Abstract
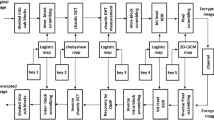
A secured compressed sensing (CS) systems design approach uses a novel deterministic sensing matrix to sense and transmit fingerprint images. The performance of the CS system was studied in detail by varying CS and security parameters. The sampling and sparse coefficient are the parameters considered from compressed sensing, whereas the encryption key is from the security scheme. The simultaneous compression and encryption has been achieved by multiplying the sparse modeled data with the proposed deterministic partial bounded orthogonal sensing matrix. A chaotic model-based permutation is applied to scramble the DCT matrix rows to build the sensing matrix. Recovering and decryption of the compressed image are accomplished with the help of the L1 optimization method. The experimental test shows that a sparse vector of 121 widths has been recovered by taking about 25 samples. This indicates that up to 1 : 5 compression ratio is supported without damaging the fingerprint minutiae. If only compression is required without encryption, up to a 1 : 16 ratio can be achieved. The peak signal-to-noise ratio (PSNR) is 27.65 dB for both compression ratios under fulfilments of all necessary security requirements. The 7.20 value of the entropy, histogram analysis, and the correlation analysis show the proposed scheme possesses adequate randomness. Furthermore, the ability of the system resistance against attacks is proved by 100% NPCR (Net Pixel Change Rate) and 0.92% UACI (Unified Average Changing Intensity) values.














Similar content being viewed by others
References
Achanta SDM, Karthikeyan T, Vinoth Kanna R (2020) A wireless IOT system towards gait detection technique using FSR sensor and wearable IOT devices. Int J Intell Unmanned Syst 8(1):43–54. https://doi.org/10.1108/IJIUS-01-2019-0005
Achanta SDM, Karthikeyan T, Vinothkanna R (2019) A novel hidden Markov model-based adaptive dynamic time warping (HMDTW) gait analysis for identifying physically challenged persons. Soft Comput 23(18):8359–8366. https://doi.org/10.1007/s00500-019-04108-x
Aharon M, Elad M, Bruckstein AM (2006) On the uniqueness of overcomplete dictionaries, and a practical way to retrieve them. Linear Algebra Appl. https://doi.org/10.1016/j.laa.2005.06.035
Aharon M, Elad M, Bruckstein A (2006) K-SVD: an algorithm for designing overcomplete dictionaries for sparse representation. IEEE Trans Signal Process 54:4311–4322. https://doi.org/10.1109/TSP.2006.881199
Allen JB, Rabiner LR (1977) A unified approach to short-time fourier analysis and synthesis. Proc IEEE 65:1558–1564. https://doi.org/10.1109/PROC.1977.10770
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurc Chaos. https://doi.org/10.1142/S0218127406015970
Antonini M, Barlaud M, Mathieu P, Daubechies I (1992) Image coding using wavelet transform. IEEE Trans Image Process 1(2):205–220
Bakiri M, Guyeux C, Couchot JF, Oudjida AK (2018) Survey on hardware implementation of random number generators on FPGA: theory and experimental analyses. Comput Sci Rev 27:135–153. https://doi.org/10.1016/j.cosrev.2018.01.002
Cand‘es E, Romberg J (2005) 1-magic: Recovery of Sparse Signals via Convex Programming, Caltech. https://candes.su.domains/software/l1magic/atlast. Accessed 10 Dec 2021
Candès EJ (2008) The restricted isometry property and its implications for compressed sensing. Comptes Rendus Math. https://doi.org/10.1016/j.crma.2008.03.014
Candès EJ, Donoho DL (2004) New tight frames of curvelets and optimal representations of objects with piecewise C 2 singularities. Commun Pure Appl Math 57:219–266. https://doi.org/10.1002/cpa.10116
Candès EJ, Romberg J, Tao T (2006) Robust uncertainty principles: exact signal reconstruction from highly incomplete frequency information. IEEE Tran Inf Theory. https://doi.org/10.1109/TIT.2005.862083
Chao L, Han J, Yan L, Sun L, Huang F, Zhu ZB, Wei S, Ji H, Ma D (2020) Fast compressed sensing analysis for imaging reconstruction with primal dual interior point algorithm. Opt Lasers Eng 129. https://doi.org/10.1016/j.optlaseng.2020.106082
Chen G, Maggioni M (2010) Multiscale geometric wavelets for the analysis of point clouds. In: 2010 44th Annual Conference on Information Sciences and Systems, CISS. pp 1–6. https://doi.org/10.1109/CISS.2010.5464843
Djelouat H, Amira A, Bensaali F, Boukhennoufa I (2020) Secure compressive sensing for ECG monitoring. Comput Secur 88:101649. https://doi.org/10.1016/j.cose.2019.101649
Do TT, Gan L, Nguyen NH, Tran TD (2012) Fast and efficient compressive sensing using structurally random matrices. IEEE Trans Signal Process 60(1):139–154. https://doi.org/10.1109/TSP.2011.2170977
Donoho DL (2006) Compressed sensing. IEEE Trans Inf Theory. https://doi.org/10.1109/TIT.2006.871582
Elad M, Bruckstein AM (2002) A generalized uncertainty principle and sparse representation in pairs of bases. IEEE Trans Inf Theory. https://doi.org/10.1109/TIT.2002.801410
Fan H, Li M, Mao W (2017) VQ-Based compressive sensing with high compression quality. Electron Lett 53(17):1196–1198. https://doi.org/10.1049/el.2017.1321
Fan H, Zhou K, Zhang E, Wen W, Li M (2020) Subdata image encryption scheme based on compressive sensing and vector quantization. Neural Comput Applic 32(16):12771–12787. https://doi.org/10.1007/s00521-020-04724-x
Fishman GS, Moore LR III (1986) Erratum: an exhaustive analysis of multiplicative congruential random number generators with modulus 231 − 1, SIAM J Sci Stat Comput. https://doi.org/10.1137/0907072
Gangopadhyay D, Allstot EG, Dixon AMR, Natarajan K, Gupta S, Allstot DJ (2014) Compressed sensing analog front-end for bio-sensor applications, IEEE J Solid-State Circ. https://doi.org/10.1109/JSSC.2013.2284673
Hashad FG, Zahran O, El-Rabaie ESM et al (2019) Fusion-based encryption scheme for cancelable fingerprint recognition. Multimed Tools Appl 78:27351–27381. https://doi.org/10.1007/s11042-019-7580-xhttps://doi.org/10.1007/s11042-019-7580-x
Hopper T, Brislawn C, Bradley J (1993) –WSQ gray-scale fingerprint image compression specification, Federal Bureau of Investigation, Criminal Justice Information Services, Washington, DC, USA, Tech. Rep. IAFIS-IC-0110-V2
Hopper T, Preston F (1992) Compression of grey-scale fingerprint images. In: Proceedings DCC ’92. Data Compression Conference. pp 309–318. https://doi.org/10.1109/DCC.1992.227450
Hsiung YS, Lu MSC (2011) A CMOS capacitive pressure sensor chip for fingerprint detection. In: 2011 16th International Solid-State Sensors, Actuators Microsystems Conference TRANSDUCERS’11. pp 24–27
Hu G, Xiao D, Wang Y, Xiang T (2017) An image coding scheme using parallel compressive sensing for simultaneous compression-encryption applications. J Vis Commun Image Represent 44:116–127. https://doi.org/10.1016/j.jvcir.2017.01.022
Javidi B (1999) Noise performance of double-phase encryption compared to XOR encryption. Opt Eng. https://doi.org/10.1117/1.602074
Javidi B (2000) Optical encryption using a joint transform correlator architecture. Opt Eng. https://doi.org/10.1117/1.1304844
Jiang X, Tang HY, Lu Y, Ng EJ, Tsai JM, Boser BE, Horsley DA (2017) Ultrasonic fingerprint sensor with transmit beamforming based on a PMUT array bonded to CMOS circuitry. IEEE Trans Ultrasonics, Ferroelectrics Frequency Control 64(9):1401–1408. https://doi.org/10.1109/TUFFC.2017.2703606
Jung SM, Nam JM, Yang DH, Lee MK (2005) A CMOS integrated capacitive fingerprint sensor with 32-bit RISC microcontroller. IEEE J Solid-State Circ 40(8):1745–1750
Kharratzadeh M, Sharifnassab A, Babaie-Zadeh M (2017) Invariancy of sparse recovery algorithms. IEEE Trans Inf Theory 63:3333–3347. https://doi.org/10.1109/TIT.2017.2686428
Komarinski P (2005) Automated fingerprint identification systems (AFIS), Elsevier Science Technology
Kreutz-delgado K, Murray JF, Sejnowski TJ (2003) Dictionary learning algorithms for sparse representation kenneth. Neural Comput 15. https://doi.org/10.1162/089976603762552951
Kwon K, Nam I, Lee K (2016) A three-terminal n+-p-n+ silicon CMOS light-emitting device for the new fully integrated optical-type fingerprint recognition system. J Disp Technol 12(1):77–81. https://doi.org/10.1109/JDT.2015.2456641
Li R (2020) Fingerprint-related chaotic image encryption scheme based on blockchain framework Multimed Tools Appl. https://doi.org/10.1007/s11042-020-08802-z
Li X, Cai J (2007) Robust transmission of JPEG2000 encoded images over packet loss channels. In: Proceedings of the 2007 IEEE International Conference on Multimedia and Expo, ICME. p 2007. https://doi.org/10.1109/icme.2007.4284808
Liu JC, Hsiung YS, Lu MSC (2012) A CMOS micromachined capacitive sensor array for fingerprint detection. IEEE Sens J 12(5):1004–1010
Liu D, Wang Q, Zhang Y, Liu X, Lu J, Sun J (2019) FPGA-Based real-time compressed sensing of multichannel EEG signals for wireless body area networks. Biomed Signal Process Control 49:221–230. https://doi.org/10.1016/j.bspc.2018.12.019
Mairal J, Bach F, FRANCISBACH J, Sapiro G (2010) Ponce JEANPONCE online learning for matrix factorization and sparse coding. J Mach Learn Res 11:19–60. http://www.jmlr.org/papers/volume11/mairal10a/mairal10a.pdf
Mairal J, Bach F, Ponce J, Sapiro G (2010) Online learning for matrix factorization and sparse coding, J Mach Learn Res. https://doi.org/10.1145/1756006.1756008
Mallat S (2009) A Wavelet Tour of Signal Processing. https://doi.org/10.1016/B978-0-12-374370-1.X0001-8
Mallat SG, Zhang Z (1993) Matching pursuits with time-frequency dictionaries, IEEE Trans Signal Process. https://doi.org/10.1109/78.258082
Maltoni D, Maio D, Jain AK, Prabhakar S (2009) Handbook of Fingerprint Recognition. Springer Science & Business Media. p 216. ISBN 978-1-84882-254-2
May RM (1976) Simple mathematical models with very complicated dynamics. Nature. https://doi.org/10.1038/261459a0
Mehta G, Dutta MK, Karasek J, Kim PS (2013) An efficient and lossless fingerprint encryption algorithm using Henon map & Arnold transformation. In: 2013 International Conference on Control Communication and Computing (ICCC). pp 485–489. https://doi.org/10.1109/ICCC.2013.6731703
Needell D, Tropp JA (2009) CosaMP: iterative signal recovery from incomplete and inaccurate samples. Appl Comput Harmon Anal. https://doi.org/10.1016/j.acha.2008.07.002
Orsdemir A, Altun HO, Sharma G, Bocko MF (2008) On the security and robustness of encryption via compressed sensing. In: Proceedings of the IEEE Military Communications Conference, MILCOM. https://doi.org/10.1109/MILCOM.2008.4753187
Pati YC, Rezaiifar R, Krishnaprasad PS (1993) Orthogonal matching pursuit: recursive function approximation with applications to wavelet decomposition. In: Conference Rec Asilomar Conference on Signals, Systems, and Computers. https://doi.org/10.1109/acssc.1993.342465
Polania LF, Carrillo RE, Blanco-Velasco M, Barner KE (2015) Exploiting prior knowledge in compressed sensing wireless ECG systems, IEEE J Biomed Heal Inform. https://doi.org/10.1109/JBHI.2014.2325017
Polat Ö, Kayhan SK (2018) High-speed FPGA implementation of orthogonal matching pursuit for compressive sensing signal reconstruction. Comput Electr Eng 71:173–190. https://doi.org/10.1016/j.compeleceng.2018.07.017
Rani M, Dhok SB, Deshmukh RB (2018) A systematic review of compressive sensing: concepts, implementations and applications. IEEE Access. Institute of Electrical and Electronics Engineers Inc. https://doi.org/10.1109/ACCESS.2018.2793851
Ravelomanantsoa A, Rabah H, Rouane A (2015) Compressed sensing: a simple deterministic measurement matrix and a fast recovery algorithm. IEEE Trans Instrum Meas 64:3405–3413. https://doi.org/10.1109/TIM.2015.2459471
Rudelson M, Vershynin R (2008) On sparse reconstruction from Fourier and Gaussian measurements. Commun Pur Appl Math 61(8):1025–1045. https://doi.org/10.1002/cpa.20227
Ruelle D, Takens F (1971) On the nature of turbulence. Commun Math Phys. https://doi.org/10.1007/BF01646553
Sato N, Shigematsu S, Morimura H, Yano M, Kudou K, Kamei T, Machida K (2005) Novel surface structure and its fabrication process for MEMS fingerprint sensor. IEEE Trans Electron Devices 52:1026–1032. https://doi.org/10.1109/TED.2005.846342
(2001) ScientificWorking Group on Friction Ridge Analysis, Study and Technology (SWGFAST): Friction Ridge Digital Imaging Guidelines, 1 edn. http://www.theiai.org/guidelines/swgfast/. Accessed 12 Dec 2021
Shah AA, Parah SA, Rashid M, Elhoseny M (2020) Efficient image encryption scheme based on generalized logistic map for real time image processing. J Real-Time Image Process 17:2139–2151. https://doi.org/10.1007/s11554-020-01008-4
Shao G, Wu Y, Yong A, Liu X, Guo T (2014) Fingerprint compression based on sparse representation. IEEE Trans Image Process 23(2):489–501. https://doi.org/10.1109/TIP.2013.2287996
Sharma A, Shwetank A, Praveena C (2020) A novel image compression based method for multispectral fingerprint biometric system. Procedia Comput Sci 171:1698–1707. (Elsevier)
Shen Q, Liu W, Lin Y, Zhu Y (2019) Designing an image encryption scheme based on compressive sensing and non-uniform quantization for wireless visual sensor networks. Sensors (Switzerland) 19(14). https://doi.org/10.3390/s19143081
Sivapalan S, Rana RK, Chen D, Sridharan S, Denmon S, Fookes C (2011) Compressive sensing for gait recognition. In: Proceedings - 2011 international conference on digital image computing: techniques and applications, DICTA 2011 (pp 567–571). IEEE Computer Society. https://doi.org/10.1109/DICTA.2011.101
Skodras A, Christopoulos C, Ebrahimi T (2001) The JPEG 2000 still image compression standard. IEEE Signal Process Mag 18(5):36–58
Sun C, Li W, Chen W (2017) A compressed sensing based method for reducing the sampling time of a high resolution pressure sensor array system. Sensors (Switzerland) 17(8). https://doi.org/10.3390/s17081848
Tang Y, Zhao M, Li L (2020) Secure and efficient image Compression-Encryption scheme using new chaotic structure and compressive sensing. Secur Commun Netw 2020. https://doi.org/10.1155/2020/6665702
Tawfic I, Kayhan S (2015) Compressed sensing of ECG signal for wireless system with new fast iterative method. Comput Methods Programs Biomed. https://doi.org/10.1016/j.cmpb.2015.09.010
Thomos N, Boulgouris NV, Strintzis MG (2006) Optimized transmission of JPEG2000 streams over wireless channels. IEEE Trans Image Process. https://doi.org/10.1109/TIP.2005.860338
Vidyasagar M (2016) A tutorial introduction to compressed sensing. In: 2016 55th IEEE Conference on Decision and Control (CDC). pp 5091–5104. https://doi.org/10.1109/CDC.2016.7799048
Wang Z, Bovik AC, Sheikh HR (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans Image Process. https://doi.org/10.1109/TIP.2003.819861
Xie Y, Yu J, Guo S, Ding Q, Wang E (2019) Image encryption scheme with compressed sensing based on new three-dimensional chaotic system. Entropy 21(9). https://doi.org/10.3390/e21090819
Zhang Y, Zhang LY, Zhou J, Liu L, Chen F, He X (2016) A review of compressive sensing in information security field. IEEE Access. https://doi.org/10.1109/ACCESS.2016.2569421
Zhang Y, Zheng CH, Tanno N (2002) Optical encryption based on iterative fractional Fourier transform. Opt Commun. https://doi.org/10.1016S0030-4018(02)01113-6
Zhao C, Wu X, Huang L, Yao Y, Chang YC (2014) Compressed sensing based fingerprint identification for wireless transmitters. Sci World J 2014. https://doi.org/10.1155/2014/473178
Zhao C, Wu X, Huang L, Yao Y, Chang YC (2014) Compressed sensing based fingerprint identification for wireless transmitters. Sci World J 2014. https://doi.org/10.1155/2014/473178
Author information
Authors and Affiliations
Contributions
Workneh Wolde Hailemariam: Design methodology, simulation work, writing and editing the manuscript draft. Pallavi Gupta: supervision.
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare that they have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Hailemariam, W.W., Gupta, P. Compressed sensing based fingerprint imaging system using a chaotic model-based deterministic sensing matrix. Multimed Tools Appl 82, 6885–6915 (2023). https://doi.org/10.1007/s11042-022-13444-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13444-4