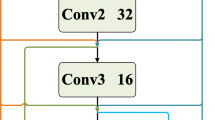
Abstract
Forged images in JPEG format have a ubiquitous presence in today’s world due to the ease of availability of image manipulation tools. This paper presents a deep learning-based system that utilizes the inherent relationship between histograms of quantized DCT coefficients and corresponding quantization step sizes to distinguish between original and forged regions in a JPEG image, based on detecting single and double compressed blocks, without fully decompressing the JPEG image. In this direction, we propose a novel combination of raw histograms of the quantized DCT coefficients and corresponding quantization step sizes and use it as input to the counterpart standard CNN architectures designed to handle the proposed input representation for single vs. double JPEG compression detection. The proposed input is shown to have a minimal effect on performance with various standard CNN architectures that are designed to handle the proposed input for the task at hand. Specifically, we have utilized DenseNet to extract the compression-specific artifacts from the proposed input for additional experiments reported in this work. We considered a publicly available dataset generated with a diverse set of 1,120 quantization matrices. Using the proposed input to learn the compression artifacts outperforms the baseline methods for the blocks of sizes \(256 \times 256\), \(128 \times 128\), and \(64 \times 64\). Furthermore, in the case of test blocks compressed with completely different quantization matrices than matrices used in training, the proposed method outperforms the baseline methods. Consequently, improved forgery localization performances are obtained for forged JPEG images.






Similar content being viewed by others
References
Amerini, I., Becarelli, R., Caldelli, R., Del Mastio, A.: Splicing forgeries localization through the use of first digit features. In: IEEE International Workshop on Information Forensics and Security (WIFS), 143–148 (2014)
Amerini, I., Uricchio, T., Ballan, L., Caldelli, R.: Localization of jpeg double compression through multi-domain convolutional neural networks. In: IEEE Conference on computer vision and pattern recognition workshops (CVPRW), 1865–1871. IEEE (2017)
Barni M, Bondi L, Bonettini N, Bestagini P, Costanzo A, Maggini M, Tondi B, Tubaro S (2017) Aligned and non-aligned double JPEG detection using convolutional neural networks. Journal of Visual Communication and Image Representation 49:153–163
Bas, P., Filler, T., Pevnỳ, T.: Break our steganographic system: The ins and outs of organizing boss. In: International Workshop on Information Hiding, 59–70. Springer Berlin Heidelberg (2011)
Bianchi, T., De Rosa, A., Piva, A.: Improved dct coefficient analysis for forgery localization in jpeg images. In: 2011 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), 2444–2447 (2011)
Chen YL, Hsu CT (2011) Detecting recompression of jpeg images via periodicity analysis of compression artifacts for tampering detection. IEEE Transactions on Information Forensics and Security 6(2):396–406
Chollet, F.: Xception: Deep learning with depthwise separable convolutions. In: Proceedings of the IEEE conference on computer vision and pattern recognition, 1251–1258 (2017)
Dang-Nguyen, D.T., Pasquini, C., Conotter, V., Boato, G.: Raise: A raw images dataset for digital image forensics. In: Proceedings of the 6th ACM Multimedia Systems Conference, MMSys ’15, 219-224. Association for Computing Machinery (2015)
Farid H (2009) Exposing digital forgeries from jpeg ghosts. IEEE transactions on information forensics and security 4(1):154–160
Fu D, Shi YQ, Su W (2007) A generalized Benford’s law for JPEG coefficients and its applications in image forensics. Security, vol 6505. Steganography, and Watermarking of Multimedia Contents IX. International Society for Optics and Photonics, SPIE, pp 574–584
Gloe T, Böhme R (2010) The dresden image database for benchmarking digital image forensics. Journal of Digital Forensic Practice 3(2–4):150–159
Glorot, X., Bengio, Y.: Understanding the difficulty of training deep feedforward neural networks. In: Proceedings of the Thirteenth International Conference on Artificial Intelligence and Statistics, Proceedings of Machine Learning Research, vol. 9, 249–256. PMLR (2010)
He, K., Zhang, X., Ren, S., Sun, J.: Deep residual learning for image recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition, 770–778 (2016)
Hsu, Y.F., Chang, S.F.: Detecting image splicing using geometry invariants and camera characteristics consistency. In: IEEE International Conference on Multimedia and Expo, 549–552 (2006)
Huang, G., Liu, Z., Van Der Maaten, L., Weinberger, K.Q.: Densely connected convolutional networks. In: Proceedings of the IEEE conference on computer vision and pattern recognition, 4700–4708 (2017)
Kingma, D.P., Ba, J.: Adam: A method for stochastic optimization. arXiv preprint http://arxiv.org/abs/1412.6980arXiv:1412.6980 (2014)
Korus P (2017) Digital image integrity-a survey of protection and verification techniques. Digital Signal Processing 71:1–26
Li, B., Luo, H., Zhang, H., Tan, S., Ji, Z.: A multi-branch convolutional neural network for detecting double jpeg compression. arXiv preprint http://arxiv.org/abs/1710.05477arXiv:1710.05477 (2017)
Li, B., Shi, Y.Q., Huang, J.: Detecting doubly compressed jpeg images by using mode based first digit features. In: Proceedings of IEEE 10th Workshop on Multimedia Signal Processing, 730–735 (2008)
Li B, Zhang H, Luo H, Tan S (2019) Detecting Double JPEG Compression and Its Related Anti-Forensic Operations with CNN. Multimedia Tools and Applications 78(7):8577–8601
Li W, Yuan Y, Yu N (2009) Passive detection of doctored JPEG image via block artifact grid extraction. Signal Processing 89(9):1821–1829
Lin Z, He J, Tang X, Tang CK (2009) Fast, automatic and fine-grained tampered JPEG image detection via DCT coefficient analysis. Pattern Recognition 42(11):2492–2501
Lukáš, J., Fridrich, J.: Estimation of primary quantization matrix in double compressed jpeg images. In: Proceedings Digital Forensic Research Workshop, 5–8 (2003)
Luo, W., Qu, Z., Huang, J., Qiu, G.: A novel method for detecting cropped and recompressed image block. In: IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), vol. 2, II–217–II–220 (2007)
Milani, S., Tagliasacchi, M., Tubaro, S.: Discriminating multiple jpeg compressions using first digit features. APSIPA Transactions on Signal and Information Processing 3 (2014)
Park, J., Cho, D., Ahn, W., Lee, H.K.: Double jpeg detection in mixed jpeg quality factors using deep convolutional neural network. In: Proceedings of the European Conference on Computer Vision (ECCV), 636–652 (2018)
Pasquini, C., Boato, G., Perez-Gonzalez, F.: Multiple jpeg compression detection by means of benford-fourier coefficients. In: Proceedings IEEE International Workshop on Information Forensics and Security (WIFS), 113–118 (2014)
Piva, A.: An overview on image forensics. Hindawi Publishing Corporation, International Scholarly Research Notices (ISRN) Signal Processing 2013 (2013)
Popescu, A.C., Farid, H.: Statistical tools for digital forensics. In: Information Hiding, vol. 3200, 395–407. Springer (2004)
Redi JA, Taktak W, Dugelay JL (2011) Digital image forensics: a booklet for beginners. Multimedia Tools and Applications 51(1):133–162
Schaefer, G., Stich, M.: Ucid: an uncompressed color image database. In: Storage and Retrieval Methods and Applications for Multimedia, vol. 5307, 472 – 480. International Society for Optics and Photonics, SPIE (2003)
Sencar, H.T., Memon, N.: Overview of state-of-the-art in digital image forensics. Algorithms, Architectures and Information Systems Security 325–347 (2009)
Simonyan, K., Zisserman, A.: Very deep convolutional networks for large-scale image recognition. arXiv preprint http://arxiv.org/abs/1409.1556arXiv:1409.1556 (2014)
Stamm MC, Wu M, Liu KR (2013) Information forensics: An overview of the first decade. IEEE access 1:167–200
Taimori A, Razzazi F, Behrad A, Ahmadi A, Babaie-Zadeh M (2017) A novel forensic image analysis tool for discovering double jpeg compression clues. Multimedia Tools and Applications 76(6):7749–7783
Verdoliva L (2020) Media forensics and deepfakes: An overview. IEEE Journal of Selected Topics in Signal Processing 14(5):910–932. https://doi.org/10.1109/JSTSP.2020.3002101
Verma V, Agarwal N, Khanna N (2018) DCT-domain deep convolutional neural networks for multiple JPEG compression classification. Signal Processing: Image Communication 67:22–33
Wallace, G.K.: The jpeg still picture compression standard. IEEE transactions on consumer electronics 38(1), xviii–xxxiv (1992)
Wang Q, Zhang R (2016) Double jpeg compression forensics based on a convolutional neural network. EURASIP Journal on Information Security 23(1):1–12
Wang W, Dong J, Tan T (2014) Exploring dct coefficient quantization effects for local tampering detection. IEEE Transactions on Information Forensics and Security 9(10):1653–1666
Ye, S., Sun, Q., Chang, E.: Detecting Digital Image Forgeries by Measuring Inconsistencies of Blocking Artifact. In: IEEE International Conference on Multimedia and Expo, 12–15 (2007)
Zeng X, Feng G, Zhang X (2019) Detection of double jpeg compression using modified densenet model. Multimedia Tools and Applications 78(7):8183–8196
Acknowledgements
The authors would like to thank the editor and anonymous reviewers for their careful reading of our manuscript and their insightful comments and valuable suggestions, which helped in improving the quality of the manuscript.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflicts of interest
This material is based upon work partially supported by a grant from the Department of Science and Technology (DST), New Delhi, India, under Award Number ECR/2015/000583. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the funding agencies. Address all correspondence to Nitin Khanna at nitin@iitbhilai.ac.in.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Verma, V., Singh, D. & Khanna, N. Block-level double JPEG compression detection for image forgery localization. Multimed Tools Appl 83, 9949–9971 (2024). https://doi.org/10.1007/s11042-023-15942-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15942-5