Abstract
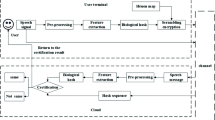
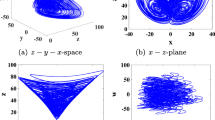
In order to solve the problems of poor security and small application scope of speech content authentication, and to improve the robustness, discrimination and real-time performance of speech authentication, a multi-format speech BioHashing algorithm based on energy to zero ratio and improved linear prediction minimum mean square error (LP-MMSE) parameter fusion is proposed. Firstly, the algorithm extracts the short-term logarithmic energy, zero-crossing rate and the covariance method’s LP-MMSE of speech signal to be processed. Then, the time-frequency parameters are fused, and the fused feature vector and the orthogonal normalized random matrix of the key control are generated into BioHashing sequences through the inner product form. Finally, the BioHashing is encrypted by equal-length scrambling using henon chaotic map. The experimental results show that the proposed algorithm not only has the characteristics of good discrimination, strong robustness, good security, high real-time performance and wide application range, but also realizes the detection and localization of small-scale tampering of speech through minimum code distance (MCD) algorithm. At the same time, the algorithm also validates the unidirectionality of BioHashing with trapdoor by comparative difference method.




















Similar content being viewed by others
References
Aghili SF, Mala H, Shojafar M, Peris-Lopez P (2019) Laco: lightweight three-factor authentication, access control and ownership transfer scheme for e-health systems in iot. Futur Gener Comput Syst 96:410–424
Alpar O, Krejcar O (2018) Online signature verification by spectrogram analysis. Appl Intell 48(5):1189–1199
Amin R, Biswas GP (2015) A secure three-factor user authentication and key agreement protocol for tmis with user anonymity. Journal of medical systems 39(8):78
Atighehchi K, Ghammam L, Barbier M, Rosenberger C (2019) Greyc-hashing: Combining biometrics and secret for enhancing the security of protected templates. Futur Gener Comput Syst 101:819– 830
Awais A, Kun S, Yue Y, Hayat S, Ahmed A, Tu T (2018) Speaker recognition using mel frequency cepstral coefficient. In: 2018 international conference on artificial intelligence and big data (ICAIBD), IEEE, pp 271–276
Chen N, Wan W, Xiao H-D (2010) Robust audio hashing based on discrete-wavelet-transform and non-negative matrix factorisation. IET communications 4(14):1722–1731
Chen Y, Wo Y, Xie R, Chudan W, Han G (2019) Deep secure quantization: on secure biometric hashing against similarity-based attacks. Signal Process 154:314–323
Chen N, Xiao H-D (2013) Perceptual audio hashing algorithm based on zernike moment and maximum-likelihood watermark detection. Digit Signal Process 23(4):1216–1227
Huang Y-B, Zhang Q-Y (2017) Strong robustness hash algorithm of speech perception based on tensor decomposition model. J Softw Eng 11:22–31
Huang Y-B, Zhang Q-Y, Wen-Jin H (2018) Robust speech perception hashing authentication algorithm based on spectral subtraction and multi-feature tensor. IJ Netw Secur 20(2):206–216
Jin Z, Hwang JY, Lai Y-L, Kim S, Teoh ABJ (2017) Ranking-based locality sensitive hashing-enabled cancelable biometrics: Index-of-max hashing. IEEE Trans Inform Forensics Secur 13(2):393–407
Kim H-G, Cho H-S, Kim JY (2016) Robust audio fingerprinting using peak-pair-based hash of non-repeating foreground audio in a real environment. Clust Comput 19(1):315–323
Kumar D, Grover HS et al (2019) A secure authentication protocol for wearable devices environment using ecc. J Inform Secur Appl 47:8–15
Kumari S, Li X, Fan W, Das AK, Choo K-KR, Shen J (2017) Design of a provably secure biometrics-based multi-cloud-server authentication scheme. Futur Gener Comput Syst 68:320–330
Li J, Wang H, Yi J (2015) Audio perceptual hashing based on nmf and mdct coefficients. Chin J Electron 24(3):579–588
Li J, Wu T (2015) Perceptual audio hashing using rt and dct in wavelet domain. In: 2015 11th international conference on computational intelligence and security (CIS), IEEE, pp 363–366
Liu J, Li J, Ma J, Sadiq N, Bhatti UA, Ai Y (2019) A robust multi-watermarking algorithm for medical images based on dtcwt-dct and henon map. Appl Sci 9(4):700
Lotia P, Khan DMR (2013) Significance of complementary spectral features for speaker recognition. IJRCCT 2(8):579–588
Lumini A, Nanni L (2007) An improved biohashing for human authentication. Pattern recognition 40(3):1057–1065
Qi J, Chen Z, Li B, Shen J, Li Y, Ma J (2018) Security analysis and improvement of bio-hashing based three-factor authentication scheme for telecare medical information systems. J Ambient Intell Human Comput 9(4):1061–1073
Qian Q, Wang H, Sun X, Cui Y, Wang H, Shi C (2018) Speech authentication and content recovery scheme for security communication and storage. Telecommun Syst 67(4):635–649
Qiao S, Zhang T, Huang Y (2017) A fast speech feature extraction method based on perceptual hashing. In: 2017 13th international conference on natural computation, fuzzy systems and knowledge discovery (ICNC-FSKD),IEEE, pp 1295–1300
Qiuyu Z, Pengfei X, Yibo H, Ruihong D, Zhongping Y (2018) An efficient speech perceptual hashing authentication algorithm based on dwt and symmetric ternary string. Int J Inf Commun Technol 12(1-2):31–50
Sheela SJ, Suresh KV, Tandur D (2018) Image encryption based on modified henon map using hybrid chaotic shift transform. Multimed Tools Appl 77 (19):25223–25251
Siddavatam I, Khatri D, Ashar P, Parekh V, Sharma T (2019) Authentication using dynamic question generation. In: Integrated intelligent computing, communication and security. Springer, New York, pp 293–300
Srinivas J, Mishra D, Mukhopadhyay S, Kumari S, Guleria V (2019) An authentication framework for roaming service in global mobility networks. Inform Technol Control 48(1):129–145
Teoh ABJ, Kuan YW, Lee S (2008) Cancellable biometrics and annotations on biohash. Pattern Recog 41(6):2034–2044
Verma G, Liao M, Dajiang L, He W, Peng X (2019) A novel optical two-factor face authentication scheme. Opt Lasers Eng 123:28–36
Wang C, Wang X, Li Y, Xia Z, Zhang C (2018) Quaternion polar harmonic fourier moments for color images. Inf Sci 450:141–156
Wang C, Wang X, Xia Z, Ma B, Shi Y-Q (2019), Image description with polar harmonic fourier moments. IEEE Trans Circ Syst Video Technol
Wang C, Wang X, Xia Z, Zhang C (2019) Ternary radial harmonic fourier moments based robust stereo image zero-watermarking algorithm. Inf Sci 470:109–120
Wodecki J, Kruczek P, Bartkowiak A, Zimroz R, Wyłomańska A (2019) Novel method of informative frequency band selection for vibration signal using nonnegative matrix factorization of spectrogram matrix. Mech Syst Signal Process 130:585–596
Xia Zhiqiu, Wang Xingyuan, Zhou Wenjie, Li Rui, Wang Chunpeng, Zhang Chuan (2019) Color medical image lossless watermarking using chaotic system and accurate quaternion polar harmonic transforms. Signal Process 157:108–118
Yenigalla P, Kumar A, Tripathi S, Singh C, Kar S, Vepa J (2018) Speech emotion recognition using spectrogram & phoneme embedding. In: Interspeech, pp 3688–3692
Zhang Q-Y, Ge Z-X, Qiao S-B (2018) An efficient retrieval method of encrypted speech based on frequency band variance. J Inform Hiding Multimed Signal Process 9:1452–1463 11
Zhang Q-Y, Qiao S-B, Huang Y-B, Zhang T (2018) A high-performance speech perceptual hashing authentication algorithm based on discrete wavelet transform and measurement matrix. Multimed Tools Appl 77(16):21653–21669
Zhang Q, Qiao S, Zhang T, Huang Y (2017) Perception hashing authentication algorithm for multi-format audio based on energy to zero ratio. J Huazhong Univ Sci Technol (Nat Sci Edition) 45(9):33–38
Zhang Q-Y, Wen-jin H, Huang Y-B, Qiao S-B (2018) An efficient perceptual hashing based on improved spectral entropy for speech authentication. Multimed Tools Appl 77(2):1555–1581
Zhang Q-Y, Wen-jin H, Qiao S-B, Zhang T (2016) An efficient speech perception hash authentication algorithm based on the linear prediction minimum mean squared error. J Huazhong Univ Sci Technol (Nat Sci Edition) 44 (12):127–132
Zhang Q-Y, Xing P-F, Huang Y-B, Dong R-H, Yang Z-P (2015) An efficient speech perceptual hashing authentication algorithm based on wavelet packet decomposition. J Inform Hiding Multimed Signal Process 6(2):311–322
Zhang Q-Y, Xing P-F, Huang Y-B, Dong R-H, Yang R-H (2016) Perception hashing algorithm for multi-format audio. J Beijing Univ Posts Telecommun 39(4):77–82
Zhang Q-Y, Zhang T, Dong-Fang W, Ge Z-X (2018) Strong robust speech authentication algorithm based on quasi-harmonic model. J Huazhong Univ Sci Technol (Nat Sci Edition) 46(3):58–64
Zhang X, Zhang J, He T, Chen Y, Shen Y, Xu X (2018) A speech and lip authentication system based on android smart phone. In: Proceedings of the 6th international conference on information technology: IoT and Smart City, ACM, pp 110–114
Acknowledgements
This work is supported by the National Natural Science Foundation of China(No.61862041), Youth Science and Technology Fund of Gansu Province of China(No.1606RJYA274).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, Y., Huang, Yb., Zhang, R. et al. Multi-format speech BioHashing based on energy to zero ratio and improved LP-MMSE parameter fusion. Multimed Tools Appl 80, 10013–10036 (2021). https://doi.org/10.1007/s11042-020-09701-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-09701-z