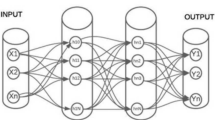
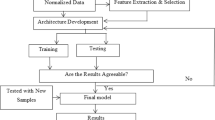
Abstract
Artificial immune system constructs a dynamic and adaptive information defense system through a function similar to the biological immune system. In order to resist the external invasion of useless and harmful information and ensure the effectiveness and the harmlessness of received information. Due to the low accuracy and the high false positive rate of the existing clonal selection algorithms applied to intrusion detection, in this paper, we propose an improved clonal selection algorithm. The improved method detects the intrusion behavior by selecting the best individual overall and cloning them. Experimental results show that the improved algorithm achieves very good performance when applied to intrusion detection. And it is shown that the algorithm is better than BP neural network with its 99.5 % accuracy and 0.1 % false positive rate.






Similar content being viewed by others
References
Aickelin U, Bentley P, Cayzer S, Kim J, McLeod J (2003) Danger theory: The link between AIS and IDS? In: Timmis J, Bentley PJ, Hart E (eds) Artificial immune systems. Second International Conference, ICARIS 2003, Edinburgh, UK, September 1–3, 2003. Lecture Notes in Computer Science, vol 2787. Springer, Berlin, Heidelberg, pp 147–155
Aickelin U, Dasgupta D, Gu F (2014) Artificial immune systems. In: Burke EK, Kendall G (eds) Search methodologies. Introductory Tutorials in Optimization and Decision Support Techniques. Springer, US, pp 187–211
DasGupta D (1999) An overview of artificial immune systems and their applications. Springer, New York
Forrest S, Hofmeyr S, Somayaji A, Longstaff T (1996) A sense of self for unix processes. Proceedings of the IEEE Symposium on Security & Privacy 11(30):120–128
Gu Y, Shi Y, Wang J (2012) Efficient intrusion detection based on multiple neural network classifiers with improved genetic algorithm. J Softw 7(7):1641–1648
Gu B, Sheng VS, Tay KY, Romano W, Li S (2014) Incremental support vector learning for ordinal regression. IEEE Trans Neural Netw Learn Syst 26(7):1403-1416
Gu B, Sheng VS, Wang Z, Ho D, Osman S, Li S (2015) Incremental learning for ν-Support Vector Regression. Neural Netw 67:140–150
Kim J, Bentley PJ (2001) Towards an artificial immune system for network intrusion detection: An investigation of clonal selection with a negative selection operator. IEEE 1244–1252
Kim J, Bentley PJ (2002) Towards an artificial immune system for network intrusion detection: an investigation of dynamic clonal selection. IEEE 1015–1020
Li Y, Xia J, Zhang S, Yan J, Ai X, Dai K (2012) An efficient intrusion detection system based on support vector machines and gradually feature removal method. Expert Syst Appl 39(1):424–430
Liao H-J, Lin C-HR, Lin Y-C, Tung K-Y (2013) Intrusion detection system: A comprehensive review. J Netw Comput Appl 36(1):16–24
McClelland JL, Rumelhart DE, Group PR (1986) Parallel distributed processing. Explorations in the microstructure of cognition, vol 1. MIT Press, Cambridge
McHugh J (2000) Testing intrusion detection systems: a critique of the 1998 and 1999 DARPA intrusion detection system evaluations as performed by Lincoln Laboratory. ACM Trans Inf Syst Secur 3(4):262–294
Ou C-M (2012) Host-based intrusion detection systems adapted from agent-based artificial immune systems. Neurocomputing 88(7):78–86
Qing S-h, J-c J, Ma H-t, W-p W, X-f L (2004) Research on intrusion detection techniques: a survey. Journal-China Institute of Communications 25(7):19–29
Schmidhuber J (2015) Deep learning in neural networks: An overview. Neural Netw 61:85–117
Ulutas BH, Kulturel-Konak S (2011) A review of clonal selection algorithm and its applications. Artif Intell Rev 36(2):117–138
Yin C (2014) Towards Accurate Node-Based Detection of P2P Botnets. Sci World J 2014:425491
Yin C, Zou M, Iko D, Wang J (2013) Botnet detection based on correlation of malicious behaviors. International Journal of Hybrid Information Technology 6(6):291–300
Zhang F, Wang D (2013) An effective feature selection approach for network intrusion detection. IEEE 307–311
Zhang B, Zhang S, Lu G (2013) Evaluation model research of 100 meters sprint exercise capacity based on fuzzy neural network. J Chem Pharm Res 5(9):256
Acknowledgments
Foundation item: This work was funded by the National Natural Science Foundation of China (No.61373134). It was also supported by the Priority Academic Program Development of Jiangsu Higer Education Institutions(PAPD), Jiangsu Key Laboratory of Meteorological Observation and Information Processing (No.KDXS1105) and Jiangsu Collaborative Innovation Center on Atmospheric Environment and Equipment Technology(CICAEET).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Yin, C., Ma, L. & Feng, L. Towards accurate intrusion detection based on improved clonal selection algorithm. Multimed Tools Appl 76, 19397–19410 (2017). https://doi.org/10.1007/s11042-015-3117-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-3117-0