Abstract
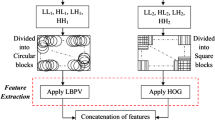
The fast growth of using digital images in the virtual world and, The advance of image processing tools makes an image under the effect of attackers or intruders. Attackers tamper digital images and divert the content of the image from its true meaning. The manipulation in digital images makes tampering hard to detect with the naked eye. Therefore, image forensic analysis is developed to keep up and protect the authenticity and rights of the owner of digital images. The Copy-move forgery detection (CMFD) scheme is the popular type in image forensic analysis. This paper presents a merged CMFD scheme. This scheme contains a preparing process and three layers of processing. In the preparing process, Haar Discrete Wavelet Transform(HDWT) automates the number of segments before applying the segmentation process. The first layer, Simple Linear Iterative Clustering(SLIC)segmentation method is proposed to split images into irregular labels. Then, classification these segments into two main types called texture or smooth regions based on the Entropy metric. In the second layer, the keypoint-based technique is adopted. Speed Up Robust Feature(SURF) as detector and Histogram Of Oriented Gradient (HOG) as a descriptor is applied on each region. SURF-HOG to extract key points from regions with different Threshold values. In the third layer, an efficient probabilistic false positive removal filter(M-SAC) is employed. It aims to include the correct results and exclude false results from the output detected image. Subsequently, increase TPR and decrease FPR. The proposed scheme is evaluated by using(IMD and MICC-F220)data sets. The photometric attacks(brightness, blurring, JPEG compression) and geometric transformation attacks(scaling, rotation) are applied in these datasets. The experimental results indicate that the proposed scheme is fast, efficient, and high performance under simple and compound attacks. It has high TPR, Low FPR and, makes the scheme more dynamic and suitable in image forensic analysis.










Similar content being viewed by others
References
A. Mathematics (2014) “ijpam.eu,” vol. 91, no. 3, pp. 349–360
Amerini I, Ballan L, Member S, Caldelli R, Del Bimbo A, Serra G (2011) A SIFT-based forensic method for copy-move attack detection and transformation recovery. 6(1):1–12
Amerini I, Ballan L, Caldelli R, Del A, Del L, Serra G (2013) Signal processing : image communication copy-move forgery detection and localization by means of robust clustering with J-linkage. Signal Process Image Commun 28:1–11
K. Asghar, Z. Habib, and M. Hussain (2016) “Copy-move and splicing image forgery detection and localization techniques : a review,” vol. 0618, no. May, pp. 2–4, .
Bay H, Tuytelaars T, Van Gool L (2006) SURF : speeded up robust features:404–417
Bhavya Bhanu MP, Arun Kumar MN (2017) Copy-move forgery detection using segmentation. Proc. 2017 11th Int. Conf. Intell. Syst. Control. ISCO 2017:224–228
Christlein V, Riess C, Jordan J, Riess C, Angelopoulou E (2012) An evaluation of popular copy-move forgery detection approaches. IEEE Trans Inf Forensics Secur 7(6):1841–1854
“Download _ CVIP Group”.
Emam M, Han Q, Zhang H (2018) Two-stage Keypoint detection scheme for region duplication forgery detection in digital images. J Forensic Sci 63(1):102–111
Escolano F. (2009) “Contour and Region-Based Image”. Image (Rochester, N.Y.)
Fadl SM and Semary NA (2017) “Robust copy-move forgery revealing in digital images using polar coordinate system,” Neurocomputing, .
Fridrich J, Soukal D, Lukáš J Detection of copy-move forgery in digital images.
Gonzalez RC“Digital Image Processing Third Edition.”
Guohui L, Qiong W, Dan T, Shaojie S (2007, 2007) A sorted neighborhood approach for detecting duplicated regions in image forgeries based on DWT and SVD. Proc 2007 IEEE Int Conf Multimed Expo, ICME 2007:1750–1753
Hassaballah M, Abdelmgeid AA, Alshazly HA Image features detection. Description and Matching
He Z, Lu W, Sun W, Huang J (2012) Digital image splicing detection based on Markov features in DCT and DWT domain. Pattern Recogn 45(12):4292–4299
Kaspi O, Yosipof A, Senderowitz H (2017) RANdom SAmple consensus ( RANSAC ) algorithm for material - informatics : application to photovoltaic solar cells. J. Cheminform
Khan S, Kulkarni A Robust method for detection of copy-move forgery in digital images:69–73
Lee JC, Chang CP, Chen WK (2015) Detection of copy-move image forgery using histogram of orientated gradients. Inf. Sci. (Ny). 321:250–262
Li J, Li X, Yang B, Sun X, Member S (2014) Segmentation-based Image Copy-move Forgery Detection Scheme. 6013(c):1–12
Lin C, … Tan Z (2019) Copy-move forgery detection using combined features and transitive matching. Multimed Tools Appl 78(21):30081–30096
Liu Y, Wang H, Chen Y, Wu H, Wang H (2020) A passive forensic scheme for copy-move forgery based on superpixel segmentation and K-means clustering. Multimed Tools Appl 79(1–2):477–500
Macdermott Á, Baker T, and Shi Q(2018) “IoT Forensics : Challenges For The IoA Era”.
Mahmood T, Irtaza A, Mehmood Z, Tariq Mahmood M (2017) Copy–move forgery detection through stationary wavelets and local binary pattern variance for forensic analysis in digital images. Forensic Sci Int 279:8–21
Meena KB, Tyagi V (2019) A copy-move image forgery detection technique based on Gaussian-Hermite moments. Multimed Tools Appl 78(23):33505–33526
Nirmal Jothi J, Letitia S (2020) Tampering detection using hybrid local and global features in wavelet-transformed space with digital images. Soft Comput 24(7):5427–5443
Pun C, Member S, Yuan X, Bi X (2015) Over - Segmentation and Feature Point Matching. 6013(c):1–12
Ryu S, Lee M, Lee H (2010) Detection of copy-rotate-move forgery using Zernike moments. 1:51–65
Sadeghi S, Dadkhah S, Jalab HA, Mazzola G, Uliyan D (2017) State of the art in passive digital image forgery detection : copy - move image forgery. Pattern Anal Appl (0123456789)
Silva E, Carvalho T, Ferreira A, Rocha A (2015) Going deeper into copy-move forgery detection : Exploring image telltales via multi-scale analysis and voting processes q. J. Vis. Commun. Image Represent. 29:16–32
Sridevi M, Aishwarya S, Nidheesha A, Bokadia D FREAK descriptor. Springer Singapore
Torr PHS, Murray DW (1997) The development and comparison of robust methods for estimating the fundamental matrix. Int J Comput Vis 24(3):271–300
Uliyan DM, Jalab HA, Wahab AWA, Shivakumara P (2016) A novel forged blurred region detection system for image forensic applications. Expert Syst Appl 64:1–10
Warif NBA, … Choo KKR (2016) Copy-move forgery detection: survey, challenges and future directions. J Netw Comput Appl 75:259–278
Warif NBA, Wahab AWA, Idris MYI, Salleh R, Othman F (2017) SIFT-symmetry: a robust detection method for copy-move forgery with reflection attack. J Vis Commun Image Represent 46:219–232
Yang F, Li J, Lu W, Weng J (2017) Copy-move forgery detection based on hybrid features. Eng. Appl. Artif. Intell. 59(May 2016):73–83
Zandi M, Mahmoudi-Aznaveh A, Talebpour A (2016) Iterative copy-move forgery detection based on a new interest point detector. IEEE Trans Inf Forensics Secur 11(11):2499–2512
Zhang Q, Lu W, Weng J (2016) Joint image splicing detection in DCT and Contourlet transform domain. J Vis Commun Image Represent 40(Part B):449–458
Zhang W, Yang Z, and Niu S (2017) “Detection of Copy-Move Forgery in Flat Region Based on Feature Enhancement,” vol. 2, pp. 159–171, .
Zhang Z, Wang C, Zhou X (2018) A survey on passive image copy-move forgery detection. 14(1):6–31
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Alhaidery, M.M.A., Taherinia, A.H. A passive image forensic scheme based on an adaptive and hybrid techniques. Multimed Tools Appl 81, 12681–12699 (2022). https://doi.org/10.1007/s11042-022-12374-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-12374-5