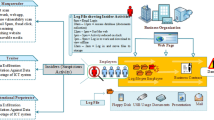
Abstract
Insider threats are a significant source of security breaches in organizations. They are often identified using machine and deep learning methods. These methods rely on predefined rules, require explicit feature engineering, and also give rise to more false positives. To overcome these limitations, the proposed work focus on introducing an enhanced insider threat detection method based on user behavior analysis. It leads to fewer false positives, faster threat detection, and significantly higher classifier accuracy. This enhancement is achieved due to: use of data pre-processing steps for removal of noise; use of isometric feature mapping to minimize information loss while extracting the features from a high dimensional space; use of content based features to enhance the feature set for final classification; use of emperor penguin algorithm due to its effective exploitation and exploration for optimum feature selection; and, use of multi fuzzy classifier to parallelly handle variety of features for fast processing. The proposed method is tested on CMU-CERT v4.2 dataset using eight different performance evaluation metrics. Our test results show that the proposed method outperforms the existing methods.











Similar content being viewed by others
References
Almehmadi A (2018) Micromovement behavior as an intention detection measurement for preventing insider threats. IEEE Access 6:40626–40637
Bin Ahmad M, Akram A, Asif M, Ur-Rehman S (2014) Using genetic algorithm to minimize false alarms in insider threats detection of information misuse in windows environment. Math Probl Eng 2014:12
Böse B., Avasarala B, Tirthapura S, Chung Y-Y, Steiner D (2017) Detecting insider threats using radish: a system for real-time anomaly detection in heterogeneous data streams. IEEE Syst J 11(2):471–482
Cao N, Shi C, Lin S, Lu J, Lin Y-R, Lin CY (2015) Targetvue: Visual analysis of anomalous user behaviors in online communication systems. IEEE Trans Vis Comput Graph 22(1):280–289
Chapman P, Clinton J, Kerber R, Khabaza T, Reinartz T, Shearer C, Wirth R, et al. (2000) Crisp-dm 1.0: Step-by-step data mining guide. SPSS inc 9:13
Chattopadhyay P, Wang L, Tan Y. -P. (2018) Scenario-based insider threat detection from cyber activities. IEEE Trans Comput Soc Syst 5(3):660–675
Cmu-cert insider threat test dataset. ftp://ftp.sei.cmu.edu/pub/cert-data/
Dhiman G, Kumar V (2018) Emperor penguin optimizer: a bio-inspired algorithm for engineering problems. Knowl-Based Syst 159:20–50
Gurucul - insider threat survey report. https://gurucul.com/2020-insider-threat-survey-report/
Iranmanesh SM, Mohammadi M, Akbari A, Nassersharif B (2011) Improving detection rate in intrusion detection systems using fcm clustering to select meaningful landmarks in incremental landmark isomap algorithm. In: International Conference on Theoretical and Mathematical Foundations of Computer Science, pp. 46–53 Springer
Izquierdo S, Izquierdo LR (2017) Mamdani fuzzy systems for modelling and simulation: A critical assessment, Available at SSRN 2900827
Kott A, Wang C, Erbacher RF (2015) Cyber defense and situational awareness, vol 62. Springer, New York
Law MH, Jain AK (2006) Incremental nonlinear dimensionality reduction by manifold learning. IEEE transactions on pattern analysis and machine intelligence 28(3):377–391
Le DC, Khanchi S, Zincir-Heywood AN, Heywood MI (2018) Benchmarking evolutionary computation approaches to insider threat detection. In: Proceedings of the Genetic and Evolutionary Computation Conference. pp 1286–1293
Leslie NO, Harang RE, Knachel LP, Kott A (2018) Statistical models for the number of successful cyber intrusions. The Journal of Defense Modeling and Simulation 15(1):49–63
Liu L, De Vel O, Chen C, Zhang J, Xiang Y (2018) Anomaly-based insider threat detection using deep autoencoders. In: 2018 IEEE International Conference on Data Mining Workshops (ICDMW), pp. 39–48, IEEE
Lo O, Buchanan WJ, Griffiths P, Macfarlane R (2018) Distance measurement methods for improved insider threat detection. Secur Commun Netw 2018
Lu J, Wong RK (2019) Insider threat detection with long short-term memory. In: proceedings of the Australasian Computer Science Week Multiconference, pp. 1–10
May C, et al. (2017) Insight into insiders: a survey of insider threat taxonomies, analysis, modeling and countermeasures
Meng F, Lou F, Fu Y, Tian Z (2018) Deep learning based attribute classification insider threat detection for data security. In: 2018 IEEE Third International Conference on Data Science in Cyberspace (DSC), pp. 576–581 IEEE
Ramos J, et al. (2003) Using tf-idf to determine word relevance in document queries. In: proceedings of the first instructional conference on machine learning, 242, pp. 133–142, Piscataway, NJ
Sen S (2015) A survey of intrusion detection systems using evolutionary computation. In: Bio-inspired computation in telecommunications, pp. 73–94, Elsevier
Shearer C (2000) The crisp-dm model: the new blueprint for data mining. J data warehous 5(4):13–22
Singh M, Mehtre B, Sangeetha S (2019) User behavior profiling using ensemble approach for insider threat detection. In: 2019 IEEE 5th International Conference on Identity, Security, and Behavior Analysis (ISBA), pp. 1–8, IEEE
Singh M, Mehtre B, Sangeetha S (2020) Insider threat detection based on user behaviour analysis. In: International Conference on Machine Learning, Image Processing, Network Security and Data Sciences, pp. 559–574, Springer
Willett P (2006) The porter stemming algorithm: then and now, Program
Xin Y, Kong L, Liu Z, Chen Y, Li Y, Zhu H, Gao M, Hou H, Wang C (2018) Machine learning and deep learning methods for cybersecurity. IEEE Access 6:35365–35381
Yamin MM, Katt B, Sattar K, Ahmad MB (2019) Implementation of insider threat detection system using honeypot based sensors and threat analytics. In: Future of Information and Communication Conference, pp. 801–829, Springer Insiderthreatdetectionwithdeepneuralnetwork(2018)
ZaytsevA,MalyukA(2017)Identifyingapotentialinsiderusingclassification models.AutomControlComputSci 51(8):860–866
ZhanZ,XuM,XuS(2015)Predictingcyberattackrateswithextremevalues. IEEETransactionsonInformationForensicsandSecurity 10(8):1666–1677
ZhengK-m,QianX,ZhouY,JiaL-j(2009)Intrusiondetectionusingisomap andsupportvectormachine.In: 2009InternationalConferenceonArtificialIntelligence andComputationalIntelligence,3,pp.235–239IEEE
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’snote
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Singh, M., Mehtre, B. & Sangeetha, S. User behavior based Insider Threat Detection using a Multi Fuzzy Classifier. Multimed Tools Appl 81, 22953–22983 (2022). https://doi.org/10.1007/s11042-022-12173-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-12173-y