Abstract
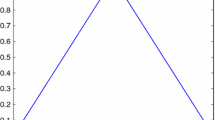
Digital images play a crucial role in data communication through the internet or any mode, but their security is a formidable task. Multiple image encryption approaches were conceived, employing chaotic maps to accomplish the security level of digital images. Chaotic maps are deemed suitable for encryption techniques because of their intrinsic properties of randomness, unpredictable behavior, and ergodicity. In this paper, we modify a chaotic map utilizing a fuzzy number and confer the enhancement in chaotic behavior through a bifurcation diagram. Further, we conceive a distinctive image encryption scheme that can uniform the pixel value of a plain image during the diffusion process with the help of a pseudo-random sequence generated from modifying the map. The sum of diffused pixels is used in the discretized tent map to annihilate the correlation among contiguous pixels of the diffused image. Finally, various security and statistical analysis exemplify that our proposed encryption scheme is fast, secure, and efficient against a plethora of threats.












Similar content being viewed by others
References
Bakhshandeh A, Eslami Z (2013) An authenticated image encryption scheme based on chaotic maps and memory cellular automata. Opt Lasers Eng 51 (6):665–673
Bashir Z, Rashid T, Zafar S (2016) Hyperchaotic dynamical system based image encryption scheme with time-varying delays. Pac Sci Rev A: Nat Sci Eng 18(3):254–260
Bashir Z, Wa̧tróbski J, Rashid T, Zafar S, Sałabun W (2017) Chaotic dynamical state variables selection procedure based image encryption scheme. Symmetry 9(12):312
Chakraverty S, Sahoo DM, Mahato NR (2019) Concepts of soft computing, Fuzzy and ANN with Programming. Springer, Singapore
Elmanfaloty RA, Abou-Bakr E (2020) An image encryption scheme using a 1D chaotic double section skew tent map. Complexity
Fridrich J (1994) On chaotic systems: fuzzified logistic mapping. Int J Gen Syst 22(4):369–380
Gao W, Idrees B, Zafar S, Rashid T (2020) Construction of nonlinear component of block cipher by action of modular group PSL (2, Z) on projective line PL (GF (2 8)). IEEE Access 8:136736–136749
Hanss M (2005) Applied fuzzy arithmetic. Springer, Berlin
Hong L, Sun JQ (2006) Bifurcations of fuzzy nonlinear dynamical systems. Commun Nonlinear Sci Numer Simul 11(1):1–12
Hua Z, Jin F, Xu B, Huang H (2018) 2D Logistic-Sine-coupling map for image encryption. Signal Process 149:148–161
Huang CK, Nien HH (2009) Multi chaotic systems based pixel shuffle for image encryption. Opt Commun 282(11):2123–2127
Idress B, Zafar S, Rashid T, Gao W (2020) Image encryption algorithm using S-box and dynamic Henon bit level permutation. Multimed Tools Appl 79 (9):6135–6162
Kanso A (2011) Self-shrinking chaotic stream ciphers. Commun Nonlinear Sci Numer Simul 16(2):822–836
Li S, Ding W, Yin B, Zhang T, Ma Y (2018) A novel delay linear coupling logistics map model for color image encryption. Entropy 20(6):463
Malik MGA, Bashir Z, Iqbal N, Imtiaz MA (2020) Color image encryption algorithm based on hyper-chaos and DNA computing. IEEE Access 8:88093–88107
Matthews R (1989) On the derivation of a “chaotic” encryption algorithm. Cryptologia 13(1):29–42
Malik DS, Shah T (2020) Color multiple image encryption scheme based on 3Dchaotic maps. Math Comput Simul 178:646–666
Masuda N, Aihara K (2002) Cryptosystems with discretized chaotic maps. IEEE Transactions on Circuits and Systems I: Fundamental Theory and Applications 49(1):28–40
Moysis L, Volos C, Jafari S, Munoz-Pacheco JM, Kengne J, Rajagopal K, Stouboulos I (2020) Modification of the logistic map using fuzzy numbers with application to pseudorandom number generation and image encryption. Entropy 22(4):474
Niu Y, Zhou Z, Zhang X (2020) An image encryption approach based on chaotic maps and genetic operations. Multimed Tools Appl 79:25613–25633
Pak C, Huang L (2017) A new color image encryption using combination of the 1D chaotic map. Signal Process 138:129–137
Rehman AU, Firdous A, Iqbal S, Abass ZM, Shahid MA, Wang H, Ullah F (2020) A Color Image encryption algorithm based on one time key, chaos theory, and concept of rotor machine. IEEE Access 8:172275–172295
Tromer E, Osvik DA, Shamir A (2010) Efficient cache attacks on AES, and countermeasures. J Cryptol 23(1):37–71
Wang X, Zhu X, Zhang Y (2018) An image encryption algorithm based on Josephus traversing and mixed chaotic map. IEEE Access 6:23733–23746
Wei Z (2011) Dynamical behaviors of a chaotic system with no equilibria. Phys Lett A 376(2):102–108
Zhang G, Ding W, Li L (2020) Image encryption algorithm based on tent delay-sine cascade with logistic map. Symmetry 12(3):355
Zhang LY, Liu Y, Pareschi F, Zhang Y, Wong KW, Rovatti R, Setti G (2017) On the security of a class of diffusion mechanisms for image encryption. IEEE Trans Cybern 48(4):1163–1175
Zhu S, Zhu C (2020) Secure image encryption algorithm based on hyperchaos and dynamic DNA coding. Entropy 22(7):772
Acknowledgements
The authors are grateful to the reviewers for their comments and suggestions to improve the manuscript.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
Conflict of Interests] The authors declare that they have no conflict of interest.
Additional information
Availability of data and materials
All data generated or analyzed during this study are included in this manuscript.
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Muhammad Akraam, Tabasam Rashid and Sohail Zafar contributed equally to this work.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Akraam, M., Rashid, T. & Zafar, S. An image encryption scheme proposed by modifying chaotic tent map using fuzzy numbers. Multimed Tools Appl 82, 16861–16879 (2023). https://doi.org/10.1007/s11042-022-13941-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13941-6