Abstract
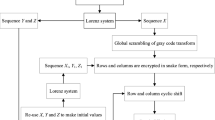
Swapping a row with a row, a column with a column or row with a column are usual operations carried out to scramble the given input plain image. To introduce more complications for the potential hackers, a novel grayscale image encryption scheme using the variable length row-column swapping based scrambling (VLRCSBS) has been proposed in this study. Security of the cipher would be improved in this way. Two chaotic maps, Henon map and piecewise linear chaotic map (PWLCM) have been used. These maps provide three streams of random numbers. Two more streams of random numbers have been created by manipulating the two streams of Henon map. After the grayscale image is input, arbitrary row and column are selected from this image to realize the scrambling effects. A randomly selected vector of pixels from these selected rows and columns is swapped with each other for a number of times. If selected vectors of pixels intersect each other, then to avoid the loss of pixels data, an intersection filter (IF) has been employed to forgo the intersecting vectors of selected pixels from the row and column for swapping. Resultantly, the given image is confused abundantly. An Exclusive-OR(XOR) operation is conducted between the scrambled image and the keystream given by PWLCM to get the final encrypted image. In the previous studies, whole rows and whole columns were swapped with each other. Our study swapped randomly selected portions of the rows and columns for scrambling, which spawned more security. In order to introduce the plaintext sensitivity in the proposed cipher, the hash codes given by the SHA-256 hash function for each input image have been used to update the system parameters and the initial values of the chaotic systems. The value of information entropy attained through the proposed algorithm is 7.9975 which is very competitive. Besides, the simulation and the performance analyses with varied validation metrics express the robustness, defiance to the multifarious threats and potential for some real world application of the cipher.













Similar content being viewed by others
References
Alghafis A, Firdousi F, Khan M, Batool SI, Amin M (2020) An efficient image encryption scheme based on chaotic and Deoxyribonucleic acid sequencing. Math Comput Simul 177:441–466
Ali TS, Ali R (2020) A new chaos based color image encryption algorithm using permutation substitution and Boolean operation. Multimed Tools Appl pp 1–21
Cao C, Sun K, Liu W (2018) A novel bit-level image encryption algorithm based on 2D-LICM hyperchaotic map. Signal Process 143:122–133
Chai X, Fu X, Gan Z, Lu Y, Chen Y (2019) A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process 155:44–62
Chai X, Bi J, Gan Z, Liu X, Zhang Y, Chen Y (2020) Color image compression and encryption scheme based on compressive sensing and double random encryption strategy. Signal Process p 107684
Chen L, Ma B, Zhao X, Wang S (2017) Differential cryptanalysis of a novel image encryption algorithm based on chaos and Line map. Nonlinear Dyn 87(3):1797–1807
Diaconu AV (2015) KenKen puzzle-based image encryption algorithm. In Proc Rom Acad Ser A 16:313-320
Dorgham O, Al-Rahamneh B, Almomani A, Khatatneh KF (2018) Enhancing the security of exchanging and storing DICOM medical images on the cloud. Int J Cloud Appl Comput 8(1):154–172
Floating-Point Working Group (1985) IEEE computer society: IEEE standard for binary floating-point arithmetic, Standard 754–1985
Guo H, Zhang X, Zhao X, Yu H, Zhang L (2020) Quadratic function chaotic system and its application on digital image encryption. IEEE Access 8:55540–55549
Hanif M, Naqvi RA, Abbas S, Khan MA, Iqbal N (2020) A novel and efficient 3D multiple images encryption scheme based on chaotic systems and swapping operations. IEEE Access 8:123536–123555
Hoang TM, Thanh HX (2018) Cryptanalysis and security improvement for a symmetric color image encryption algorithm. Optik 155:366–383
Iqbal N, Abbas S, Khan MA, Alyas T, Fatima A, Ahmad A (2019) An rgb image cipher using chaotic systems, 15-puzzle problem and dna computing. IEEE Access 7:174051–174071
Iqbal N, Hanif M, Abbas S, Khan MA, Rehman ZU (2021) Dynamic 3D scrambled image based RGB image encryption scheme using hyperchaotic system and DNA encoding. J Inf Secur Appl 58:102809
Jian ZH, Da HU (2018) Quantum image encryption algorithm based on chaotic system and DNA coding. Journal of Southwest Jiaotong University 53(6)
Jithin KC, Sankar S (2020) Colour image encryption algorithm combining Arnold map, DNA sequence operation, and a Mandelbrot set. J Inf Secur Appl 50:102428
Joe H (2005) Asymptotic efficiency of the two-stage estimation method for copula-based models. J Multivar Anal 94(2):401–419
Khan M, Masood F (2019) A novel chaotic image encryption technique based on multiple discrete dynamical maps. Multimed Tools Appl 78(18):26203–26222
Kulsoom A, Xiao D, Abbas SA (2016) An efficient and noise resistive selective image encryption scheme for gray images based on chaotic maps and DNA complementary rules. Multimed Tools Appl 75(1):1–23
Li S, Chen G, Mou X (2005) On the dynamical degradation of digital piecewise linear chaotic maps. Int J Bifurcation Chaos 15(10):3119–3151
Liao X, Kulsoom A, Ullah S (2016) A modified (Dual) fusion technique for image encryption using SHA-256 hash and multiple chaotic maps. Multimed Tools Appl 75(18):11241–11266
Liao X, Hahsmi MA, Haider R (2018) An efficient mixed inter-intra pixels substitution at 2bits-level for image encryption technique using DNA and chaos. Optik 153:117–134
Masood F, Ahmad J, Shah SA, Jamal SS, Hussain I (2020) A novel hybrid secure image encryption based on julia set of fractals and 3D Lorenz chaotic map. Entropy 22(3):274
Murillo-Escobar MA, Meranza-Castillón MO, López-Gutiérrez RM, Cruz-Hernández C (2019) Suggested integral analysis for chaos-based image cryptosystems. Entropy 21:815
Norouzi B, Mirzakuchaki S (2014) A fast color image encryption algorithm based on hyper-chaotic systems. Nonlinear Dyn 78(2):995–1015
Norouzi B, Seyedzadeh SM, Mirzakuchaki S, Mosavi MR (2015) A novel image encryption based on row-column, masking and main diffusion processes with hyper chaos. Multimed Tools Appl 74(3):781–811
Parvin Z, Seyedarabi H, Shamsi M (2016) A new secure and sensitive image encryption scheme based on new substitution with chaotic function. Multimed Tools Appl 75(17):10631–10648
Ping P, Xu F, Mao Y, Wang Z (2018) Designing permutation–substitution image encryption networks with Henon map. Neurocomputing 283:53–63
Qayyum A, Ahmad J, Boulila W, Rubaiee S, Masood F, Khan F, Buchanan WJ (2020) Chaos-based confusion and diffusion of image pixels using dynamic substitution. IEEE Access 8:140876–140895
Shannon CE (1949) Communication theory of secrecy systems. Bell Syst Tech J 28(4):656–715
Sivakumar T, Venkatesan R (2016) A New Image Encryption Method Based on Knight’s Travel Path and True Random Number. J Inf Sci Eng 32(1):133–152
Sun S, Guo Y, Wu R (2019) A novel image encryption scheme based on 7D hyperchaotic system and row-column simultaneous swapping. IEEE Access 7:28539–28547
Taneja N, Raman B, Gupta I (2012) Combinational domain encryption for still visual data. Multimed Tools Appl 59(3):775–793
Ur Rehman A, Liao X, Wang H (2021) An innovative technique for image encryption using tri-partite graph and chaotic maps. Multimed Tools Appl pp 1–27
Wang B, Zhang BF, Liu XW (2021) An image encryption approach on the basis of a time delay chaotic system. Optik 225:165737
Wang X, Wang Q, Zhang Y (2015) A fast image algorithm based on rows and columns switch. Nonlinear Dyn 79(2):1141–1149
Wang X, Liu C (2017) A novel and effective image encryption algorithm based on chaos and DNA encoding. Multimed Tools Appl 76(5):6229–6245
Wu J, Liao X, Yang B (2018) Cryptanalysis and enhancements of image encryption based on three-dimensional bit matrix permutation. Signal Process 142:292–300
Wu X, Wang K, Wang X, Kan H, Kurths J (2018) Color image DNA encryption using NCA map-based CML and one-time keys. Signal Process 148:272–287
Wu Y, Zhou Y, Noonan JP, Panetta K, Agaian S (2010) Image encryption using the sudoku matrix. In Mobile Multimedia/Image Processing, Security, and Applications. International Society for Optics and Photonics. 7708:77080P
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI randomness tests for image encryption. Cyber journals: multidisciplinary journals in science and technology. J Sel Areas Commun 1(2):31–38
Xian Y, Wang X (2021) Fractal sorting matrix and its application on chaotic image encryption. Inf Sci 547:1154–1169
Xu L, Li Z, Li J, Hua W (2016) A novel bit-level image encryption algorithm based on chaotic maps. Opt Lasers Eng 78:17–25
Yang Y-G et al (2019) Image compression-encryption scheme based on fractional order hyper-chaotic systems combined with 2D compressed sensing and DNA encoding. Opt Laser Technol 119:105661
Zhang W, Wong KW, Yu H, Zhu ZL (2013) A symmetric color image encryption algorithm using the intrinsic features of bit distributions. Commun Nonlinear Sci Numer Simul 18(3):584–600
Zhang W, Yu H, Zhao YL, Zhu ZL (2016) Image encryption based on three-dimensional bit matrix permutation. Signal Process 118:36–50
Zhang YQ, Wang XY (2014) A symmetric image encryption algorithm based on mixed linear-nonlinear coupled map lattice. Inf Sci 273:329–351
Zhou G, Zhang D, Liu Y, Yuan Y, Liu Q (2015) A novel image encryption algorithm based on chaos and Line map. Neurocomputing 169:150–157
Zhou Y, Li C, Li W, Li H, Feng W, Qian K (2021) Image encryption algorithm with circle index table scrambling and partition diffusion. Nonlinear Dyn 103(2):2043–2061
Zhu C (2012) A novel image encryption scheme based on improved hyperchaotic sequences. Opt Commun 285(1):29–37
Zhu ZL, Zhang W, Wong KW, Yu H (2011) A chaos-based symmetric image encryption scheme using a bit-level permutation. Inf Sci 181(6):1171–1186
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Iqbal, N., Hanif, M. An efficient grayscale image encryption scheme based on variable length row-column swapping operations. Multimed Tools Appl 80, 36305–36339 (2021). https://doi.org/10.1007/s11042-021-11386-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-11386-x