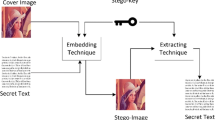
Abstract
Hiding sensitive information in a host image (or 2D signal) is a challenging task. Several image steganography techniques have been proposed in recent years, which either have low embedding capacity, or the embedded images are vulnerable. The proposed technique, which is based on Golden Ratio and Non-Subsampled Contourlet Transform (GRNSCT) model provides both high embedding capacity as well as the confidentiality of the embedded images. The high embedding capacity is achieved via a combination of mosaic process and two level NSCT (Non-Subsampled Contourlet Transform), while confidentiality is attained via double layer encryption based on shuffling method of a deck of cards. Several types of security evaluation metrics, such as, key sensitivity, histogram, and information entropy, are utilized to assess the robustness of the embedded images. The experimental results demonstrate that the proposed multi-image steganography technique achieves 24 bpp (bits per pixel) embedding capacity, or 300% payload with PSNR up to 42.38 dB (decibels), which is better than the existing techniques.



















Similar content being viewed by others
Notes
USC–SIPI image database is available at http://sipi.usc.edu/database/. Accessed 18 May 2021
References
Abdulla AA (2015) Exploiting similarities between secret and cover images for improved embedding efficiency and security in digital steganography. Doctoral thesis, University of Buckingham
Ahmed N (1991) How I came up with the discrete cosine transform. Digit Signal Process 1(1):4–5. https://doi.org/10.1016/1051-2004(91)90086-z
Akansu AN, Haddad RA (1992) Multiresolution signal decomposition: Transforms, sub-bands and wavelets. Academic Press, Boston
Atta R, Ghanbari M (2018) A high payload steganography mechanism based on wavelet packet transformation and neutrosophic set. J Vis Commun Image Represent 53:42–54. https://doi.org/10.1016/j.jvcir.2018.03.009
Atta R, Ghanbari M (2020) A high payload data hiding scheme based ondual tree complex wavelet transform. Optik. https://doi.org/10.1016/j.ijleo.2020.165786
Available from: https://www.merriam-webster.com/dictionary/steganography. Accessed 6 May, 2021
Available from: http://www.numberworld.org/digits/GoldenRatio. Accessed 14 Jan 2021
Available from: https://oeis.org/A001622. Accessed 14 Jan 2021
Baptiste J, Lemaréchal C (1993) Convex analysis and minimization algorithms
Biham E, Shamir A (1993) Differential cryptanalysis of the Data Encryption Standard (DES). Springer, Berlin
Brown M (2004) Advanced digital photography. Media Publishing
Candès EJ, Donoho DL (1999) Curvelets - a surprisingly effective nonadaptive representation for objects with edges. In: Cohen A, Rabut C, Schumaker LL (eds) Proceedings of the Curve and Surface Fitting. http://www.curvelet.org/papers/Curve99.pdf. Accessed 14 Jan 2021. Saint-Malo, France
Chan CS (2009) On using LSB matching function for data hiding in pixels. Fundamenta Informaticae. IOS Press 96:49–59
Cox IJ, Miler ML (1997) A review of watermarking and the the importance of perceptual modeling. In: Electronic Imaging
Cunha AL, Zhou J, Do MN (2005) Nonsubsampled contourlet transform: construction and application in enhancement. In: Proceedings of the IEEE international conference on image processing, Genova, vol 1, pp 1–469
Cunha AL, Zhou J, Do MN (2006) The nonsubsampled contourlet transform: theory, design, and applications. IEEE Trans Image Process 15 (10):3089–3101
Debnath D, Ghosh E, Banik BG (2020) Multi-image hiding blind robust RGB steganography in transform domain. International Journal of Web-Based Learning and Teaching Technologies
Do MN, Vetterli M (2005) The contourlet transform: an efficient directional multiresolution image representation. IEEE Trans Image Process 14 (12):2091–2106
Dunlap RA (1997) The golden ratio and the Fibonacci numbers. World Scientific Publishing
Fisher RA, Yates F (1938) Statistical tables, example 12. London
Fridrich J, Lisonek P, Soukal D (2007) On steganographic embedding efficiency. Information Hiding. Springer, Berlin, pp 282–296
Gallier J (2001) Geometric methods and applications. Springer, Berlin
Ghosal SK, Mandal JK, Sarkar R (2018) High payload image steganography based on Laplacian of Gaussian (LoG) edge detector. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-018-6126-y
Gong LH, Tian C, Zou WP, Zhou NR (2021) Robust and imperceptible watermarking scheme based on Canny edge detection and SVD in the contourlet domain. Multimed Tools Appl 80(1):439–461
Gutub A, Al-Shaarani F (2020) Efficient implementation of multi-image secret hiding based on LSB and DWT steganography comparisons. Arabian Journal for Science and Engineering
Jeevitha S, Prabha NA (2019) Effective payload and improved security using HMT Contourlet transform in medical image steganography. Health and Technology. https://doi.org/10.1007/s12553-018-00285-1
Kadhim IJ, Premaratne P, Vial PJ (2019) High capacity adaptive image steganography with cover region selection using dual-tree complex wavelet transform. Cognitive Systems Research. https://doi.org/10.1016/j.cogsys.2019.11.002
Ker AD (2013) Moving steganography and steganalysis from the laboratory into the real world. In: ACM workshop on Information hiding and Multimedia Security, pp 45–58
Kingsbury NG (1998) The dual-tree complex wavelet transform: a new technique for shift invariance and directional filters. In: Proceedings of the IEEE Digital Signal Processing Workshop, Citeseer, Bryce Canyon, vol 86, pp 120–131
Knuth DE (1981) The art of computer programming, vol 2. Addison-Wesley Publishing Company, Boston
Kumar V, Kumar D (2017) A modified DWT-based image steganography technique. Multimed Tools Appl 77(11):13279–13308. https://doi.org/10.1007/s11042-017-4947-8
Lang S (1986) Introduction to linear algebra, 2nd edn. Springer, Berlin
Lawton W (1993) Applications of complex valued wavelet transforms to sub-band decomposition. IEEE Trans Signal Process 41:3566–3568
Mangayarkarasi S, Abinesh G, Kala TS (2018) A secure image steganography method using contourlet transform domain. Int J Pure Appl Math 119 (15):3643–3651
Maschke T (2004) Digital camera technology: Technology of digital cameras in theory and practice. Springer, Berlin
Mielikainen J (2006) LSB Matching revisited. IEEE Signal Process Lett 13:285–287
Muhuri PK, Ashraf Z, Goel S (2020) A novel image steganographic method based on integer wavelet transformation and particle swarm optimization. Appl Soft Comput J 92:106–257. https://doi.org/10.1016/j.asoc.2020.106257
Reshma VK, Kumar RSV, Shahi D, Shyjith MB (2020) Optimized support vector neural network and contourlet transform for image steganography. Evolutionary Intelligence. https://doi.org/10.1007/s12065-020-00387-8
Rivest RL (1990) Cryptography. In: Rivest RL (ed) Leeuwen JV. Elsevier, p 1
Rockafellar TR (1970) Convex analysis. Princeton Mathematical Series, 28. Princeton University Press, Princeton
Schneier B (1996) Applied cryptography: Protocols algorithms and source code in C, 2nd edn. Wiley, New York
Selesnick IW, Baraniuk RG, Kingsbury NC (2005) The dual-tree complex wavelet transform
Shannon CE (1949) Communication theory of secrecy systems. Bell System Technical J 28:656–715
Subhedar MS, Mankar VH (2019) Image steganography using contourlet transform and matrix decomposition techniques. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-019-7512-9
Sun S, Guo Y (2015) A novel image steganography based on contourlet transform and Hill cipher. Journal of Information Hiding and Multimedia Signal Processing
Westfeld A (2001) F5 - a steganographic algorithm. Information Hiding. Springer, Berlin, pp 289–302
Acknowledgements
The authors would like thank everyone, who has contributed anyhow in the preparation of this manuscript.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
The authors declare that they have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This work was supported by UGC (University Grants Commission), India under grant No. [415024]
Rights and permissions
About this article
Cite this article
Gaffar, A., Joshi, A.B., Singh, S. et al. A high capacity multi-image steganography technique based on golden ratio and non-subsampled contourlet transform. Multimed Tools Appl 81, 24449–24476 (2022). https://doi.org/10.1007/s11042-022-12246-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-12246-y