Abstract
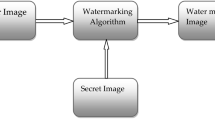
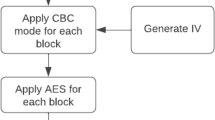
The wide range of applications of 3D meshes and the birth of very high-speed networks for storing 3D models in remote multimedia databases have made the copyright protection of these objects a necessity. In order to contribute to safe sharing, transfer and indexing of 3D multiresolution meshes, a new crypto-watermarking approach is proposed based on spherical harmonics and AES encryption algorithm. Data to be inserted, in this case, is a grayscale image already encrypted using AES256 algorithm. The host mesh, to be watermarked, is decomposed using spherical harmonics to extract frequency coefficients and to compute optimal order for reconstruction. These coefficients undergo two watermarking iterations. During each round, modulation, insertion using quantification method and demodulation steps are implemented. Finally, reconstruction of watermarked mesh using a minimal number of coefficients is conducted. The results established show clearly that our algorithm protects the mesh quality even with the insertion of a large amount of information (a whole image) while ensuring real time execution. The application of various attacks (noise addition, coordinate quantization, smoothing, translation, rotation, uniform scaling and compression) to a watermarked mesh did not prevent the correct retrieval of inserted information. Our approach presents then an enhancement compared to existing ones.











Similar content being viewed by others
Code Availability
The code concerning this study is available from the corresponding author upon reasonable request.
Abbreviations
- 3D:
-
Three Dimension
- AES:
-
Advanced Encryption Standard
- MSQE:
-
Mean SQuare Erreur
- PSNR:
-
Peak Signal to Noise Ratio
- SHs:
-
Spherical Harmonics
- SHsDecomposition:
-
Spherical Harmonics Decomposition
- SHsReconst:
-
Spherical Harmonics Reconstruction
- SHsCoeff:
-
Spherical Harmonics Coefficients
- US:
-
Uniform scaling
References
Ali A, Ahmad M, Alaa A (2017) Crypto-Watermarking Of transmitted medical images. J Digit Imaging 30(1):26–38
Basyoni L, Saleh HI, Abdelhalim MB (2015) Enhanced watermarking scheme for 3D mesh models. In: CIT 2015 The 7th international conference on information technology, pp 612–619
Borra S, Thanki R (2020) Crypto-watermarking scheme for tamper detection of medical images. Computer Methods in Biomechanics and Biomedical Engineering: Imaging and Visualization 8(4):345– 355
Bülow T (2004) Spherical diffusion for 3-D surface smoothing. IEEE Trans Pattern Anal 26(12):1650–1654
Chao HL, Min WC, Jyun YC, Cheng WY, Wei YH (2013) A high-capacity distortion-free information hiding algorithm for 3D polygon models. Int J Innov Comput Inf Control 9(3):1321–1335
Céline R, Frédéric P (2011) Remaillage semi-régulier pour les maillages surfaciques triangulaires: Un état de l’art. Revue Electronique Francophone d’Informatique Graphique, Association Française d’Informatique Graphique 5(11):27–40
Che X, Gao Z (2011) Watermarking algorithm for 3D mesh based on multi-scale radial basis functions. Int J Parallel Emergent Distrib Syst 27(2):133–141
Federal Information Processing Standards Publication 197, Announcing the ADVANCED ENCRYPTION STANDARD (AES), 2001
Frederic P, Marc A (2006) Mean square error approximation for wavelet based semi-regular mesh compression. IEEE Trans Vis Comput Graph 12(4):649–657
Hamidi M, El Haziti M, Cherifi H, Aboutajdine D (2017) A robust blind 3-D mesh watermarking based on wavelet transform for copyright protection. In: International conference on advanced technologies for signal and image processing (ATSIP), pp 1–6
Hitendra G, Krishna KK, Manish G, Suneeta A (2014) Uniform selection of vertices for watermark embedding in 3-D polygon mesh using IEEE754 floating point representation. In: International conference on communication systems and network technologies, pp 788–792
Jallouli M, Belhaj khelifa W, Ben Mabrouk A, Mahjoub MA (2020) Toward recursive spherical harmonics issued bi-filters: Part II: An associated spherical harmonics entropy for optimal modeling. Soft Comput 24:5231–5243
Jen-Tse W, Yi-Ching Ch, Shyr-Shen Y, Chun-Yuan Y (2014) Hamming code based watermarking scheme for 3D model verification. International symposium on computer, Consumer and Control, pp 1095–1098
Jing L, Yinghui W, Ye L, Ruijiao L, Jinlei C (2017) A robust and blind 3D watermarking algorithm using multiresolution adaptive parameterization of surface. Neurocomputing 237(C):304–315
Khalil OH, Elhadad A, Ghareeb A (2020) A blind proposed 3D mesh watermarking technique for copyright protection. Imaging Sci J 68(2):90–99
Kohli R, Kumar M (2013) FPGA Implementation of cryptographic algorithms using multi-encryption technique. Int J Adv Res Comput Sci Softw Eng 3(5):112–120
Kohli R, Kumar M (2013) Optimized on system analysis using AES and X-tea. Int J Adv Res Comput Sci Softw Eng 3(2):18–25
Kumar BJS, Roshni Raj VK, Nair A (2017) Comparative Study on AES and RSA Algorithm for Medical images. In: International conference on communication and signal processing, pp 501–504
Li L, Hangkai L, Wenqiang Y, Xiaoqing F, Jianfeng L, Chin-Chen C (2018) A watermarking mechanism with high capacity for three-dimensional mesh objects using integer planning. IEEE Multimed 25:49–64
Mateo MJ, Callaghan DJ, Donnell CP (2010) Comparison between red-green-blue imaging and visiblenear infrared reflectance as potential process analytical tools for monitoring syneresis. J Dairy Sci 93(5):1882–1889
Mehan V (2018) Semi-blind secure watermarking based on integration of AES and ECC in DCT domain. J Adv Inf Fusion 13(1):106–121
Muna ML (2021) 3D model watermarking based on wavelet transform. Iraqi J Sci 62(12):4999–5007
Khalil OH, Ahmed E, Ghareeb A (2019) A blind proposed 3D mesh watermarking technique for copyright protection. Imaging Sci J 68(2):90–99
Sayahi I, Elkefi A, Ben Amar C (2019) Crypto-watermarking system for safe transmission of 3D multiresolution meshes. Int J Multimed Tools Appli 78:13877–13903
Sayahi I, Elkefi A, Ben Amar C (2016) A multi-resolution approach for blind watermarking of 3D meshes using scanning spiral method. Int Conf Comput Intell Secur Inform Syst 527:526–537
Shannon C (1948) A mathematical theory of communication. Bell System Technical Journal 27:379–423
Sharma N, Panda J (2020) Statistical watermarking approach for 3D mesh using local curvature estimation. IET Inf Secur 14(6):745–753
Sridhar P, Sathiya RR (2017) Crypto-watermarking for secure and robust transmission of multispectral images. In: International conference on computation of power, energy information and communication, pp 153–163
Wang K, Lavoué G, Denis F, Baskurt A Tatouage robuste et aveugle de maillage 3D base sur les moments volumiques. CORESA’09: COmpression et REprésentation des Signaux Audiovisuels, (2009), 6 pages
Yang Y, Pintus R, Rushmeier R, Ivrissimtzis I (2016) A 3D steganalytic algorithm and Steganalysis-Resistant watermarking. IEEE Transactions on Visualization and Computer Graphics 23(2):1002–1013
Yuan YT (2016) An efficient 3D information hiding algorithm based on sampling concepts. Multimed Tools Appl 75:7891–7907
Zaid AO, Hachani M, Puech W (2015) Wavelet-based high-capacity watermarking of 3-D irregular meshes. Multimed Tools Appl 74:5897–5915
Zhou X, Zhu Q (2012) A DCT-based dual watermarking algorithm for three-dimensional mesh models. In: International conference on consumer electronics, communications and networks, pp 1509–1513
Funding
The authors did not receive support from any organization for this work.
Author information
Authors and Affiliations
Contributions
The author confirms sole responsibility for the following: study and programming, data collection, analysis and interpretation of results, and manuscript preparation.
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare no conflict of interest for the present work.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Jallouli, M., Sayahi, I. & Mabrouk, A.B. Robust crypto-watermarking approach based on spherical harmonics and AES algorithm for 3D mesh safe transmission. Multimed Tools Appl 81, 38543–38567 (2022). https://doi.org/10.1007/s11042-022-13113-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13113-6