Abstract
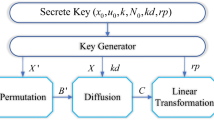
Recently, a color image encryption scheme based on skew tent map and hyper chaotic system of 6th-order CNN was proposed. It consists of two phases including one-time confusion and many times diffusion, which are controlled by skew tent map and hyper chaotic system of 6th-order CNN, respectively. It was claimed that the scheme can resist common attacks. However, this scheme is found to be insecure against chosen-plaintext attack. In this paper, we analyze the security weakness of the scheme. Although many keys were utilized, they keep fixed so that the corresponding chaotic keystreams are also consistent when encrypting different color images. All the keystreams used for each encryption can be wholly revealed through the derivation. In spite of many times of iterations in the diffusion phase, cryptanalytic results show that it is the same as only once. Experiment also verifies the proposed assertion.

Similar content being viewed by others
References
Benrhouma O, Hermassi H, Belghith S (2013) Security analysis and improvement of a partial encryption scheme. Multimed Tools Appl. doi:10.1007/s11042-013-1790-4
Chen J, Zhu Z, Fu C, Zhang L, Zhang Y (2014) An image encryption scheme using nonlinear inter-pixel computing and swapping based permutation approach. Commun Nonlinear Sci Numer Simul. doi:10.1016/j.cnsns.2014.11.021
Chen J, Zhu Z, Fu C, Zhang L, Zhang Y (2014) Cryptanalysis and improvement of an optical image encryption scheme using a chaotic Baker map and double random phase encoding. J Opt 16:125403
Hermassi H, Belazi A, Rhouma R, Belghith SM (2014) Security analysis of an image encryption algorithm based on a DNA addition combining with chaotic maps. Multimed Tools Appl 72(3):2211–2224
Kadir A, Hamdulla A, Guo WQ (2014) Color image encryption using skew tent map and hyper chaotic system of 6th-order CNN. Optik 125:1671–1675
Kong DZ, Shen XJ (2014) Multiple-image encryption based on optical wavelet transform and multichannel fractional Fourier transform. Opt Laser Technol 57:343–349
Li SJ, Li CQ, Chen GR, Bourbakis NG, Lo KT (2008) A general quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Signal Process Image Commun 23:212–223
Li CQ, Lo KT (2011) Optimal quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Signal Process 91:949–54
Liu H, Liu YB (2014) Cryptanalyzing an image encryption scheme based on hybrid chaotic system and cyclic elliptic curve. Opt Laser Technol 56:15–9
Liu H, Liu YB (2014) Security assessment on block-Cat-map based permutation applied to image encryption scheme. Opt Laser Technol 56:313–316
Liu HJ, Wang XY, Kadir A (2013) Color image encryption using Choquet fuzzy integral and hyper chaotic system. Optik 124:3527–3533
Norouzi B, Mirzakuchaki S, Seyedzadeh SM, Mosavi MR (2014) A simple, sensitive and secure image encryption algorithm based on hyper-chaotic system with only one round diffusion process. Multimed Tools Appl 71(3):1469–1497
Norouzi B, Seyedzadeh SM, Mirzakuchaki S, Mosavi MR (2013) A novel image encryption based on row-column, masking and main diffusion processes with hyper chaos. Multimed Tools Appl. doi:10.1007/s11042-013-1699-y
Parvin Z, Seyedarabi H, Shamsi M (2014) A new secure and sensitive image encryption scheme based on new substitution with chaotic function. Multimed Tools Appl. doi:10.1007/s11042-014-2115-y
Wen WY, Zhang Y, Fang ZJ, Chen J (2015) Infrared target-based selective encryption by chaotic maps. Opt Commun 241:131–139
You SP, Wu L, Cai BX (2013) Image double encryption based on iteration Fourier and chaos system. Optik 124:4197–4200
Zhang LY, Hu X, Liu Y, Wong KW, Gan J (2014) A chaotic image encryption scheme owning temp-value feedback. Commun Nonlinear Sci Numer Simul 19(10):3653–3659
Zhang L, Li C, Wong KW, Shu S, Chen G (2012) Cryptanalyzing a chaos-based image encryption algorithm using alternate structure. J Syst Softw 85(9):2077–2085
Zhang YS, Wen WY, Su MT, Li M (2014) Cryptanalyzing a novel image fusion encryption algorithm based on DNA sequence operation and hyper-chaotic system. Optik 125:1562–1564
Zhang Y, Xiao D (2013) Double optical image encryption using discrete Chirikov standard map and chaos-based fractional random transform. Opt Laser Eng 51(4):472–480
Zhang YS, Xiao D (2013) Cryptanalysis of S-box-only chaotic image ciphers against chosen plaintext attack. Nonlinear Dyn 72:751–756
Zhang YS, Xiao D (2014) Self-adaptive permutation and combined global diffusion for chaotic color image encryption. AEU-Int J Electron Commun 68(4):361–368
Zhang Y, Xiao D (2014) An image encryption scheme based on rotation matrix bit-level permutation and block diffusion. Commun Nonlinear Sci Numer Simul 19(1):74–82
Zhang YS, Xiao D, Shu YL, Li J (2013) A novel image encryption scheme based on a linear hyperbolic chaotic system of partial differential equations. Signal Process Image Commun 28:292–300
Zhang YS, Xiao D, Wen WY, Li M (2014) Cryptanalyzing a novel image cipher based on mixed transformed logistic maps. Multimed Tools Appl 73(3):1885–1896
Zhang YS, Xiao D, Wen WY, Liu H (2013) Vulnerability to chosen-plaintext attack of a general optical encryption model with the architecture of scrambling-then-double random phase encoding. Opt Lett 38:4506–4509
Zhang YS, Xiao D, Wen WY, Tian Y (2013) Edge-based lightweight image encryption using chaos-based reversible hidden transform and multiple-order discrete fractional cosine transform. Opt Laser Technol 54:1–6
Zhang Y, Xiao D, Wen W, Wong KW (2014) On the security of symmetric ciphers based on DNA coding. Inf Sci 289:254–261
Zheng YF, Jin JX (2014) A novel image encryption scheme based on Hénon map and compound spatiotemporal chaos. Multimed Tools Appl. doi:10.1007/s11042-014-2024-0
Acknowledgments
This work was supported by the National Natural Science Foundation of China (Grant nos. 61462032 and 61461021), the Natural Science Foundation of Jiangxi Province (Grant no. 20142BAB217012).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wen, W. Security analysis of a color image encryption scheme based on skew tent map and hyper chaotic system of 6th-order CNN against chosen-plaintext attack. Multimed Tools Appl 75, 3553–3560 (2016). https://doi.org/10.1007/s11042-015-2464-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-2464-1