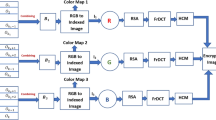
Abstract
For the asymmetric key, the Diffie Hellman Key (DHK) protocol is very efficient, but sometimes it is vulnerable against brute force attacks if the parameters are not chosen carefully. Our study aims to improve the asymmetric key scheme based on the elliptic curve cryptosystem (ECC). The sender and receiver agree on an elliptic curve based on the DHK sharing technique, but generator G is kept secret, and we generate its hash value, which is shared publicly. The authorized members can recover G using the hash value. By keeping G secret, the key protocol becomes much more robust than existing ones. Further, the proposed scheme will be applied to multiple RGB images. In this novel public key algorithm, 4D chaotic sequences are used for the diffusion of image pixels. The pixels’ values are used for permutations of images rather than the chaotic sequences, strengthening the scheme against chosen/known plain text attacks. The simulation and the security analysis of the proposed algorithm show efficiency, potential to endure the varied attacks, and prospects for real-world application.

















Similar content being viewed by others
References
Abd-El-Hafiz SK, Radwan AG, Haleem SHA, Barakat ML (2014) A fractal-based image encryption system. IET Image Process 8(12):742–752
Bashir Z, Watrobski J, Rashid T, Zafar S, Sałabun W (2017) Chaotic dynamical state variables selection procedure based image encryption scheme. Symmetry 9(12):312
Bashir Z, Iqbal N, Hanif M (2021) A novel grayscale image encryption scheme based on pixels’ swapping operations. Multimed Tools Applic 80(1):1029–1054
Belazi A, El-Latif AAA, Diaconu AV, Rhouma R, Belghith S (2017) Chaos-based partial image encryption scheme based on linear fractional and lifting wavelet transforms. Opt Lasers Eng 88:37–50
Bissell C (2009) Vladimir Aleksandrovich Kotelnikov: pioneer of the sampling theorem, cryptography, optimal detection, planetary mapping [History of Communications]. IEEE Commun Mag 47(10):24–32
Cassels JWS, Silverman JH (1987) The arithmetic of elliptic curves. Bulletin (New Series) of the American Mathematical Society 17(1):148–149
Cokal C, Solak E (2009) Cryptanalysis of a chaos-based image encryption algorithm. Phys Lett A 373(15):1357–1360
Das S, Mandal S, Ghoshal N (2015) Multiple-image encryption using genetic algorithm. In: Intelligent computing and applications. Springer, New Delhi, pp 145–153
Dey D, Giri D, Jana B, Maitra T, Mohapatra RN (2018) Linear-feedback shift register-based multi-ant cellular automation and chaotic map-based image encryption. Security and Privacy 1(6):e52
Di H, Kang Y, Liu Y, Zhang X (2016) Multiple image encryption by phase retrieval. Optical Engineering 55(7):073103
Di H, Kang Y, Liu Y, Zhang X (2016) Multiple image encryption by phase retrieval. Opt Eng 55(7):073103
Diffie W, Hellman M (1976) New directions in cryptography. IEEE Trans 22(6):644–654
Guesmi R, Farah MAB, Kachouri A, Samet M (2016) A novel chaos-based image encryption using DNA sequence operation and Secure Hash Algorithm SHA-2. Nonlinear Dyn 83(3):1123–1136
Hankerson D, Menezes AJ, Vanstone S (2006) Guide to elliptic curve cryptography. Springer Science & Business Media
Huang X, Ye G (2014) An efficient self-adaptive model for chaotic image encryption algorithm. Commun Nonlinear Sci 19(12):4094–4104
Iqbal N, Abbas S, Khan MA, Alyas T, Fatima A, Ahmad A (2019) An RGB image cipher using chaotic systems, 15-puzzle problem and DNA computing. IEEE Access 7:174051–174071
Karawia AA (2018) Encryption algorithm of multiple-image using mixed image elements and two dimensional chaotic economic map. Entropy 20(10):801
Kaushik A (2013) Extended Diffie-Hellman algorithm for key exchange and management. Int J Adv Eng Sci Appl Math 3(3)
Koblitz N (1987) Elliptic curve cryptosystems. Math Comput 48(177):203–209
Kumar M, Iqbal A, Kumar P (2016) A new RGB image encryption algorithm based on DNA encoding and elliptic curve Diffie-Hellman cryptography. Signal Process 125:187–202
Lai Q, Nestor T, Kengne J, Zhao XW (2018) Coexisting attractors and circuit implementation of a new 4D chaotic system with two equilibria. Chaos Solitons Fractals 107:92–102
Laiphrakpam DS, Khumanthem MS (2018) A robust image encryption scheme based on chaotic system and elliptic curve over finite field. Multimed Tools Appl 77(7):8629–8652
Li C, Li S, Lo KT (2011) Breaking a modified substitution–diffusion image cipher based on chaotic standard and logistic maps. Commun Nonlinear Sci 16(2):837–843
Li Y, Wang C, Chen H (2017) A hyper-chaos-based image encryption algorithm using pixel-level permutation and bit-level permutation. Opt Lasers Eng 90:238–246
Li CL, Li HM, Li FD, Wei DQ, Yang XB, Zhang J (2018) Multiple-image encryption by using robust chaotic map in wavelet transform domain. Optik 171:277–286
Liu H, Wang X (2012) Image encryption using DNA complementary rule and chaotic maps. Appl Soft Comput 12(5):1457–1466
Liu H, Wang X, Kadir A (2013) Color image encryption using Choquet fuzzy integral and hyperchaotic system. Optik-International Journal for Light and Electron Optics 124(18):3527–3533
Liu W, Xie Z, Liu Z, Zhang Y, Liu S (2015) Multiple-image encryption based on optical asymmetric key cryptosystem. Opt Commun 335:205–211
Luo Y, Ouyang X, Liu J, Cao L (2019) An image encryption method based on elliptic curve elgamal encryption and chaotic systems. IEEE Access 7:38507–38522
Malik MA, Bashir Z, Iqbal N, Imtiaz MA (2020) Color image encryption algorithm based on hyper-chaos and DNA computing. IEEE Access 8:88093–88107
Menzes AJ, Van OPC, Vanstone SA (2001) Handbook of Applied Cryptology [M]
Niyat AY, Moattar MH, Torshiz MN (2017) Color image encryption based on hybrid hyper-chaotic system and cellular automata. Opt Lasers Eng 90:225–237
Norouzi B, Mirzakuchaki S (2014) A fast color image encryption algorithm based on hyper-chaotic systems. Nonlinear Dyn 78(2):995–1015
Noura H, Chehab A, Noura M, Couturier R, Mansour MM (2019) Lightweight, dynamic and efficient image encryption scheme. Multimed Tools Appl 78(12):16527–16561
Paar C, Pelzl J (2009) Understanding cryptography: a textbook for students and practitioners. Springer Science & Business Media
Sampangi R, Sampalli S (2015) Butterfly encryption scheme for resource-constrained wireless networks. Sensors 15(9):23145–23167
Seyedzade SM, Mirzakuchaki S, Atani RE (2010) A novel image encryption algorithm based on hash function. In: 2010 6th Iranian conference on machine vision and image processing. IEEE, pp 1–6
Shannon CE (1949) Communication theory of secrecy systems. BSTJAN 28(4):656–715
Singh LD, Singh KM (2015) Image encryption using elliptic curve cryptography. Procedia Comput Sci 54:472–481
Singh LD, Singh KM (2018) Visually meaningful multi-image encryption scheme. Arab J Sci Eng 43(12):7397–7407
Stallings W (2021) Cryptography and network security: principles and practice 0133354695, 9780133354690
Su Y, Tang C, Gao G, Gu F, Lei Z, Tang S (2017) Optical encryption scheme for multiple color images using complete trinary tree structure. Opt Lasers Eng 98:46–55
Suri S, Vijay R (2017) An AES-CHAOS-Based Hybrid approach to encrypt multiple images. In: Recent developments in intelligent computing, communication and devices. Springer, Singapore, pp 37–43
Tang Z, Song J, Zhang X, Sun R (2016) Multiple-image encryption with bit-plane decomposition and chaotic maps. Opt Lasers Eng 80:1–11
Toughi S, Fathi MH, Sekhavat YA (2017) An image encryption scheme based on elliptic curve pseudo-random and advanced encryption system. Signal Process 141:217–227
Wei X, Guo L, Zhang Q, Zhang J, Lian S (2012) A novel color image encryption algorithm based on DNA sequence operation and hyper-chaotic system. J Syst Softw 85(2):290–299
Wu Y, Zhou Y, Noonan JP, Agaian S (2014) Design of image cipher using Latin squares. Inf Sci 264:317–339
Xiong Z, Wu Y, Ye C, Zhang X, Xu F (2019) Color image chaos encryption algorithm combining CRC and nine palace map. Multimed Tools Appl 78(22):31035–31055
Xu M, Tian Z (2019) A novel image cipher based on 3D bit matrix and Latin cubes. Inf Sci 478:1–14
Yuan S, Liu X, Zhou X, Li Z (2016) Multiple-image encryption scheme with a single-pixel detector. J Mod Opt 63(15):1457–1465
Zhang X, Wang X (2017) Multiple-image encryption algorithm based on mixed image element and chaos. Comput Electr Eng 62:401–413
Zhang X, Wang X (2017) Multiple-image encryption algorithm based on mixed image element and permutation. Opt Lasers Eng 92:6–16
Zhang X, Wang X (2018) Digital Image Encryption Algorithm Based on Elliptic Curve Public Cryptosystem. IEEE Access 6:70025–70034
Zhang X, Wang X (2018) Multiple-image encryption algorithm based on the 3D permutation model and chaotic system. Symmetry 10(11):660
Zhang X, Wang X (2019) Multiple-image encryption algorithm based on DNA encoding and chaotic system. Multimed Tools Appl 78(6):7841–7869
Zhang L, Zhou Y, Huo D, Li J, Zhou X (2018) Multiple-image encryption based on double random phase encoding and compressive sensing by using a measurement array preprocessed with orthogonal-basis matrices. Opt Laser Technol 105:162–170
Zhao Z, Zhang X (2013) ECC-based image encryption using code computing. In: Proceedings of the 2012 international conference on communication, electronics and automation engineering. Springer, Berlin, pp 859–865
Zhou Y, Panetta K, Agaian S, Chen CP (2012) Image encryption using P-Fibonacci transform and decomposition. Opt Commun 285(5):594–608
Zhou N, Zhang A, Wu J, Pei D, Yang Y (2014) Novel hybrid image compression-encryption algorithm based on compressive sensing. Optik-International Journal for Light and Electron Optics 125(18):5075–5080
Zhu C (2012) A novel image encryption scheme based on improved hyperchaotic sequences. Opt Commun 285(1):29–37
Author information
Authors and Affiliations
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Rights and permissions
About this article
Cite this article
Bashir, Z., Malik, M.G.A., Hussain, M. et al. Multiple RGB images encryption algorithm based on elliptic curve, improved Diffie Hellman protocol. Multimed Tools Appl 81, 3867–3897 (2022). https://doi.org/10.1007/s11042-021-11687-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-11687-1