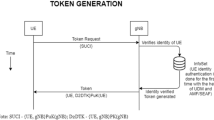
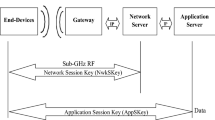
Abstract
With the increase in mobile traffic and the band-width demand, Device-to-Device (D2D) communication has gained tremendous interest by the researchers, cellular operators and equipment manufacturers. However, D2D communication has been limited to study the converge services at cell edge. D2D users that located outside the cellular network coverage haven’t received enough attention. Some of the problems faced in this case are discovering process of neighbor user equipment (UE) and services, as well as designing suitable and secure protocols for D2D communication. Toward these problems, in this paper, we propose security enhancement for D2D communication based on modified elliptic curve cryptography (MECC), which provides greater efficiency in computational overhead, key sizes and bandwidths for user’s authentication applied on proactive routing protocol for neighbor and service discovery. We study Diffie–Hellman, ElGamal and MECC techniques to improve service of D2D users at cell edge. Results show that the proposed scheme can strength the secrecy with less control overhead and can increase the robustness in a wide range of scenarios for service discovery in D2D networks.














Similar content being viewed by others
References
Abdellatif S, Tibermacine O, Bechkit W, Bachir A (2020) Efficient distributed D2D ProSe-based service discovery and querying in disaster situations. Adv Inf Netw Appl Adv Intell Syst Comput 115:910–921
Adhikari S, Ray S, Biswas GP, Obaidat MS (2018) Efficient and secure business model for content centric network using elliptic curve cryptography. Int J Commun Syst 32(1) e3839
Ahishakiye F, Li FY (2014) Service discovery protocols in D2D-enabled cellular networks: Reactive versus proactive. 2014 IEEE Globecom Workshops (GC Wkshps)
Al-Ayyoub M, Al-Andoli M, Jararweh Y, Smadi M, Gupta B (2019) Improving fuzzy C-mean-based community detection in social networks using dynamic parallelism. Comput Electr Eng 74:533–546
Almiani M, Razaque A, Aidja T, Dmour AA (2018) Context-aware latency reduction protocol for secure encryption and decryption. Int J High Perform Comput Netw 12(3):251
Alvarez R, Caballero-Gil C, Santonja J, Zamora A (2017) Algorithms for Lightweight Key Exchange †. Sensors 17(7):1517
Bharathi R, Rangasamy RS (2019) Software reliability assessment of safety critical system using computational intelligence. Int J Softw Sci Comput Intell 11(3):1–25
Cao M, Wang L, Xu H, Chen D, Lou C, Zhang N, Zhu Y, Qin Z (2019) Sec-D2D: a secure and lightweight D2D communication system with multiple sensors. IEEE Access 7:33759–33770
Elgamal T (1985) A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans Inf Theory 31(4):469–472
Hussein H, Elsayed H, El-Kader A, Sherine (2019) Intensive benchmarking of D2D communication over 5G cellular networks: prototype, integrated features, challenges, and main applications. Wirel Netw 26:3183–3202. https://doi.org/10.1007/s11276-019-02131-2
Javed Y, Khan A, Qahar A (2018) EEoP: A Lightweight Security Scheme over PKI in D2D Cellular Networks 9:3–11
Khalique A, Singh K, Sood S (2010) Implementation of elliptic curve digital signature algorithm. Int J Comput Appl 2(2):21–27
Kim S (2019) A new multicasting device-to-device communication control scheme for virtualized cellular networks. Wirel Commun Mob Comput 2019. 1–9. https://doi.org/10.1155/2019/3540674.
Kota S, Padmanabhuni VNR, Budda K, Sruthi K (2018) Authentication and encryption using modified elliptic curve cryptography with particle swarm optimization and cuckoo search algorithm. J Inst Eng (India): Series B 99(4):343–351
Nasraoui L, Atallah LN (2017) SRS-based D2D neighbor discovery scheme for LTE cellular networks. 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC)
Olakanmi OO, Dada A (2019) An efficient privacy-preserving approach for secure verifiable outsourced computing on untrusted platforms. Int J Cloud Appl Comput 9(2):79–98
Qureshi B (2018) An affordable hybrid cloud based cluster for secure health informatics research. Int J Cloud Appl Comput 8(2):27–46
Roy S, Khatwani C (2017) Cryptanalysis and improvement of ECC based authentication and key exchanging protocols. Cryptography 1(1):9
Shen W, Hong W, Cao X, Yin B, Shila DM, Cheng Y (2014) Secure key establishment for device-to-device communications 2014 IEEE Global Communications Conference
Stamp M (2011) Information security: principles and practice. Wiley, Hoboken
Sun Y, Cao J, Ma M, Li H, Niu B, Li F (2019) Privacy-preserving device discovery and authentication scheme for d2d communication in 3GPP 5G HetNet. 2019 International Conference on Computing, Networking and Communications (ICNC)
Tayeb S, Ruiz A, Latifi S (2019) Secure device discovery in big data communications networks: opportunities and challenges. Int Journal of e-Educ e-Bus e-Manag e-Learn 9(2):108–115
Vassilev TS, Twizell A (2013) Cryptography: a comparison of public key systems. Algorithms Res 1(5):31–42
Wang W, Teh KC, Li KH (2016) Enhanced physical layer security in D2D Spectrum sharing networks. IEEE Wirel Commun Lett 1–1 6(1):106–109
Wang J, Tang Q, Yang C, Schober R, Li J (2016) Security enhancement via device-to-device communication in cellular networks. IEEE Signal Process Lett 23(11):1622–1626
Waqas M, Ahmed M, Li Y, Jin D, Chen S (2018) Social-aware secret key generation for secure device-to-device communication via trusted and non-trusted relays. IEEE Trans Wirel Commun 17(6):3918–3930
Yan Z, Xie H, Zhang P, Gupta BB (2017) Flexible data access control in D2D communications. Futur Gener Comput Syst 82:738–751. https://doi.org/10.1016/j.future.2017.08.052
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Hussein, A., El-Rabaie, S. & El-Mashed, M.G. Proactive discovery protocol with security enhancement for D2D communication system. Multimed Tools Appl 80, 5047–5066 (2021). https://doi.org/10.1007/s11042-020-09799-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-09799-1