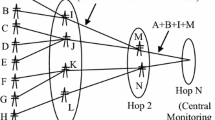
Abstract
The video traffic analysis is the most important issue for large scale surveillance. In the large scale surveillance system, huge amount of live digital video data is submitted to the storage servers through the number of externally connected scalable components. The system also contains huge amount of popular and unpopular old videos in the archived storage servers. The video data is delivered to the viewers, partly or completely on demand through a compact system. In real time, huge amount of video data is imported to the viewer’s node for various analysis purposes. The viewers use a number of interactive operations during the real time tracking suspect. The compact video on demand system is used in peer to peer mesh type hybrid architecture. The chunk of video objects move fast through the real time generated compact topological space. Video traffic analytics is required to transfer compressed multimedia data efficiently. In this work, we present a dynamically developed topological space, using mixed strategy by game approach to move the video traffic faster. The simulation results are well addressed in real life scenario.





















Similar content being viewed by others
References
Annapureddy S et al. (2007) Explorng VoD in swarming system, IEEE INFOCOM 2007, p 2571–2575, doi: 10.1109/INFCOM.2007.323
Asit D et al. (1994) Scheduling polices for an on demand video server with batching. Proc Multimed:15–23 doi:10.1145/192593.192614
Atrey PK, Kankanhalli MS, Jain R (2006) A framework for information assimilation in multimedia surveillance systems. ACM Multimed Syst J
Atrey PK, Kankanhalli MS, Saddik A E (2007) Confidence building among correlated streams in multimedia surveillance systems. MMM 2007, LNCS 4352, Part II, p 155–164
Ayesta U et al (2012) Sojourn times in a processor sharingqueue with multiple vacations. Queueing Syst 71(1):53–78
Bird ND, Masoud O, Papanikolopoulos NP, Isaacs A (Jun. 2005) Detection of loitering individuals in public transportation areas. IEEE Trans Intell Transp Syst 6(2):167–177
Bramberger M et al. (2014) Real-time video analysis on an embedded smart camera for traffic surveillance, 10th IEEE Real-Time and Embedded Technology and Applications Symposium (RTAS’04),p 174–181. doi:10.1109/rttas.2004.1317262
Coifman B, Beymer D, McLauchlan P, Malik J (1998) Areal time computer vision system for vehicle tracking and traffic surveillance. Trans Res Part -C 6:271–288. Elsevier Science
Collins R et al (2000) A system for video surveillance and monitoring, VSAM Final Report, Technical Report, CMURI-TR-00-12
Dufaux F, Ebrahimi T (2006) Scrambling for video surveillance with privacy. Proc. IEEE Workshop on Privacy Research in Vision, New York, NY
Hampapur A et al (2005) Smart video surveillance, exploring the concept of multiscale spatiotemporal tracking. IEEE Signal Process Mag 22(2):38–51. doi:10.1109/MSP.2005.1406476
Heartwell CH et al (2002) Critical asset protection, perimeter monitoring, and threat detection using automated video surveillance –a technology overview with case studies, Proceedings. 36th Annual 2002 International Carnahan Conference on Security Technology. doi:10.1109/CCST.2002.1049231
Jiang D et al (2014) How to reconstruct end –to-end traffic based on time-frequency analysis and artificial neural network. AEU - Int J Electron Commun 68(10):915–925
Jiang D et al (2014) A transform domainbased anomaly detection approach to network wide traffic. J Netw Comput Appl 40:292–306
Jiang D et al (2015) A novel hybrid prediction algorithm to network traffic. Ann Telecommun 70(9):427–439
Junejo IN, Javed O, Shah M (2004) Multi feature path modeling for video surveillance. Int Conf Pattern Recogn:716–719
Junejo IN, Javed O, Shah M (2004) Multi feature path modeling for video surveillance. In Int Conf Pattern Recog, Cambridge, England, UK, p 716–719
Kanrar S (2011) Performance of distributed video on demand system for multirate traffic. Int Conf ReTIS 2011:52–56. doi:10.1109/ReTIS.2011.6146839
Kanrar S, Mandal NK (2014) Dynamic page replacement at the cache memory for the video on demand server. Adv Comput Netw Inform 2:461–469. doi:10.1007/978-3-319-07350-7_51
Kanrar S et al (2015) Text and language independent speaker identification by GMM based I vector. ICCCT‘15–ACM proceeding, p 95–100. doi:10.1145/2818567.2818585
Kanrar S et al (2015) Detect mimicry by enhancing the speaker recognition system. Adv Intell Syst Comput 339:21–31. doi:10.1007/978-81-322-2250-7_3
Kanrar S (2015) Impact of threshold to identify vocal tract. Adv Intell Syst Comput 404:97–105. doi:10.1007/978-81-322-2695-6_9
Khoshabeh R, Gandhi T, Trivedi MM (2007) Multi camera based traffic flow characterization and classification. IEEEConf. Intell. Transport. Syst, p 259–264, Seattle,WA
Kwak S, Byun H (2011) Detection of dominant flow and abnormal events in surveillance video. Opt Eng 50(2):027202
Lee D et al (2001) LRFU: a spectrum of polices that subsumes the least recently used and least frequently used polices. IEEE Trans Comput 50(12):1352–1361
Li VOK, Liao W (2003) Interactive video-on-demand system, Patent US 6543053 B1, Publication
Liao H.-Y.M, Chen D.-T, Su C.-W, Tyan H.-R (2006) Real-time event detection and its application to surveillance systems. IEEE Int Symp Circuits Syst:509–512
Lu N et al. (2008) An improved motion detection method for real-time surveillance. Proc. of IAENG International Journal of Computer Science (1):1–16
Makris D, Ellis T (2005) Learning semantic scene models from ob-serving activity in visual surveillance. IEEE Trans Syst Man Cy-bernB 35(3):397–408
Morris BT, Trivedi MM (2008) Learning, modeling, and classification of vehicle track patterns from live video. IEEE Trans Intell Transp Syst 9(3):425–437
Morris BT et al (2012) Real-time video-based traffic measurement and visualization system for energy/emissions. IEEE Trans Intell Transp Syst 13(4):1667–1678
Muller-Schneiders S, Jager T, Loos H, Niem W (2005) Performance evaluation of a real time video surveillance system. Proc. of 2nd Joint IEEE Int. Workshop on Visual Surveillance and Performance Evaluation of Tracking and Surveillance (VS-PETS), p 137–144
Nie L et al (2013) A compressive sensing-based reconstruction approach to network traffic. Comput Electr Eng 39(5):1422–1432
Oner Sebe I et al. (2003) 3D Video surveillance with augmented virtual environments. ACM proceeding IWVS’03
Remagnino P, Velastin SA, Foresti GL, Trivedi M (Aug. 2007) Novel concepts and challenges for the next generation of video surveillance systems. Mach Vis Appl 18(3–4):135–137
Saleemi I, Shafique K, Shah M (2009) Probabilistic modeling of scene dynamics for applications in visual surveillance. IEEE Trans Pattern Anal Mach Intell 31(8):1472–1485. doi:10.1109/TPAMI.2008.175
Saroj Kumar R (2010) New terror architecture in South Asia 26/11 Mumbai attacks inquiry. J Int Aff (India Quarterly) 66(4):359–381. doi:10.1177/097492841006600403
Saunier N, Sayed T, Lim C (2007) Probabilistic collision prediction for vision-based automated road safety analysis. IEEE Conf. Intell Transport Syst, Seattle, pp 872–878, Washington
Shah M et al (2007) Automated surveillance in realistic scenarios. IEEE Multi Media 14(1):30–39. doi:10.1109/MMUL.2007.3
Shiang H-P, van der Schaar M (2010) Information-constrained resource allocation in multicamera wireless surveillance networks. IEEE Trans Circ Syst Video Technol 20(4):505–517. doi:10.1109/TCSVT.2009.2035837
Shrutivandana S, Demosthenis T (2009) Externalities-based decentralized optimal power allocation algorithm for wireless networks. IEEE/ACM Trans Netw 17(6):1819–1831. doi:10.1109/TNET.2009.2020162
Soumen K et al. (2016) Enhancement of video streaming in distributed hybrid architecture. Adv Multimed 2016, Article ID 5429187: 14, doi:10.1155/2016/5429187
Soumen K et al. (2016) Video traffic flow analysis in distributed system during interactive session. Adv Multimed 2016, Article ID 7829570:14, doi:10.1155/2016/7829570
Suh K, Diot C, Kurose J, Massoulié L, Neumann C, Towsley D, Varvello M (2006) Push-to-peer video-on-demand system: design and evaluation. Technical Report CR-PRL-2006-11-0001, Thomson Research
Suh K et al (2007) Push-to-peer video-on-demand system: design and evaluation. IEEE J Sel Areas Commun 25(9):1706–1716
Tan B, Massoulie L (2013) Optimal content placement for peer-to-peer video-on-demand systems. Networking. IEEE/ACM Trans Networking 21(2):566–579. doi:10.1109/tnet.2012.2208199
Turner-Fairbank-Highway Research Center (2013) Pedestrian and bicyclist intersection safety indices final report, http://www.fhwa.dot.gov/publications/research/safety/pedbike/06125/index.cfm
Victor O, Li K et al (1996) Performance model of interactive video-on-demand systerns. IEEE J Sel Areas Commun 14(6):1099–1109
Yoshitaka A, Sawada K (2012) Personalized video summarization based on behavior of viewers. In Eighth international conference on signal Image Technology and Internet Based Systems:1–7
Yu H et al. (2006) Understanding user behavior in large scale video-on-demand systems. ACM proceeding Euro Sys, Leuven, Belgium 06
Yunus D, Atay O, Cem E (2012) Distributed and Online Fair Resource Managment in Video Surveillance Sensor Networks. IEEE Trans Mob Comput 11(5):835–848. doi:10.1109/TMC.2011.115
Zhang X, Liu J, Li B, Yum T (2005) Cool Streaming/DONet: a data driven overlay network for live media streaming. In Proc. IEEE 3:2102–2111. doi: 10.1109/INFCOM.2005.1498486
Acknowledgments
The authors are grateful to Sharmista Das Kanrar from Bishop Westcott, Ranchi, India.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Kanrar, S., Mandal, N.K. Video traffic analytics for large scale surveillance. Multimed Tools Appl 76, 13315–13342 (2017). https://doi.org/10.1007/s11042-016-3752-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3752-0