Abstract
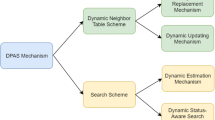
The inherent scalability and flexibility of structured overlay networks makes them an excellent choice to support modern day applications with complex, volatile, mobile, and heterogeneous infrastructure. However, this heterogeneity and volatility of the infrastructure increase the need for more reliable maintenance mechanisms to guarantee the availability and performance of structured overlay networks in the presence of autonomous participants. This paper focus on the implementation of the state-based predictive maintenance mechanism that is based on the intelligent prediction of the dynamics of the neighbouring node (k closest successors as defined in a DHT finger table) to schedule proactive maintenance of the nodes having periodic availabilities. The paper provides the predictive analysis of the uptime patterns of the machines specified in the Microsoft trace file using rapid miner and yielded 95% prediction accuracy. The proposed predictive framework is also tested in the simulation environments and the results show significant performance improvements by implementing the predictive maintenance approach as compared to the state-of-the-art statically scheduled maintenance actions. The simulation results report 54.23% increase in the average lookup success ratio and 59% reduction in the maintenance overhead of chord-based overlay network by the implementation of the proposed technique.












Similar content being viewed by others
References
Alima LO, El-Ansary S, Brand P, Haridi S (2003) DKS (N, k, f): a family of low communication, scalable and fault-tolerant infrastructures for P2P applications. In: 3rd IEEE/ACM International Symposium on Cluster Computing and the Grid, pp 344-350
Baumgart I, Heep B, Kraue S (2007) OverSim: A flexible overlay network simulation framework. In: IEEE Global Internet Symposium, pp 79-84
Bhagwan R, Savage S, Voelker G (2003) Understanding availability. Peer Peer Syst II:256-267
Bolosky WJ, Douceur JR, Ely D, Theimer M (2000) Feasibility of a serverless distributed file system deployed on an existing set of desktop PCs. In: ACM SIGMETRICS Performance Evaluation Review, vol 28, no 1, pp 34-43
Chu JC, Labonte KS, Levine BN (2002) Availability and locality measurements of peer-to-peer file systems. In: ITCom: The Convergence of Information Technologies and Communications, pp 310-321
Dotan M, Pignolet YA, Schmid S, Tochner S, Zohar A (2021) Survey on blockchain networking: Context, state-of-the-art, challenges. ACM Comput Surv (CSUR) 54(5):1–34
Douceur JR (2003) Is remote host availability governed by a universal law? ACM SIGMETRICS Perform Eval Rev 31(3):25–29
Feldmann M, Scheideler C, Schmid S (2020) Survey on algorithms for self-stabilizing overlay networks. ACM Comput Surv (CSUR) 53(4):1–24
Foreback D, Nesterenko M, Tixeuil S (2018) Churn possibilities and impossibilities. In: International Conference on Networked Systems. Springer, Berlin, pp 303-317
Ghinita G, Teo YM (2006) An adaptive stabilization framework for distributed hash tables. In: IEEE 20th International Parallel and Distributed Processing Symposium, pp 10-20
Ghodsi A, Alima LO, Haridi S (2005) Low-bandwidth topology maintenance for robustness in structured overlay networks. In: Proceedings of the IEEE 38th Annual Hawaii International Conference on System Sciences, pp 302a-312a
Guha S, Daswani N (2006) An experimental study of the Skype peer-to-peer voip system. International Workshop on Peer-to-Peer Systems, pp 1-6
Guidi B, Conti M, Passarella A, Ricci L (2018) Managing social contents in decentralized online social networks: a survey. Online Soc Netw Media 7:12–29
Hassanzadeh-Nazarabadi Y, Küpçü A, Ozkasap O (2019) Decentralized utility-and locality-aware replication for heterogeneous dht-based p2p cloud storage systems. IEEE Trans Parallel Distrib Syst 31(5):1183–1193
Hassanzadeh-Nazarabadi Y, Küpçü A, Özkasap Ö (2021) Interlaced: Fully decentralized churn stabilization for skip graph-based dhts. J Parallel Distrib Comput 149:13–28
Javadi B, Kondo D, Vincent JM, Anderson DP (2009) Mining for availability models in large-scale distributed systems: A case study of seti@ home. In: Proceedings of MASCOTS, pp 276-283
Javadi B, Kondo D, Iosup A, Epema D (2013) The Failure Trace Archive: Enabling the comparison of failure measurements and models of distributed systems. J Parallel Distrib Comput 73(8):1208–1223
Kaur R, Sangal AL, Kumar K (2016) Performance analysis of predictive stabilization for churn handling in structured overlay networks. In: Proceedings of the International Conference on Big Data and Advanced Wireless Technologies, pp 1-7
Kaur R, Sangal AL, Kumar K (2017) Modeling and simulation of adaptive neuro-fuzzy based intelligent system for predictive stabilization in structured overlay networks. Eng Sci Technol 20(1):310-320
Kaur R, Gabrijelčič D, Klobučar T (2020) Churn handling strategies to support dependable and survivable structured overlay networks. IETE Technical Review, pp 1-17
Khan MA, Hamila R, Al-Emadi NA, Kiranyaz S, Gabbouj M (2020) Real-time throughput prediction for cognitive Wi-Fi networks. J Netw Comput Appl 150:102499
Klinkenberg R (ed) (2013) RapidMiner: Data mining use cases and business analytics applications. Chapman and Hall/CRC, London
Koutsopoulos A, Scheideler C, Strothmann T (2017) Towards a universal approach for the finite departure problem in overlay networks. Inf Comput 255:408–424
Liu H, Azhandeh K, De Foy X, Gazda R (2019) A comparative study of name resolution and routing mechanisms in information-centric networks. Digit Commun Netw 5(2):69–75
Long D, Muir A, Golding R (1995) A longitudinal survey of internet host reliability. In: 14th Symposium on reliable distributed systems, pp 2-9
Luo L, Scheideler C, Strothmann T (2019) MULTISKIPGRAPH: A self-stabilizing overlay network that maintains monotonic searchability. In: 2019 IEEE International Parallel and Distributed Processing Symposium (IPDPS), pp 845-854
Mickens JW, Noble BD (2006) Exploiting availability prediction in distributed systems. In: Proceedings of the 3rd conference on Networked Systems Design & Implementation, vol 3, pp 6-6
Microsoft trace downloads. http://fta.scem.uws.edu.au/index.php?n=Main.Download. Accessed 5 Nov 2021
Miguel EC, Silva CM, Coelho FC, Cunha IF, Campos SV (2021) Construction and maintenance of P2P overlays for live streaming. Multimed Tools Appl 80(13):20255–20282
Pace A, Quema V, Schiavoni V (2011) Exploiting node connection regularity for DHT replication. In: IEEE Symposium on Reliable Distributed Systems, pp 111–20
Pirozmand P, Wu G, Jedari B, Xia F (2014) Human mobility in opportunistic networks: Characteristics, models and prediction methods. J Netw Comput Appl 42:45–58
Porter B, Taiani F, Coulson G (2006) Generalized repair for overlay networks. In: 25th IEEE Symposium on Reliable Distributed Systems, pp 132-142
Rongjun XIE, Khalil I, Badsha S, Atiquzzaman M (2019) Collaborative extreme learning machine with a confidence interval for P2P learning in healthcare. Comput Netw 149:127–143
Shukla N, Datta D, Pandey M, Srivastava S (2021) Towards software defined low maintenance structured peer-to-peer overlays. Peer Peer Netw Appl 14(3):1242-1260
Song G, Kim S (2013) Long-term behavior pattern prediction for peer-to-peer systems. In: IEEE P2P 2013 Proceedings, pp 1-2
Song G, Kim S, Seo D, Jang S (2010) Replica placement algorithm based on peer availability for p2p storage systems. Int J Adv Netw Serv 3(1):237–248
Steiner M, En-Najjary T, Biersack EW (2009) Long term study of peer behavior in the KAD DHT. IEEE/ACM Trans Netw (ToN) 17(5):1371–1384
Stoica I, Morris R, Liben-Nowell D, Karger DR, Kaashoek MF, Dabek F, Balakrishnan H (2003) Chord: a scalable peer-to-peer lookup protocol for internet applications. IEEE Trans Netw (TON) 11(1):17–32
Tang Y, Cheng N, Wu W, Wang M, Dai Y, Shen X (2019) Delay-minimization routing for heterogeneous VANETs with machine learning based mobility prediction. IEEE Trans Veh Technol 68(4):3967–3979
Ur RZ, Nadir S, Ur RH, Sehrish K (2018) Implementation of dht-based routing in smart grid. Int J Open Inf Technol 6(1):504–515
Vrignat P, Avila M, Duculty F, Kratz F (2015) Failure event prediction using hidden markov model approaches. IEEE Trans Reliab 64(3):1038–1048
Acknowledgements
The author would like to thank Dr. Tomaž Klobučar and Dr. Dušan Gabrijelčič for their work in proofreading and technical editing of the manuscript.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The author has no relevant financial or non-financial interests to disclose.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kaur, R. Hidden Markov Model for short term churn forecast in the structured overlay networks. Multimed Tools Appl 81, 34481–34499 (2022). https://doi.org/10.1007/s11042-021-11831-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-11831-x