Abstract
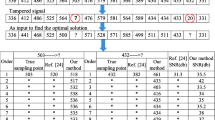
Authentication of encrypted speeches is a technique that can judge the integrity of encrypted speech in cloud computing, even the encrypted speeches have been subjected to common signal processing operations. In this paper, a novel and effective authentication scheme for encrypted speech is proposed. At first, the host speech signal is first scrambled and encrypted by Advanced Encryption Standard (AES). Then, Integer Wavelet Transform (IWT) is performed to obtain the approximation coefficients and the detail coefficients. At last, Non-negative Matrix Factorization (NMF) is employed to generate perceptual hashing, which is embedded into the encrypted speech by differential expansion. In authentication section, the tampered region of encrypted speech is located by comparing the reconstructed perceptual hashing with the extracted perceptual hashing version. Extensive experiments are carried out, which demonstrate that the proposed scheme is not only sensitive to malicious tampering of encrypted speech files, but also robust to tolerate common signal processing operations. The comparison shows that our algorithm performs better than the existing methods on Bit Error Rate (BER) values.













Similar content being viewed by others
References
Aakanksha T, Gupta BB (2019) A novel ECC-based lightweight authentication protocol for internet of things devices. Int J High Perform Comput Netw 15(1–2):106–120
Abdulla AA (2015) Exploiting similarities between secret and cover images for improved embedding efficiency and security in digital steganography [D]. PhD Thesis, Department of Applied Computing, The University of Buckingham, vol 1. pp 1–235
Ali S, Hafeez Y, Zaman N, Humayun M, Ra IH (2020) Towards pattern-based change verification framework for cloud-enabled healthcare component-based. IEEE Access 8:148007–148020
Alsmirat M, Alem FA, Ayyoub MA, Jaraweh Y, Gupta BB (2019) Impact of digital fingerprint image quality on the fingerprint recognition accuracy. Multimed Tools Appl 78:3649–3688
Chen OTC, Liu CH (2007) Content-dependent watermarking scheme in compressed speech with identifying manner and location of attacks. IEEE Trans Audio Speech Lang Process 15(5):1605–1616
Chen YC, Shiu CW, Horng G (2014) Encrypted signal-based reversible data hiding with public key cryptosystem. J Vis Commun Image Represent 25(5):1164–1170
Chen J, Zheng P, Guo J, Zhang W, Huang J (2018) A privacy-preserving multipurpose watermarking scheme for audio authentication and protection, 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering, pp. 86–91
Deep G, Mohana R, Nayyar A, Sanjeevikumar P, Hossain E (2019) Authentication Protocol for Cloud Databases Using Blockchain Mechanism. Sensors (Basel) 19(20):4444
EBU.: Sqam-sound quality assessment material Website (n.d.) . Retrieved October 20, 2018, from http://sound.media.mit.edu/resources/mpeg4/audio.html
El-latif AAA, El-atty BA, Hossain MS, Rahman MA, Alamri A, Gupta BB (2018) Efficient quantum information hiding for remote medical image sharing. IEEE Access 6:2169–3536
Fan MQ, Liu PP, Wang HX, Li HJ (2013) A semi-fragile watermarking scheme for authenticating audio signal based on dual-tree complex wavelet transform and discrete cosine transform. Int J Comput Math 90(12):2588–2602
Gupta S, Cho S, Kuo CCJ (2012) Current developments and further trends in audio authentication. IEEE Multimed 19(1):50–59
Hua G, Huang JW, Shi YQ, Goh J, Thing VL (2016) Twenty years of digital audio watermarking a comprehensive review. Signal Process 128(c):222–242
Kaushik S, Gandhi C (2019) Ensure Hierarchal Identity Based Data Security in Cloud Environment. Int J Cloud Appl Comput (IJCAC), IGI Global 9(4):21–36
Lee DD, Seung HS (2000) Algorithms for non-negative matrix factorization Neural Inf Process Syst, pp. 556–562
Lei BY, Soon IY, Li Z (2011) Blind and robust audio watermarking scheme based on SVD-DCT. Signal Process 91(8):1973–1984
Li DM, Deng LB, Gupta BB, Wang HX, Choi C (2019) A novel CNN based security guaranteed image watermarking generation scenario for smart city applications. Inf Sci 479:432–447
Liu YL, Peng H, Wang J (2018) Verifiable diversity ranking search over encrypted outsourced data. Comput Mater Contin 55(1):37–57
Meng RH, Steven GR, Wang J, Sun XM (2018) A fusion steganographic algorithm based on faster R-CNN. Comput Mater Contin 55(1):1–16
Nayyar A (2019) Handbook of cloud computing: basic to advance research on the concepts and design of cloud computing [M]. BPB Publications 1–413
Qerem AA, Alauthman M, Almomani A, Gupta BB (2020) IoT transaction processing through cooperative concurrency control on fog-cloud computing environment. Soft Comput 24:5695–5711
Qian Q, Cui YH, Wang HX, Deng MS (2020) REPAIR: fragile watermarking for encrypted speech authentication with recovery ability. Telecommun Syst 75(3):273–289
Qian Q, Wang HX, Sani MA, Wang H, Shi CH (2016) Speech authentication and recovery scheme in encrypted domain, Proceedings of 15th International Workshop on Digital-forensics and Watermarking, September 17–19, pp. 46–60, Beijing, China
Qian Q, Wang HX, Sun XM, Cui YH, Wang H, Shi CH (2018) Speech authentication and content recovery scheme for security communication and storage. Telecommun Syst 67(4):635–649
Saurabh S, Young-Sik J, Jong HP (2016) A survey on cloud computing security: Issues, threats, and solutions. J Netw Comput Appl 75:200–222
Shen J, Shen J, Chen XF, Huang XY, Susilo W (2017) An efficient public auditing protocol with novel dynamic structure for cloud data. IEEE Trans Inf Forensic Secur 12(10):2402–2415
Singh SP, Kumar R, Sharma A, et al (2020) Leveraging energy‐efficient load balancing algorithms in fog computing. Concurrency and Computation: Practice and Experience 1–16. https://doi.org/10.1002/cpe.5913
Singh SP, Nayyar A, Kumar R, Sharma A (2019) Fog computing: from architecture to edge computing and big data processing. J Supercomput 75:2070–2105
Singh S, Sharma PK, Moon SY, Moon D, Park JH (2019) A comprehensive study on APT attacks and countermeasures for future networks and communications: challenges and solutions. J Supercomput 75(8):4543–4574
Singh S, Sharma PK, Moon SY et al (2017) Advanced lightweight encryption algorithms for IoT devices: survey, challenges and solutions. J Ambient Intell Human Comput 1–18. https://doi.org/10.1007/s12652-017-0494-4
Wang JW, Li T, Shi YQ, Lian SG, Ye JY (2017) Forensics feature analysis in quaternion wavelet domain for distinguishing photographic images and computer graphics. Multimed Tools Appl 76(22):23721–23737
Wu HZ, Shi YQ, Wang HX, Zhou LN (2017) Separable reversible data hiding for encrypted palette images with color partitioning and flipping verification. IEEE Trans Circ Syst Video Technol 27(8):1620–1631
Xia ZH, Wang XH, Zhang LG, Qin Z, Sun XM, Ren K (2016) A privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing. IEEE Trans Inf Forensic Secur 11(11):2594–2608
Xiang SJ, Luo XR (2018) Reversible data hiding in homomorphic encrypted domain by mirroring ciphertext group. IEEE Trans Circ Syst Video Technol 28(11):3099–3110
Xiang SJ, Luo XR, Shi SX (2016) A novel reversible image watermarking algorithm in homomorphic encrypted domain. Chin J Comput 39(3):571–581
Yang J, Wang LM, Baek J (2018) A privacy preserving and fine-grained access control scheme in DaaS based on efficient DSP re-encryption. Int J High Perform Comput Netw 11(3):231–241
Zhang XP (2012) Separable reversible data hiding in encrypted image. IEEE Trans Inf Forensic Secur 7(2):826–832
Zhang Y, Qin C, Zhang WM, Liu FL, Luo XY (2018) On the fault-tolerant performance for a class of robust image steganography. Signal Process 146:99–111
Zheng Q, Wang X, Khurram Khan M, Zhang W, Gupta BB, Guo W (2018) A lightweight authenticated encryption scheme based on chaotic SCML for railway cloud service. IEEE Access 6:711–722
Zhu SS, Han YL (2018) Secure data outsourcing scheme in cloud computing with attribute-based encryption. Int J High Perform Comput Netw 12(2):128
Acknowledgments
This work is supported by the National Natural Science Foundation of China (NSFC) under Grants 61972269, and the Fundamental Research Funds for the Central Universities under Grant YJ201881, and by the Scientific Research Foundation of the Education Department of Sichuan Province (17ZA0063). The authors would like to thank Dr. Hanzhou Wu for valuable suggestions and discussion.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Shi, C., Wang, H., Hu, Y. et al. A novel NMF-based authentication scheme for encrypted speech in cloud computing. Multimed Tools Appl 80, 25773–25798 (2021). https://doi.org/10.1007/s11042-021-10896-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-10896-y