Abstract
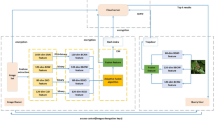
In recent years, secure image archival and retrieval model in cloud computing (CC) received significant attention to ensure data confidentiality and secured data transmission among cloud server and clients cloud storage and users. Traditional secure image retrieval (IR) techniques are not applicable to adapt with a large-scale IR in cloud environment. In order to overcome these issues, this article introduces an effective secure IR scheme using Inception with ResNet v2 (SIRS-IR) and Multiple Share Creation (MSC) scheme. The proposed method uses Inception with ResNet v2 model based feature extraction process. At the same time, the MSC process is utilized for multiple share generation and then encryption of shares takes place using double chaotic logistic map (DLCM) technique. Besides, the encrypted shares and the respective feature vectors are saved in the cloud server with the corresponding image identification number. During the IR process for the applied QI, the SIRS-IR model extracts the feature vectors and performs similarity measurement to retrieve the related images from the database interms of encrypted shares. Finally, the share decryption process is carried out for the reconstruction of original images with no loss of quality. Extensive experimentations were performed to verify the retrieval performance and image quality of the reconstructed images using Corel10K dataset. The obtained results stated that the presented SIRS-IR model is found to be superior to other methods in a considerable way.












Similar content being viewed by others
References
Abdulla AA, Sellahewa H, Jassim SA (2014) Stego quality enhancement by message size reduction and fibonacci bit-plane mapping. In: Chen L, Mitchell C (eds) Security standardisation research. SSR 2014. Lecture notes in computer science, vol 8893. Springer, Cham. https://doi.org/10.1007/978-3-319-14054-4_10
Alsmadi MK (2017) An efficient similarity measure for content based image retrieval using memetic algorithm. Egypt J Basic Appl Sci 4(2):112–122
Alsmadi MK (2018) Query-sensitive similarity measure for content-based image retrieval using meta-heuristic algorithm. J King Saud Univ Comput Inf Sci 30(3):373–381
Cheng SL, Wang LJ, Huang G, Du AY (2019) A privacy-preserving image retrieval scheme based secure kNN, DNA coding and deep hashing. Multimed Tools Appl 25:1–23
Du A, Wang L, Cheng S, Ao N (2020) A privacy-protected image retrieval scheme for fast and secure image search. Symmetry 12(2):282
ElAlami ME (2011) A novel image retrieval model based on the most relevant features. Knowl Based Syst 24(1):23–32
Elhoseny M, Shankar K, Lakshmanaprabu SK et al (2020) Hybrid optimization with cryptography encryption for medical image security in Internet of Things. Neural Comput Appl 32:10979–10993. https://doi.org/10.1007/s00521-018-3801-x
Ferreira B, Rodrigues J, Leitao J, Domingos H (2017) Practical privacy-preserving content-based retrieval in cloud image repositories. IEEE Trans Cloud Comput 7(3):784–798
Geetha P, Jayanthi VS, Jayanthi AN (2019) Multiple share creation based visual cryptographic scheme using diffusion method with a combination of chaotic maps for multimedia applications. Multimed Tools Appl 78(13):18503–18530
Gu Q, Xia Z, Sun X, Weng J (2020) MSPPIR: Multi-source privacy-preserving image retrieval in cloud computing. arXiv preprint arXiv:2007.12416
He K, Zhang X, Ren S, Sun J (2016) Deep residual learning for image recognition. IEEE Comput Soc Conf Comput Vis Pattern Recogn :770–778
Jhanwar N, Chaudhuri S, Seetharaman G, Zavidovique B (2004) Content based image retrieval using motif cooccurrence matrix. Image Vis Comput 22(14):1211–1220
Kouzehgar M, Tamilselvam YK, Heredia MV, Elara MR (2019) Self-reconfigurable façade-cleaning robot equipped with deep-learning-based crack detection based on convolutional neural networks. Autom Constr 108:102959
Li M, Zhang M, Wang Q, Chow SS, Du M, Chen Y, Lit C, 2018, April. InstantCryptoGram: Secure image retrieval service. In: IEEE INFOCOM 2018-IEEE Conference on Computer Communications (pp. 2222–2230). IEEE, New York
Lin CH, Chen RT, Chan YK (2009) A smart content-based image retrieval system based on color and texture feature. Image Vis Comput 27(6):658–665
Madhavi KV, Tamilkodi R, Sudha KJ (2016) An innovative method for retrieving relevant images by getting the top-ranked images first using interactive genetic algorithm. Procedia Comput Sci 79:254–261
Pan H, Lei Y, Jian C (2018) Research on digital image encryption algorithm based on double logistic chaotic map. EURASIP J Image Video Process 2018(1):142
Pandey HM (2020) Secure medical data transmission using a fusion of bit mask oriented genetic algorithm, encryption and steganography. Futur Gener Comput Syst 111:213–225
Pavithra LK, Sharmila TS (2018) An efficient framework for image retrieval using color, texture and edge features. Comput Electr Eng 70:580–593
Rahim N, Ahmad J, Muhammad K, Sangaiah AK, Baik SW (2018) Privacy-preserving image retrieval for mobile devices with deep features on the cloud. Comput Commun 127:75–85
Shankar K, Eswaran P (2017) RGB based multiple share creation in visual cryptography with aid of elliptic curve cryptography. China Commun 14(2):118–130
Szegedy C, Liu W, Jia Y, Sermanet P, Reed S, Anguelov D, Erhan D, Vanhoucke V, Rabinovich A (2014) Going deeper with convolutions. arXiv 2014. arXiv preprint arXiv:1409.4842, 1409
Szegedy C, Ioffe S, Vanhoucke V, Alemi AA (2017) Inception-v4, Inception-Resnet and the Impact of Residual Connections on Learning, Thirty-First AAAI Conference on Artificial Intelligence
Wang H, Xia Z, Fei J, Xiao F (2020) An AES-based secure image retrieval scheme using random mapping and BOW in cloud computing. IEEE Access 8:61138–61147
Xia Z, Wang X, Zhang L, Qin Z, Sun X, Ren K (2016) A privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing. IEEE Trans Inf Forensics Secur 11(11):2594–2608
Xia Z, Ma X, Shen Z, Sun X, Xiong NN, Jeon B (2018) Secure image LBP feature extraction in cloud-based smart campus. IEEE Access 6:30392–30401
Xu Y, Zhao X, Gong J (2019) A large-scale secure image retrieval method in cloud environment. IEEE Access 7:160082–160090
Youssef SM (2012) ICTEDCT-CBIR: Integrating curvelet transform with enhanced dominant colors extraction and texture analysis for efficient content-based image retrieval. Comput Electr Eng 38(5):1358–1376
Yuan BH, Liu GH (2020) Image retrieval based on gradient-structures histogram. Neural Comput Appl 32(15):11717–11727
Zhang C, Zhu L, Zhang S, Yu W (2020) TDHPPIR: an efficient deep hashing based privacy-preserving image retrieval method. Neurocomputing 406:386–398
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Punithavathi, R., Ramalingam, A., Kurangi, C. et al. Secure content based image retrieval system using deep learning with multi share creation scheme in cloud environment. Multimed Tools Appl 80, 26889–26910 (2021). https://doi.org/10.1007/s11042-021-10998-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-10998-7