Abstract
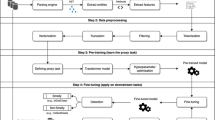
This paper puts forward one kind of behavioral characteristic extraction and detection method of malicious code based on semantic; it extracts the key behavior and dependence relations among behaviors by combining with stain spread analysis in command layer and semantic analysis in behavior layer. And then it uses anti-confusion engine identification semantic irrelevance and semantic equivalence behavior to obtain malicious code behavior characteristic with certain capacity of resisting disturbance, as well as realize characteristic extraction and detection on prototype system. It completes experimental demonstration on this system through analysis and detection on plenty of malicious code samples. The test result indicates that extraction characteristic based on the above methods has characteristic such as stronger capacity of resisting disturbance etc., detection based on this characteristic has better identification ability for malicious code.







Similar content being viewed by others
References
Anyanwu K, Maduko A, Sheth A (2005) SemRank: ranking complex relationship search results on the semantic web. In: Proc of the 14th international world wide web conference. ACM Press. pp 117–127
Anyanwu K, Sheth A (2003) ρ -Queries: enabling querying for semantic associations on the semantic web. In: Proc of the 12th international world wide web conference. ACM Press. pp 690–699 OpenURL
Diao M, Nicopoulos C, Jongman K (2011) Large-scale semantic concept detection on manycore platforms for multimedia mining. IEEE (1):384–394
Dong X, Ding Y, Wang H, Chen B, Wild DJ (2010) Ranking semantic associations in systems chemical biology space, 19th International World Wide Web Conference. FWCS, Raleigh
El-Semary AM, Gadal-Haqq M, Mostafa M (2010) Distributed and scalable intrusion detection system based on agents and intelligent techniques. JIPS 6(4):481–483
Goswami K, Hong G-S, Kim B-G (2013) A novel mesh-based moving object detection technique in video sequence. JOS 4(3):20–24
Ha H-Y, Fleites FC, Chen S-C, Chen M (2014) Correlation-based re-ranking for semantic concept detection. IEEE (10):765–770
Jiang X, Tan A (2009) Learning and inferencing in user ontology for personalized Semantic Web search. Inf Sci 179:2794–2808
Kolter JZ, Maloof MA (2004) Learning to detect malicious executables in the wild. In: Proceedings of the tenth ACM SIGKDD international conference on knowledge discovery and data mining. New York: ACM Press
Kumar KPK, Geethakumari G (2014) Detecting misinformation in online social networks using cognitive psychology. HCIS (9):4–9
Liu S, Cheng X, Fu W et al (2014) Numeric characteristics of generalized M-set with its asymptote [J]. Appl Math Comput 243:767–774
Liu S, Fu W, He L et al (2015) Distribution of primary additional errors in fractal encoding method [J]. Multimed Tools Appl. doi:10.1007/s11042-014-2408-1
Liu T, Zhang L, Li P et al (2012) Remotely sensed image retrieval based on region-level semanticmining. Springer. (4):1186–1687
Martens G, Verborgh R, Poppe C (2011) Lifting a metadata model to the semantic multimedia world. JOS 7(1):199–200
Min H-S, Choi JY, De Neve W, Ro YM (2012) Near-duplicate video clip detection using model-free semantic concept detection and adaptive semantic distance measurement. IEEE (8):1174–1187
Minsu KO, Woonho CHOI (2013) A dstributional inference for cross-lingual undefined entities linking. JOS 2(4):23–28
Mozgovoy M, Efimov R (2013) WordBricks: a virtual language lab inspired by Scratch environment and dependency grammars. HCIS 8:3–5
Nguyen NP, Yan G, Thai MT, Eidenbenz S (2012) Containment of misinformation spread in online social networks. In: Proceedings of the 3rd annual ACM web science conference. ACM, Illinois, USA. pp 213–222
Ning G, Xiaopin S, He L (2011) Detection on malicious code based on nature sequence. Comput Appl 31(4):1006–1009
Patil PB, Kokare MB (2013) Interactive semantic image retrieval. JIPS 9(3):349–364
Qazvinian V, Rosengren E, Radev DR, Mei Q (2011) Rumor has it: identifying misinformation in microblogs. In: Proceedings of the conference on empirical methods in natural language processing. Association for Computational Linguistics, Edinburg, UK. pp 1589–1599 OpenURL
Sun J, Zhan Y (2013) A Semi-supervised incremental learning algorithm based on auto-adaptive probabilistic hypergraph and its application for video semantic detection. IEEE (8) 743–749
Vidal M, Rashid L, Ibabez L, Rivera J, Rodrogiez H, Ruckhaus E (2010) A ranking-based approach to discover semantic association between linked data. The 2nd international workshop on inductive reasoning and machine learning for the semantic web 611:18–29 OpenURL
Viswanathan V, Krishnamurthi I (2012) Finding relevant semantic association paths through user-specific intermediate entities. HCIS 3:2–9
Viswanathan V, Krishnamurthi I (2012) Finding relevant semantic association paths through user-specific intermediate entities. HCIS (2):3–9
Weon I-Y, Song D-H, Ko S-B, Lee C-H (2013) A multiple instance learning problem approach model to anomaly network intrusion detection. JIPS (1):5–9
Acknowledgments
This work is sponsored by Science and Technology Program of Wuhan City under Grant No. 2014060101010029.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Lu, Q., Wang, Y. Detection technology of malicious code based on semantic. Multimed Tools Appl 76, 19543–19555 (2017). https://doi.org/10.1007/s11042-015-3228-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-3228-7