Abstract
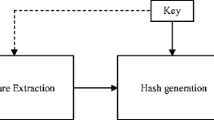
This paper presents a novel Binary Multi-View Perceptual Hashing (BMVPH) scheme for image authentication, which provides compact and efficient representations and can easily scale to large data. We apply virtual prior attacks (e.g. additive noise, blurring, compression, logo-insert etc.) on original images to generate simulated distorted copies. The original images and the corresponding distorted copies provide the so-called training set. For perceptual hashing learning, we formulate BMVPH by two key components: collaborative binary representation learning (CBRL) and perpetual content authentication learning (PCAL), into a unified learning framework. Our BMVPH scheme collaboratively encodes the multi-view features into a compact common binary code space while considering the perceptual content similarity at the same time. The experimental results show that when compared with the state-of-the-art methods, the proposed algorithm can achieve higher discrimination and better perceptual robustness. In particular, the Area Under ROC Curve (AUC) increases on average of 3.8% as compared with other state-of-the-art methods.






Similar content being viewed by others
References
Abbas SQ, Ahmed F, Zivic N, and Ur-Rehman O (2016) “Perceptual image hashing using svd based noise resistant local binary pattern,” in International Congress on Ultra Modern Telecommunications and Control Systems and Workshops, 2016, pp. 401–407.
Anitha K and Leveenbose P (2015) “Edge detection based salient region detection for accurate image forgery detection,” in IEEE International Conference on Computational Intelligence and Computing Research, pp. 1–4
Bondi L, Lameri S, Guera D, Bestagini P, Delp EJ, and Tubaro S (2017) “Tampering detection and localization through clustering of camera-based cnn features,” 2017 IEEE Conference on Computer Vision and Pattern Recognition Workshops (CVPRW), pp. 1855–1864
Brbi M, Kopriva I (2018) Multi-view low-rank sparse subspace clustering. Pattern Recogn 73(2):247–258
Chen Y, Yu W, Feng J (2014) Robust image hashing using invariants of tchebichef moments. Optik - International Journal for Light and Electron Optics 125(19):5582–5587
Du L, Chen Z, Ke Y (2018) Image hashing for tamper detection with multi-view embedding and perceptual saliency. Advances in Multimedia 2018:1–11
Gao H, Nie F, Li X and Huang H (2015) “Multi-view Subspace Clustering,” in IEEE International Conference on Computer Vision, pp. 2380–7504
Ghouti L (2014) “Robust perceptual color image hashing using quaternion singular value decomposition,” in IEEE International Conference on Acoustics, Speech and Signal Processing, pp. 3794–3798
Hosny KM, Khedr YM, Khedr WI, and Mohamed ER (2018) “Robust image hashing using exact gaussian-hermite moments,” IET Image Processing, pp. 1–8
Huang Z and Liu S (2018) “Robustness and discrimination oriented hashing combining texture and invariant vector distance,” in Proceedings of the 26th ACM International Conference on Multimedia, 2018, pp. 1389–1397
Jgou H, Douze M, Schmid C (Jan. 2011) Product quantization for nearest neighbor search. IEEE Trans Pattern Anal Mach Intell 33(1):117–128
Jiang C, Pang Y (2018) Perceptual image hashing based on a deep convolution neural network for content authentication. Journal of Electronic Imaging 27(4):1–11
Kang LW, Lu CS, and Hsu CY (2010) “Compressive sensing-based image hashing,” in IEEE International Conference on Image Processing, pp. 1277–1280
Khelifi F, Jiang J (2009) Analysis of the security of perceptual image hashing based on non-negative matrix factorization. IEEE Signal Processing Letters 17(1):43–46
Kim C (2003) Content-based image copy detection. Signal Process Image Commun 18(3):169–184
Kozat SS, Mihcak K, Venkatesan R (2004) “Robust perceptual image hashing via matrix invariances,” in IEEE Conf. on Image Processing, pp. 3443–3446
Kulis B and Grauman K (2010) “Kernelized locality-sensitive hashing for scalable image search,” in in Proc. IEEE 12th Int. Conf. Computer Vision, pp. 2130–2137
Lefebvre F, Czyz J, Macq B (2003) “A robust soft hash algorithm for digital image signature,” in in Proc. IEEE Int. Conf. Image Processing (ICIP), vol. 2, pp. 495–498
Lei Y, Wang Y-G, Huang J (2011) Robust image hash in radon transform domain for authentication. 26:280–288
Liu W, Wang J, Kumar S, and Chang SF (2011) “Hashing with graphs,” in in Proc. 28th Int. Conf. Machine Learning (ICML), pp. 1–8
Liu W, Wang J, Ji R, Jiang YG, and Chang SF (2012) “Supervised hashing with kernels,” in in Proc. IEEE Conf. Computer Vision and Pattern Recognition (CVPR), pp. 2074–2081.
Liu H, Xiao D, Xiao Y, Zhang Y (2016) Robust image hashing with tampering recovery capability via low-rank and sparse representation. Multimed Tools Appl 75(13):7681–7696
Lv X, Wang ZJ (2009) An extended image hashing concept: content based fingerprinting using fjlt. EURASIP J Inf Security 2009(1):1–17
Lv X and Wang ZJ (2009) “An extended image hashing concept: Content-based fingerprinting using fjlt,” EURASIP J. Information Security, vol. 2009
Lv X, Wang ZJ (2012) Perceptual image hashing based on shape contexts and local feature points. IEEE Trans. Inf. Forensics Security 7(3):1081–1093
Lv X, Wang ZJ (2012) Perceptual image hashing based on shape contexts and local feature points. IEEE Transactions on Information Forensics and Security 7:1081–1093
Lv X, Wang A (Nov. 2013) Compressed binary image hashes based on semisupervised spectral embedding. IEEE Trans Inf Forensics Security 8(11):1838–1849
Monga V and Evans B (2004) “Robust perceptual image hashing using feature points,” in 2004 International Conference on Image Processing, pp. 677–680
Monga V, Evans B (2006) Perceptual image hashing via feature points: performance evaluation and tradeoffs. IEEE Trans Image Process 15(11):3452–3465
Monga V, Mhcak M (Sep. 2007) Robust and secure image hashing via nonnegative matrix factorizations. IEEE Trans. Inf. Forensics Security 2(3):376–390
Monga V, Mihcak MK (2007) Robust and secure image hashing via non-negative matrix factorizations. IEEE Transactions on Information Forensics and Security 2:376–390
Mu Y, Shen J, and Yan S (2010) “Weakly-supervised hashing in kernel space,” in in Proc. IEEE Conf. Computer Vision and Pattern Recognition (CVPR), pp. 3344–3351.
Nguyen DQ, Weng L, and Preneel B (2011) “Radon transform-based secure image hashing,” in Communications and Multimedia Security
Ouyang J, Coatrieux G, Shu H (2015) Robust hashing for image authentication using quaternion discrete fourier transform and log-polar transform. Digital Signal Processing 41:98–109
Ouyang J, Wen X, Liu J, and Chen J (2016) “Robust hashing based on quaternion zernike moments for image authentication,” Acm Transactions on Multimedia Computing Communications and Applications, vol. 12, no. 4s, p. 63
Pun CM, Yan CP, and Yuan X (2017) “Robust image hashing using progressive feature selection for tampering detection,” Multimedia Tools and Applications, vol. 77, pp. 11 609–11 633
Qin C, Chang C-H, Tsou P-L (2013) Robust image hashing using non-uniform sampling in discrete fourier domain. Digital Signal Processing 23(2):578–585
Qin C, Chen X, Dong J, Zhang X (2016) Perceptual image hashing with selective sampling for salient structure features. Displays 45:26–37
Qin C, Chen X, Luo X, Xinpeng Z, Sun X (2018) Perceptual image hashing via dual-cross pattern encoding and salient structure detection. Inf Sci 423:284–302
Qin C, Sun M, Chang C-C (2018) Perceptual hashing for color images based on hybrid extraction of structural features. Signal Process 142:194–205
C. Qin, Y. Hu, H. Yao, X. Duan, and L. Gao (2019) “Perceptual image hashing based on weber local binary pattern and color angle representation,” IEEE Access, vol. 7, pp. 45 460–45 471
Salakhutdinov R, Hinton G (2009) Semantic hashing. Int J Approx Reason 50(7):969–978
Srivastava M, Siddiqui J, and Ali MA (2017) “Robust image hashing based on statistical features for copy detection,” in IEEE Uttar Pradesh Section International Conference on Electrical, Computer and Electronics Engineering, pp. 490–495
Strecha MBC, Bronstein A (Jan. 2012) Ldahash: improved matching with smaller descriptors. IEEE Trans Pattern Anal Mach Intell 34(1):66–78
Sun R, Zeng W (2014) Secure and robust image hashing via compressive sensing. Multimed Tools Appl 70(3):1651–1665
Sun R, Yan X, and Ding Z (2011) “Robust image hashing using locally linear embedding,” in International Conference on Computer Science and Service System, pp. 715–718
Swaminathan A, Mao Y, Wu M (2006) Robust and secure image hashing. IEEE Trans. Inf. Forensics Security 1(2):215–230
Tagliasacchi M, Valenzise G, Tubaro S (2009) Hash-based identification of sparse image tampering. IEEE Trans Image Process 18(11):2491–2504
Tang Z, Wang S, Zhang X, Wei W, Zhao Y (2011) Lexicographical framework for image hashing with implementation based on dct and nmf. Multimed Tools Appl 52(2–3):325–345
Tang Z, Huang L, Dai Y, Yang F (2012) Robust image hashing based on multiple histograms. International Journal of Digital Content Technology and its Applications 6(23):39–47
Tang Z, Zhang X, Huang L, Dai Y (2013) Robust image hashing using ring-based entropies. Signal Process 93(7):2061–2069
Tang Z, Yang F, Huang L, Zhang X (2014) Robust image hashing with dominant dct coefficients. Optik - International Journal for Light and Electron Optics 125(18):5102–5107
Tang Z, Dai Y, Zhang X, Huang L, Yang F (2014) Robust image hashing via colour vector angles and discrete wavelet transform. 8:142–149
Tang Z, Ruan L, Qin C, Zhang X, Yu C (2015) Robust image hashing with embedding vector variance of lle. Digital Signal Processing 43(C):17–27
Tang Z, Zhang X, Li X, Zhang S (2016) Robust image hashing with ring partition and invariant vector distance. IEEE Trans. Inf. Forensics Security 11(1):200–214
Tang Z, Zhang X, Li X, Zhang S (2016) Robust image hashing with ring partition and invariant vector distance. IEEE Transactions on Information Forensics and Security 11:200–214
Tang Z, Huang L, Zhang X, Lao H (2016) Robust image hashing based on color vector angle and canny operator. AEUE - International Journal of Electronics and Communications 70(6):833–841
Tang C, Zhu X, Liu X, Li M, Wang P, Zhang C, Wang L (2019) Learning a joint affinity graph for multiview subspace clustering. IEEE Transactions on Multimedia 21(7):1724–1736
Venkatesan MHJR, Koon SM and Moulin P (2000) “Robust image hashing,” in IEEE Conf. on Image Processing, pp. 664–666
Wang J, Kumar S, Chang S (Dec. 2012) Semi-supervised hashing for large-scale search. IEEE Trans Pattern Anal Mach Intell 34(12):2393–2406
Wang X, Xue J, Zheng Z, Liu Z, Li N (2012) Image forensic signature for content authenticity analysis. J Visual Communication and Image Representation 23:782–797
Wang X, Pang K, Zhou X, Zhou Y, Li L, Xue J (2015) A visual model-based perceptual image hash for content authentication. IEEE Trans. Inf. Forensics Security 10(7):1336–1349
P. Wang, A. Jiang, Y. Cao, Y. Gao, R. Tan, H. He, and M. Zhou (2018) “Robust image hashing based on hybrid approach of scale-invariant feature transform and local binary patterns,” in 2018 IEEE 23rd International Conference on Digital Signal Processing (DSP), 11, pp. 1–5
Weiss Y, Torralba A, and Fergus R (2008) “Spectral hashing,” in in Proc. Advances in Nerual Information Processing Systems, pp. 1753–1760.
Yan C-P, Pun C-M (2017) Multi-scale difference map fusion for tamper localization using binary ranking hashing. IEEE Transactions on Information Forensics and Security 12:2144–2158
C.-P. Yan, C.-M. Pun, and X.-C. Yuan (2015) “Adaptive local feature based multi-scale image hashing for robust tampering detection,” TENCON 2015–2015 IEEE Region 10 Conference, pp. 1–4
Yan C, Pun C, Yuan X (2016) Quaternion-based image hashing for adaptive tampering localization. IEEE Trans. Inf. Forensics Security 11(12):2664–2677
Yan C-P, Pun C-M, Yuan X (2016) Quaternion-based image hashing for adaptive tampering localization. IEEE Transactions on Information Forensics and Security 11:2664–2677
Yan CP, Pun CM, Yuan XC (2016) Multi-scale image hashing using adaptive local feature extraction for robust tampering detection. Signal Process 121:1–16
Yang L, Chen Q, Tian J, Wu D (2011) Content based image hashing using companding and gray code. Security and Communication Networks 4(12):1378–1386
Yarlagadda SK, Güera D, Bestagini P, Zhu FM, Tubaro S, and Delp EJ (2018) “Satellite image forgery detection and localization using gan and one-class classifier,” CoRR, vol. abs/1802.04881
Zhan K, Zhang C, Guan J, Wang J (2018) Graph learning for multiview clustering. IEEE Transactions on Cybernetics 48(10):2887–2895
Zhan K, Nie F, Wang J, Yang Y (2019) Multiview consensus graph clustering. IEEE Trans Image Process 28(3):1261–1270
Zhan K, Niu C, Chen C, Nie F, Zhang C, Yang Y (2019) Graph structure fusion for multiview clustering. IEEE Trans Knowl Data Eng 31(10):1984–1993
D. Zhang, J. Chen, and B. Shao (2015) “Perceptual image hashing based on zernike moment and entropy,” Electronic Science and Technology
Zhang C, Hu Q, Fu H, Zhu P, Cao X (2017) “Latent Multi-view Subspace Clustering,” in IEEE Conference on Computer Vision and Pattern Recognition, pp. 1063–6919
Zhang Z, Liu L, Shen F, Shen HT, and Shao L (2018) “Binary multi-view clustering,” IEEE Transactions on Pattern Analysis and Machine Intelligence, vol. PP, no. 99, pp. 1–1
Zhang C, Fu H, Hu Q, Cao X, Xie Y, Tao D and Xu D, “Generalized Latent Multi-View Subspace Clustering,” IEEE Trans. Pattern Analysis and Machine Intelligencel, to be published
Zhao Y and Wei W (2010) “Perceptual image hash for tampering detection using zernike moments,” in IEEE International Conference on Progress in Informatics and Computing, pp. 738–742.
Zhao Y, Wang S, Zhang X, Yao H (2013) Robust hashing for image authentication using zernike moments and local features. IEEE Transactions on Information Forensics and Security 8(1):55–63
Zhaoqing L, Qiong L, Jingrui L, Xiyuan P (2011) Sift based image hashing algorithm. Chinese Journal of Scientific Instrument 32(9):2024–2028
Acknowledgments
This work was supported by National Natural Science Foundation of China (Grant No. 61602344), Science&Technology Development Fund of Tianjin Education Commission for Higher Education, China (Grant No. 2017KJ091) and Natural Science Foundation of Tianjin (Grant No. 17JCQNJC00600).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Du, L., Chen, Z. & Ho, A.T.S. Binary multi-view perceptual hashing for image authentication. Multimed Tools Appl 80, 22927–22949 (2021). https://doi.org/10.1007/s11042-020-08736-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-08736-6