Abstract
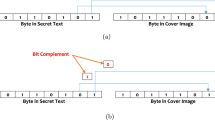
An unauthorized leak of information that is not tolerable always implies inadequate or poor security measures of information. Globally, the hospitality industry has in the recent past been targeted by cybercrimes. Management of cybercrimes are divided into facets like policies of security frameworks, cyber-threats, and management appreciating the value of Information Technology investment. These aspects possess a notable influence on the information security of an organization. This study’s purpose is to examine cybersecurity activities of network threats, electronic information, and the techniques of preventing cybercrime in hotels. Helping Chief Information Officers (CIO) and the directors of information technology is the main aim of the research to improve policy for electronic information security in the hospitality industry and recommending several tools and techniques to stabilize the network of computers. Further, to protect personal information disclosure for the visitors, an information hiding technique has been proposed by utilizing the least significant bits (LSBs) of each pixel of grayscale image adopting XOR features of the host image (HI) pixels. Also, the proposed technique successfully withstands various steganalysis attacks like regular and singular (RS) attack, pixel difference histogram (PDH) attack, and subtractive pixel adjacency matrix (SPAM) steganalysis.





Similar content being viewed by others
References
Abu‐Hashem M, Gutub A (2021) Efficient computation of Hash Hirschberg protein alignment utilizing hyper threading multi‐core sharing technology. CAAI Transactions on Intelligence Technology. IET (IEE) - Wiley. https://doi.org/10.1049/cit2.12070
Almehmadi E, Gutub A (2022) Novel arabic e-text watermarking supporting partial dishonesty based on counting-based secret sharing. Arab J Sci Eng 47(2):2585–2609. https://doi.org/10.1007/s13369-021-06200-7
Almutairi S, Gutub A, Al-Ghamdi M (2019) Image steganography to facilitate online students account system. Rev Bus Technol Res (RBTR) 16(2):43–49. https://doi.org/10.13140/RG.2.2.32048.30727
Al-Roithy B, Gutub A (2021) Remodeling randomness prioritization to boost-up security of RGB image encryption. Multimed Tools Appl (MTAP) 80:28521–28581. https://doi.org/10.1007/s11042-021-11051-3
Al-Shaarani F, Gutub A (2022) Increasing participants using counting-based secret sharing via involving matrices and practical steganography. Arab J Sci Eng 47(2):2455–2477. https://doi.org/10.1007/s13369-021-06165-7
Al-Shaarani F, Gutub A (2021) Securing matrix counting-based secret-sharing involving crypto steganography. J King Saud Univ - Comput Inf Sci. https://doi.org/10.1016/j.jksuci.2021.09.009
Al-Shaarani F, Basakran N, Gutub A (2020) Sensing e-banking cybercrimes vulnerabilities via smart information sciences strategies. RAS Eng Technol 1(1):1–9
Bin-Hureib ES, Gutub A (2020) Enhancing medical data security via combining elliptic curve cryptography and image steganography. Int. J. Comput. Sci. Netw Secur 20(8):1–8. https://doi.org/10.22937/IJCSNS.2020.20.08.1
Database (2021) http://sipi.usc.edu/database/database.php. Accessed on 03-05-2021
Enescu I (2016) Unwanted guests: How hackers are targeting the hospitality industry. http://www.naylornetwork.com/hoc-nwl/pdf/Cybersecurity_Article_for_Roomers_Magazine.pdf. Accessed 1 Dec 2020
Facchini SW (2016) Cybersecurity and the hospitality industry. https://www.reviewjournal.com/opinion/cybersecurity-and-the-hospitality-industry.
Fridrich J, Kodovsky J (2012) Rich models for steganalysis of digital images. IEEE Transactions on Information Forensics and Security 7(3):868–882
Gutub A (2010) Pixel indicator technique for RGB image steganography. Journal of Emerging Technologies in Web Intelligence 2(1):56–64. https://doi.org/10.4304/jetwi.2.1.56-64
Gutub A (2022) Adopting counting-based secret-sharing for e-Video Watermarking allowing Fractional Invalidation. Multimed Tools Appl 81(7):9527–9547. https://doi.org/10.1007/s11042-022-12062-4
Gutub A (2022) Regulating watermarking semi-authentication of multimedia audio via counting-based secret sharing. Pamukkale University Journal of Engineering Sciences. https://doi.org/10.5505/pajes.2021.54837
Gutub A (2022) Watermarking images via counting-based secret sharing for lightweight semi-complete authentication. Int J Inf Secur Priv 16(1):1–18. https://doi.org/10.4018/IJISP.2022010118
Gutub A, Al-Shaarani F (2020) Efficient implementation of multi-image secret hiding based on LSB and DWT steganography comparisons. Arab J Sci Eng 45(4):2631–2644. https://doi.org/10.1007/s13369-020-04413-w
Gutub A, Fattani M (2007) A novel arabic text steganography method using letter points and extensions. International Journal of Computer, Electrical, Automation, Control and Information Engineering. 1(3):502–505. https://doi.org/10.5281/zenodo.1061621
Gutub A, Al-Juaid N, Khan E (2019) Counting-based secret sharing technique for multimedia applications. Multimed Tools Appl 78(5):5591–5619. https://doi.org/10.1007/s11042-017-5293-6
Gwebu K, Barrows CW (2020) Data breaches in hospitality: is the industry different? J Hosp Tour Technol 11(3):511–527. https://doi.org/10.1108/JHTT-11-2019-0138
Hassan FS, Gutub A (2020) Efficient reversible data hiding multimedia technique based on smart image interpolation. Multimed Tools Appl 79(39):30087–30109. https://doi.org/10.1007/s11042-020-09513-1
Hemavathy A (2005) Cybercriminal Activity. https://cseweb.ucsd.edu//~cfleizac/WhiteTeam-CyberCrime.pdf. Accessed 1 Apr 2022
Hilliard TW, Baloglu S (2008) Safety and security as part of the hotel services cape for meeting planners. Int Journal of Convention & Event Tourism 9(1):15–34
Ip C, Leung R, Law R (2011) Progress and development of information and communication technologies in hospitality. Int J Contemp Hosp Manag 23(4):533–551. https://doi.org/10.1108/09596111111130029
Kheshaifaty N, Gutub A (2021) Engineering graphical captcha and AES crypto hash functions for secure online authentication. J Eng Res. https://doi.org/10.36909/jer.13761
Khodaei M, Faez K (2012) New adaptive steganographic method using least-significant-bit substitution and pixel-value differencing. IET Image Process 6(6):677–686
King D (2017) Hotels shown to be susceptible to cybercrime. Travel Weekly
Koegler S. (2017) How Hotel Cybersecurity Keeps Guests and Data Secure. https://securityintelligence.com/how-hotel-cybersecurity-keeps-guests-and-data-secure/
Liao X, Guo S, Yin J, Wang H, Li X, Sangaiah AK (2018) New cubic reference table based image steganography. Multimed Tools Appl 77(8):10033–10050
Liao X, Li K, Zhu X, Liu KR (2020) Robust detection of image operator chain with two-stream convolutional neural network. IEEE J Sel Top Signal Process 14(5):955–968. [Accessed: 1st Dec 2020]
Liao X, Yin J, Chen M, Qin Z (2020) Adaptive payload distribution in multiple images steganography based on image texture features. IEEE Trans Dependable Secure Comput. [Accessed: 1st Dec 2020] https://doi.org/10.1109/TDSC.2020.3004708
Liao X, Yin J, Guo S, Li X, Sangaiah AK (2018) Medical JPEG image steganography based on preserving inter-block dependencies. Comput Electr Eng 67:320–329
Liao X, Yu Y, Li B, Li Z, Qin Z (2019) A new payload partition strategy in color image steganography. IEEE Trans Circuits Syst Video Technol 30(3):685–696
Mielikainen J (2006) LSB matching revisited. IEEE Signal Process Lett 13(5):285–287. [Accessed: 1st Dec 2020]
Muraya M. Effects of Cybercrime Management on Information Security of selected Hotels in Nairobi Kenya (Doctoral dissertation, Moi University). [Accessed: 1st Dec 2020]
Papanikolaou A, Vlachos V, Papathanasiou A, Chaikalis K, Dimou M, Karadimou M (2014) A survey of cyber crime in Greece. Telfor J 6(2):86–91. [Accessed: 1st Dec 2020]
Pevny T, Bas P, Fridrich J (2010) Steganalysis by subtractive pixel adjacency matrix. IEEE Trans Inf Forensics Secur 5(2):215–224. [Accessed: 1st Dec 2020]
Samkari H, Gutub A (2019) Protecting medical records against cybercrimes within hajj period by 3-layer security. Recent Trends Inf Technol Appl 2(3):1–21. [Accessed: 1st Dec 2020] https://doi.org/10.5281/zenodo.3543455
Shabani N (2017) A study of cyber security in hospitality industry-threats and countermeasures: case study in Reno, Nevada. arXiv preprint arXiv:1705.02749
Shambour MK, Gutub A (2021) Personal privacy evaluation of smart devices applications serving Hajj and Umrah Rituals. J Eng Res. https://doi.org/10.36909/jer.13199
Shambour MK, Gutub A (2022) Progress of IoT research technologies and applications serving hajj and Umrah. Arab J Sci Eng (AJSE) 47:1253–1273. https://doi.org/10.1007/s13369-021-05838-7
Shambour MK, Gutub A (2022) The impact of corona disease on the feelings of Twitter users in the two Holy Citiesd during the Hajj season of 1442 AH. Hajj Forum 2022 - the 21st scientific Hajj research Forum, Madinah, Saudi Arabia, pp 254–265. https://drive.uqu.edu.sa/up/profile/Books/4310001/book_path_FeMAOaNgOR.pdf
Sahu AK, Swain G (2019) A novel n-rightmost bit replacement image steganography technique. 3D. Research 10(1):1–8
Sahu AK, Swain G, Sahu M, Hemalatha J (2021) Multi-directional block based PVD and modulus function image steganography to avoid FOBP and IEP. Journal of Information Security and Applications 58:102808
Seamans E (2018) The unique challenges of data security in the hospitality industry. Insurance & Loss Prevention, Lodging, Risk Management, Technology. https://hospitalitylawyer.com/the-unique-challenges-of-data-security-in-the-hospitality-industry/
Singh A, Satapathy SC, Roy A, Gutub A (2022) AI-based mobile edge computing for IoT: applications challenges and future scope. Arab J Sci Eng. https://doi.org/10.1007/s13369-021-06348-2
Swain G (2016) Digital image steganography using variable length group of bits substitution. Procedia Computer Science 85:31–38
The Network Support Company. (2017). Cybercrime and the hospitality industry
Trust Wave (2016) Hospitality in the Crosshairs of Cybercrime. https://www.infinigate.co.uk/fileadmin/user_upload/Vendors/Trustwave/hospitality-in-the-crosshairs-of-cybercrime.pdf
Wu DC, Tsai WH (2003) A steganographic method for images by pixel-value differencing. Pattern Recogn Lett 24(9–10):1613–1626
Wu NI, Hwang MS (2017) A novel LSB data hiding scheme with the lowest distortion. The Imaging Science Journal 65(6):371–378
Yallop A, Seraphin H (2020) Big data and analytics in tourism and hospitality: opportunities and risks. Journal of Tourism Futures 6(3):257–262. https://doi.org/10.1108/JTF-10-2019-0108
Ye J, Ni J, Yi Y (2017) Deep learning hierarchical representations for image steganalysis. IEEE Transactions on Information Forensics and Security 12(11):2545–2557
Zakaria AA, Hussain M, Wahab AW, Idris MY, Abdullah NA, Jung KH (2018) High-capacity image steganography with minimum modified bits based on data mapping and LSB substitution. Appl Sci 8(11):2199
Acknowledgments
Thanks for the international collaboration of institutions, Vignan’s Foundation for Science, Technology and Research, India, and Umm Al-Qura University, Saudi Arabia, for motivating this scientific research.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Informed consent
Informed consent was obtained from all individual participants included in the study.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sahu, A.K., Gutub, A. Improving grayscale steganography to protect personal information disclosure within hotel services. Multimed Tools Appl 81, 30663–30683 (2022). https://doi.org/10.1007/s11042-022-13015-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13015-7