Abstract
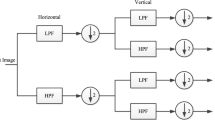
Steganography is the art and a science of obscuring the presence of communication by hiding content in electronic media and so obscuring the presence of communication from the adversary’s perspective. The goal of spatial adaptive approaches is to incorporate additional information in the image’s edge regions. The portions of the picture with the most changes are prioritized for embedding in these approaches. In contrast, wavelet-based approaches insert in high-frequency sub-bands to resemble the human visual system. The concept described in this study is a hybrid of these two concepts. On the contrary, the coefficients of the wavelet transform’s high-frequency sub-bands are more suited for embedding, since they have bigger coefficients surrounding them and reflect the image’s edge regions. Based on a local neighborhood analysis, an edge intensity criterion is employed to identify the suitable embedding coefficients in this technique. The receiver may also recognize these coefficients and fully extract the encoded data. In the suggested technique, the picture is first blocked, and then each block is given a wavelet transform. Several coefficients are discovered for each high-frequency sub-band, depending on the duration of the data, and then, using a genetic algorithm and the coefficients are chosen from the detected coefficients using a genetic approach to ensure that the resulting stego picture has the maximum PSNR value. The results of the implementation reveal that in the suggested strategy, employing the Integer Wavelet Transform is far more effective than using the Discrete Wavelet Transform. The suggested approach is safe against steganalysis assaults such as PDH analysis, RS, and universal steganalysers, and the quality of the stego picture is better than previous methods like SPAM (Steganography by Printed Arrays by Microbes) and SRM (Spatial Rich Model).














Similar content being viewed by others
References
Abedini A, Miri A, Maleki A (2017) Parallel Improved Pulse Coupled Neural Network Application for Edge Detection in Image Processing. Comput. Eng. Inf. Technol. 06(02). https://doi.org/10.4172/2324-9307.1000170
Al-Dmour H, Al-Ani A (2016) A steganography embedding method based on edge identification and XOR coding. Expert Syst. Appl. 46. https://doi.org/10.1016/j.eswa.2015.10.024
Atawneh S, Almomani A, Al Bazar H, Sumari P, Gupta B (2017) Secure and imperceptible digital image steganographic algorithm based on diamond encoding in DWT domain. Multimed. Tools Appl. 76(18). https://doi.org/10.1007/s11042-016-3930-0
Banharnsakun A (2018) Artificial bee colony approach for enhancing LSB based image steganography. Multimed. Tools Appl 77(20). https://doi.org/10.1007/s11042-018-5933-5
Chang CC, Tseng HW (2004) A steganographic method for digital images using side match. Pattern Recognit. Lett. 25(12). https://doi.org/10.1016/j.patrec.2004.05.006
Chang CC, Pai PY, Yeh CM, Chan YK (2010) A high payload frequency-based reversible image hiding method. Inf. Sci. (Ny). 180(11). https://doi.org/10.1016/j.ins.2010.01.034
Cheddad A, Condell J, Curran K, Mc Kevitt P (Mar. 2010) Digital image steganography: survey and analysis of current methods. Signal Process 90(3):727–752. https://doi.org/10.1016/J.SIGPRO.2009.08.010
Chen P-Y, Wu W-E (2009) A Modified Side Match Scheme for Image Steganography. Int. J. Appl. Sci. Eng. 7
Chen WJ, Chang CC, Le THN (2010) High payload steganography mechanism using hybrid edge detector. Expert Syst. Appl. 37(4). https://doi.org/10.1016/j.eswa.2009.09.050
Douglas M, Bailey K, Leeney M, Curran K (2018) An overview of steganography techniques applied to the protection of biometric data. Multimed. Tools Appl. 77(13). https://doi.org/10.1007/s11042-017-5308-3
El Safy RO, Zayed HH, El Dessouki A (2009) An adaptive steganographic technique based on integer wavelet transform. https://doi.org/10.1109/ICNM.2009.4907200
Fakhredanesh M, Rahmati M, Safabakhsh R (2019) Steganography in discrete wavelet transform based on human visual system and cover model. Multimed. Tools Appl. 78(13). https://doi.org/10.1007/s11042-019-7238-8
Fridrich J, Kodovsky J (2012) Rich models for steganalysis of digital images. IEEE Trans Inf Forensics Secur 7(3):868–882. https://doi.org/10.1109/TIFS.2012.2190402
Gulve AK, Joshi MS (2015) An image steganography method hiding secret data into coefficients of integer wavelet transform using pixel value differencing approach. Math. Probl. Eng. 2015. https://doi.org/10.1155/2015/684824
Hussain M, Wahab AWA, Bin Idris YI, Ho ATS, Jung KH (2018) Image steganography in spatial domain: A survey. Signal Process. Image Commun. 65. https://doi.org/10.1016/j.image.2018.03.012
Jayasingh RJ, Kumar RJS, Telagathoti DB, Sagayam KM, Pramanik S (2022) Speckle noise removal by SORAMA segmentation in digital image processing to facilitate precise robotic surgery. Int J Reliable Qual E-Healthcare 11(1). https://doi.org/10.4018/IJRQEH.295083
Jeevitha S, Amutha Prabha N (2020) Effective payload and improved security using HMT Contourlet transform in medical image steganography. Health Technol. (Berl). 10(1). https://doi.org/10.1007/s12553-018-00285-1
Kadhim IJ, Premaratne P, Vial PJ (2018) Secure image steganography using dual-tree complex wavelet transform block matching. https://doi.org/10.1109/ICECA.2018.8474616
Kadhim IJ, Premaratne P, Vial PJ (2020) Improved image steganography based on super-pixel and coefficient-plane-selection. Signal Processing 171. https://doi.org/10.1016/j.sigpro.2020.107481
Kalita M, Tuithung T, Majumder S (2019) A new steganography method using integer wavelet transform and least significant bit substitution. Comput J 62(11). https://doi.org/10.1093/comjnl/bxz014
Kanan HR, Nazeri B (2014) A novel image steganography scheme with high embedding capacity and tunable visual image quality based on a genetic algorithm. Expert Syst. Appl. 41(14). https://doi.org/10.1016/j.eswa.2014.04.022
Khamrui A, Gupta DD, Ghosh S, Nandy S (2017) A spatial domain image authentication technique using genetic algorithm. Commun Comput Info Sci 776. https://doi.org/10.1007/978-981-10-6430-2_45
Khan S, Bianchi T (2018) Ant colony optimization (ACO) based data hiding in image complex region. Int. J. Electr. Comput. Eng. 8(1). https://doi.org/10.11591/ijece.v8i1.pp379-389
Kieu TD, Chang CC (2011) A steganographic scheme by fully exploiting modification directions. Expert Syst. Appl. 38(8). https://doi.org/10.1016/j.eswa.2011.02.122
Kodovský J, Fridrich J, Holub V (2012) Ensemble classifiers for steganalysis of digital media. IEEE Trans Inform Forensics Sec 7(2). https://doi.org/10.1109/TIFS.2011.2175919
Kumar V, Kumar D (2018) A modified DWT-based image steganography technique. Multimed. Tools Appl. 77(11). https://doi.org/10.1007/s11042-017-4947-8
Kumar S, Muttoo SK (2010) Data hiding techniques based on wavelet-like transform and complex wavelet transforms. https://doi.org/10.1109/IPTC.2010.46
Laishram D, Tuithung T (2021) A novel minimal distortion-based edge adaptive image steganography scheme using local complexity: (BEASS). Multimed. Tools Appl. 80(1). https://doi.org/10.1007/s11042-020-09519-9
Lee CF, Chang CC, Xie X, Mao K, Shi RH (2018) An adaptive high-fidelity steganographic scheme using edge detection and hybrid hamming codes. Displays 53. https://doi.org/10.1016/j.displa.2018.06.001
Lu TC, Huang CC (2007) Lossless information hiding scheme based on pixels complexity analysis. https://doi.org/10.1109/SITIS.2007.60
Luo W, Huang F, Huang J (2010) Edge adaptive image steganography based on lsb matching revisited. IEEE Trans. Inf. Forensics Secur. 5(2). https://doi.org/10.1109/TIFS.2010.2041812
Maheswari SU, Hemanth DJ (2015) Frequency domain QR code based image steganography using Fresnelet transform. AEU - Int. J. Electron. Commun. 69(2). https://doi.org/10.1016/j.aeue.2014.11.004
Maheswari SU, Hemanth DJ (2015) Image steganography using hybrid edge detector and ridgelet transform. Def. Sci. J. 65(3). https://doi.org/10.14429/dsj.65.7871
Maniccam SS, Bourbakis N (2004) Lossless compression and information hiding in images. Pattern Recognit. 37(3). https://doi.org/10.1016/j.patcog.2003.08.010
Miri A, Faez K (2017) Adaptive image steganography based on transform domain via genetic algorithm. Optik (Stuttg). 145. https://doi.org/10.1016/j.ijleo.2017.07.043
Miri A, Faez K (2018) An image steganography method based on integer wavelet transform. Multimed. Tools Appl. 77(11). https://doi.org/10.1007/s11042-017-4935-z
Muhammad N, Bibi N, Mahmood Z, Kim DG (2015) Blind data hiding technique using the Fresnelet transform. Springerplus 4(1). https://doi.org/10.1186/s40064-015-1534-1
Muhuri PK, Ashraf Z, Goel S (2020) A Novel Image Steganographic Method based on Integer Wavelet Transformation and Particle Swarm Optimization. Appl. Soft Comput. J. 92. https://doi.org/10.1016/j.asoc.2020.106257
Mukherjee N, Paul G, Saha SK (2021) Two-point FFT-based high capacity image steganography using calendar based message encoding. Inf. Sci. (Ny). 552. https://doi.org/10.1016/j.ins.2020.11.044
Nipanikar SI, Hima Deepthi V, Kulkarni N (2018) A sparse representation based image steganography using Particle Swarm Optimization and wavelet transform. Alexandria Eng. J. 57(4). https://doi.org/10.1016/j.aej.2017.09.005
Pandey BK, Pandey D, Wairya S, Agarwal G, Dadeech P, Dogiwal SR, Pramanik S (2022) Application of integrated steganography and image compressing techniques for confidential information transmission In: Cyber Security and Network Security. Wiley, Eds
Patil V, Patil M (2018) Curvelet based ECG steganography for protection of data. Lecture Notes in Comput Vision Biomech 28
Pevný T, Bas P, Fridrich J (2010) Steganalysis by subtractive pixel adjacency matrix. IEEE Trans. Inf. Forensics Secur. 5(2). https://doi.org/10.1109/TIFS.2010.2045842
Prabha K, Sam S (2021) I. “lifting scheme and Schur decomposition based robust watermarking for copyright protection”. In: Sheth, a., Sinhal, a., Shrivastava, a., Pandey, a.K. (eds) intelligent systems. Algorithms for intelligent systems. Springer. Singapore. https://doi.org/10.1007/978-981-16-2248-9_15
Pramanik S, Bandyopadhyay SK (2014) Image steganography using wavelet transform and genetic algorithm. Int J Innovative Res Advanc Eng 1:1–4
Pramanik S, Bandyopadhyay SK (2014) An innovative approach in steganography. Scholars J Eng Technol:276–280.9
Pramanik S, Suresh Raja S (2019) Analytical study on security issues in steganography. Think-India 22(35):106–114
Pramanik S, Suresh Raja S (2020) A secured image steganography using genetic algorithm. Advan Math: Sci J 9(7):4533–4541
Pramanik S, Singh RP, Ghosh R, Bandyopadhyay SK (2020) A Unique Way to Generate Password at Random Basis and Sending it Using a New Steganography Technique. Indonesian J Electrical Eng Inform 8(3):525–531
Pramanik S, Singh RP, Ghosh R (2020) Application of bi-orthogonal wavelet transform and genetic algorithm in image steganography. Multimed. Tools Appl. 79:25–26. https://doi.org/10.1007/s11042-020-08676-1
Pramanik S, Samanta D, Ghosh R, Bandyopadhyay SK (2021) A New Combinational Technique in Image Steganography. Int J Info Sec Privacy 15(3):4 IGI Global
Sabeti V, Amerei S (2021) Secure and imperceptible image steganography in discrete wavelet transform using the XOR logical function and genetic algorithm. ISC Int. J. Inf. Secur
Sabeti V, S. Samavi, M. Mahdavi, and S. Shirani, “Steganalysis and payload estimation of embedding in pixel differences using neural networks,” Pattern Recognit., vol. 43, no. 1, 2010, https://doi.org/10.1016/j.patcog.2009.06.006.
Sabeti V, Samavi S, Shirani S (2013) An adaptive LSB matching steganography based on octonary complexity measure. Multimed. Tools Appl. 64(3). https://doi.org/10.1007/s11042-011-0975-y
Sajasi S, Eftekhari Moghadam AM (2015) An adaptive image steganographic scheme based on Noise Visibility Function and an optimal chaotic based encryption method. Appl. Soft Comput. J. 30. https://doi.org/10.1016/j.asoc.2015.01.032
Sarkar M, Pramanik S, Sahnwaj S (2020) Image Steganography Using DES-DCT Technique. Turkish J Comp Math Educ 11(2):906–913
Sathisha N, Priya R, Babu KS, Raja KB, Venugopal KR, Patnaik LM (2013) DTCWT based high capacity steganography using coefficient replacement and adaptive scaling. https://doi.org/10.1117/12.2051889
Shaukat A, Chaurasia M, Sanyal G (2016) A novel image steganographic technique using fast fourier transform. https://doi.org/10.1109/ICRTIT.2016.7569519
Singh S, Siddiqui TJ (2013) Robust image steganography using complex wavelet transform. https://doi.org/10.1109/MSPCT.2013.6782087
Subhedar MS, Mankar VH (2016) Image steganography using redundant discrete wavelet transform and QR factorization. Comput. Electr. Eng. 54. https://doi.org/10.1016/j.compeleceng.2016.04.017
Subhedar MS, Mankar VH (2018) Curvelet transform and cover selection for secure steganography. Multimed. Tools Appl. 77(7). https://doi.org/10.1007/s11042-017-4706-x
Thabit R, Khoo BE (2015) A new robust lossless data hiding scheme and its application to color medical images. Digit. Signal Process. A Rev. J. 38. https://doi.org/10.1016/j.dsp.2014.12.005
Wazirali R, Alasmary W, Mahmoud MMEA, Alhindi A (2019) An Optimized Steganography Hiding Capacity and Imperceptibly Using Genetic Algorithms. IEEE Access 7. https://doi.org/10.1109/ACCESS.2019.2941440
Wu DC, Tsai WH (2003) A steganographic method for images by pixel-value differencing. Pattern Recognit. Lett. 24:9–10. https://doi.org/10.1016/S0167-8655(02)00402-6
Xiao M, He Z (2015) High capacity image steganography method based on framelet and compressive sensing. In: MIPPR 2015: Multispectral Image Acquisition, Processing, and Analysis. 9811, https://doi.org/10.1117/12.2205279
Yadav GS, Ojha A (2018) Hamiltonian path based image steganography scheme with improved imperceptibility and undetectability. Appl. Soft Comput. J. 73. https://doi.org/10.1016/j.asoc.2018.08.034
Zhang X, Wang S (2004) Vulnerability of pixel-value differencing steganography to histogram analysis and modification for enhanced security. Pattern Recognit. Lett. 25(3). https://doi.org/10.1016/j.patrec.2003.10.014
Funding
The author did not receive any funding.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
None.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Pramanik, S. An adaptive image steganography approach depending on integer wavelet transform and genetic algorithm. Multimed Tools Appl 82, 34287–34319 (2023). https://doi.org/10.1007/s11042-023-14505-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-14505-y