive any specific grant from funding agencies in the public, commercial, or not-for-profit sectors.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Ethical approval
All applicable institutional and/or national guidelines for the care and use of animals were followed.
Informed consent
For this type of analysis formal consent is not needed.
Conflict of interest
The authors declare that they have no potential conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Neelima, M., Prabha, I.S. Optimized deep network based spoof detection in automatic speaker verification system. Multimed Tools Appl 83, 13073–13091 (2024). https://doi.org/10.1007/s11042-023-16127-w
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-16127-w