Abstract
Load balancers enable efficient use of network resources by distributing traffic fairly across them. In software-defined networking (SDN), load balancing is most often realized by a controller application that solicits traffic load reports from network switches and enforces load balancing decisions through flow rules. This separation between the control and data planes in SDNs creates an opportunity for an adversary at a compromised switch to misreport traffic loads to influence load balancing. In this paper, we evaluate the ability of such an adversary to control the volume of traffic flowing through a compromised switch by misreporting traffic loads. We take a probabilistic approach to model the attack and develop algorithms for misreporting that allow an adversary to tune attack parameters toward specific adversarial goals. We validate the algorithms with a virtual network testbed, finding that through misreporting the adversary can control traffic flow to a high degree by drawing a target amount of load (e.g., + 200%) to within a 2% to 10% error of that target. This is yet another example of how depending on untrustworthy reporting in making control decisions can lead to fundamental security failures.








Similar content being viewed by others
Notes
We leave to future work analyzing more specialized variants of these algorithms.
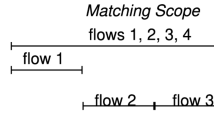
Note that switches may have multiple pool members (ports), but here we just consider a single pool member per switch and use switch and pool member interchangeably.
References
Project floodlight (2011) http://www.projectfloodlight.org/floodlight/. [Online; accessed 19-October-2018]
Opendaylight project (2013) https://www.opendaylight.org/. [Online; accessed 19-October-2018]
Aslam S, Shah MA (2015) Load balancing algorithms in cloud computing: a survey of modern techniques. In: 2015 National Software Engineering Conference (NSEC). IEEE, Rawalpindi, Pakistan, pp 30–35
Handigol N, Seetharaman S, Flajslik M, McKeown N, Johari R (2009) Plug-n-serve: Load-balancing web traffic using openflow. ACM Sigcomm Demo 4(5):6
Li J, Chang X, Ren Y, Zhang Z, Wang G (2014) An effective path load balancing mechanism based on SDN. In: 2014 IEEE 13th International Conference on Trust, Security and Privacy in Computing and Communications. IEEE, Beijing, China, pp 527–533
Mesbahi M, Rahmani AM (2016) Load balancing in cloud computing: a state of the art survey. Int J Modern Educ Comput Sci 8(3):64
Qilin M, Weikang S (2015) A load balancing method based on SDN. In: 2015 Seventh International Conference on Measuring Technology and Mechatronics Automation. IEEE, Nanchang, China, pp 18–21
Zhang J, Yu FR, Wang S, Huang T, Liu Z, Liu Y (2018) Load balancing in data center networks: A survey. IEEE Commun Surv Tutorials 20(3):2324–2352
Guo Z, Su M, Xu Y, Duan Z, Wang L, Hui S, Chao HJ (2014) Improving the performance of load balancing in software-defined networks through load variance-based synchronization. Comput Netw 68:95–109
Neghabi AA, Jafari Navimipour N, Hosseinzadeh M, Rezaee A (2018) Load balancing mechanisms in the software defined networks: A systematic and comprehensive review of the literature. IEEE Access 6:14159–14178. https://doi.org/10.1109/ACCESS.2018.2805842
Benson T, Akella A, Maltz DA (2010) Network traffic characteristics of data centers in the wild. In: Proceedings of the 10th ACM SIGCOMM conference on Internet measurement. ACM, New York, NY, pp 267–280
Rao A, Legout A, Lim Ys, Towsley D, Barakat C, Dabbous W (2011) Network characteristics of video streaming traffic. In: Proceedings of the Seventh COnference on emerging Networking EXperiments and Technologies. ACM, New York, NY, pp 1–12
Hong S, Xu L, Wang H, Gu G (2015) Poisoning network visibility in software-defined networks: New attacks and countermeasures. NDSS 15:8–11
Khan S, Gani A, Wahab AWA, Guizani M, Khan MK (2016) Topology discovery in software defined networks: Threats, taxonomy, and state-of-the-art. IEEE Commun Surv Tutorials 19(1):303–324
Yoon C, Lee S, Kang H, Park T, Shin S, Yegneswaran V, Porras P, Gu G (2017) Flow wars: Systemizing the attack surface and defenses in software-defined networks. IEEE/ACM Trans Netw (TON) 25(6):3514–3530
Kang N, Ghobadi M, Reumann J, Shraer A, Rexford J (2014) Niagara: scalable load balancing on commodity switches. Tech Rep, Technical Report (TR-973–14), Princeton
Wang R, Butnariu D, Rexford J et al (2011) Openflow based server load balancing gone wild. Hot-ICE 11:12–12
Mahmood A, Rashid I (2011) Comparison of load balancing algorithms for clustered web servers. In: ICIMU 2011: proceedings of the 5th international Conference on Information Technology & Multimedia. IEEE, Kuala Lumpur, Malaysia, pp 1–6
Zhou Y, Zhu M, Xiao L, Ruan L, Duan W, Li D, Liu R, Zhu M (2014) A load balancing strategy of SDN controller based on distributed decision. In: 2014 IEEE 13th International Conference on Trust, Security and Privacy in Computing and Communications. IEEE, Beijing, China, pp 851–856
Arau´jo JT, Saino L, Buytenhek L, Landa R (2018) Balancing on the edge: Transport affinity without network state. In: 15th USENIX Symposium on Networked Systems Design and Implementation (NSDI 18), pp. 111–124
The netfilter.org project (1998). URL https://www.netfilter.org/
Eisenbud DE, Yi C, Contavalli C, Smith C, Kononov R, Mann-Hielscher E, Cilingiroglu A, Cheyney B, Shang W, Hosein JD (2016) Maglev: A fast and reliable software network load balancer. In: 13th USENIX Symposium on Networked Systems Design and Implementation ({NSDI} 16), pp. 523–535
Patel P, Bansal D, Yuan L, Murthy A, Greenberg A, Maltz DA, Kern R, Kumar H, Zikos M, Wu H et al (2013) Ananta: Cloud scale load balancing. ACM SIGCOMM Comput Commun Rev 43(4):207–218
Openflow switch specification (2015) https://www.opennetworking.org/software-defined-standards/specifications/. [Online; accessed 19-October- 2018]
Raghavan B, Vishwanath K, Ramabhadran S, Yocum K, Snoeren AC (2007) Cloud control with distributed rate limiting. In: ACM SIGCOMM Computer Communication Review, vol. 37. ACM, New York, NY, pp 337–348
Feghhi S, Leith DJ (2016) A web traffic analysis attack using only timing information. IEEE Trans Inf Forensics Secur 11(8):1747–1759
Aslan M, Matrawy A (2016) On the impact of network state collection on the performance of sdn applications. IEEE Commun Lett 20(1):5–8
Arbettu RK, Khondoker R, Bayarou K, Weber F (2016) Security analysis of opendaylight, onos, rosemary and ryu sdn controllers. In: 2016 17th International Telecommunications Network Strategy and Planning Symposium (Networks). IEEE, Montreal, QC, pp 37–44. https://doi.org/10.1109/NETWKS.2016.7751150
Benzekki K, El Fergougui A, Elbelrhiti Elalaoui A (2016) Software-defined networking (sdn): a survey. Secur Commun Netw 9(18):5803–5833
Dargahi T, Caponi A, Ambrosin M, Bianchi G, Conti M (2017) A survey on the security of stateful sdn data planes. IEEE Commun Surv Tutorials 19(3):1701–1725
Scott-Hayward S, O’Callaghan G, Sezer S (2013) SDN security: a survey. In: 2013 IEEE SDN For Future Networks and Services (SDN4FNS). IEEE, Trento, Italy, pp 1–7
Thimmaraju K, Schiff L, Schmid S (2017) Outsmarting network security with sdn teleportation. In: 2017 IEEE European Symposium on Security and Privacy (EuroS&P). IEEE, Paris, France, pp 563–578
Pfaff B, Pettit J, Koponen T, Jackson E, Zhou A, Rajahalme J, Gross J, Wang A, Stringer J, Shelar P et al (2015) The design and implementation of open vSwitch. In: 12th USENIX Symposium on Networked Systems Design and Implementation (NSDI 15). USENIX Association, Oakland, CA, pp 117–130
Thimmaraju K, Shastry B, Fiebig T, Hetzelt F, Seifert JP, Feldmann A, Schmid S (2018) Taking control of sdn-based cloud systems via the data plane. In: Proceedings of the Symposium on SDN Research. ACM, New York, NY, pp 1–15
Chica JCC, Imbachi JC, Vega JFB (2020) Security in sdn: A comprehensive survey. J Netw Comput Appl 159:102595
Benson T, Anand A, Akella A, Zhang M (2009) Understanding data center traffic characteristics. In: Proceedings of the 1st ACM workshop on Research on enterprise networking, pp. 65–72. ACM
Burke Q, McDaniel P, Porta TL, Yu M, He T (2020) Misreporting attacks in software-defined networking. In: EAI SecureComm 2020 – 16th EAI International Conference on Security and Privacy in Communication Networks. EAI, pp 1519–1528
Achleitner S, La Porta T, Jaeger T, McDaniel P (2017) Adversarial network forensics in software defined networking. In: Proceedings of the Symposium on SDN Research, SOSR ’17. ACM, New York, NY, USA, pp 8–20. https://doi.org/10.1145/3050220.3050223
Kampanakis P, Perros H, Beyene T (2014) SDN-based solutions for moving target defense network protection. In: Proceeding of IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks 2014. IEEE, Sydney, NSW, pp 1–6
De Oliveira RLS, Schweitzer CM, Shinoda AA, Prete LR (2014) Using mininet for emulation and prototyping software-defined networks. In: 2014 IEEE Colombian Conference on Communications and Computing (COLCOM). IEEE, Bogota, Colombia, pp 1–6
Qian H, Medhi D (2011) Server operational cost optimization for cloud computing service providers over a time horizon. In: Hot-ICE. USENIX Association, Boston, MA
Curtis AR, Mogul JC, Tourrilhes J, Yalagandula P, Sharma P, Banerjee S (2011) Devoflow: scaling flow management for high-performance networks. In: ACM SIGCOMM Computer Communication Review, vol 41. ACM, New York, NY, pp 254–265
Greenberg A, Hamilton JR, Jain N, Kandula S, Kim C, Lahiri P, Maltz DA, Patel P, Sengupta S (2009) Vl2: a scalable and flexible data center network. In: ACM SIGCOMM computer communication review, vol 39. ACM, New York, NY, pp 51–62
Chandrasekaran SS (2017) Understanding traffic characteristics in a server to server data center network. Thesis, Rochester Institute of Technology
Aweya J, Ouellette M, Montuno DY, Doray B, Felske K (2002) An adaptive load balancing scheme for web servers. Int J Network Manage 12(1):3–39
Ahmed M, Mahmood AN, Hu J (2016) A survey of network anomaly detection techniques. J Netw Comput Appl 60:19–31
Caberera J, Ravichandran B, Mehra RK (2000) Statistical traffic modeling for network intrusion detection. In: Proceedings 8th International Symposium on Modeling, Analysis and Simulation of Computer and Telecommunication Systems (Cat. No. PR00728). IEEE, San Francisco, CA, pp 466–473
Dhawan M, Poddar R, Mahajan K, Mann V (2015) Sphinx: detecting security attacks in software-defined networks. Ndss 15:8–11
Kamisin´ski A, Fung C (2015) Flowmon: detecting malicious switches in software-defined networks. In: Proceedings of the 2015 Workshop on Automated Decision Making for Active Cyber Defense. ACM, New York, NY, pp 39–45
Zhang Y (2013) An adaptive flow counting method for anomaly detection in SDN. In: Proceedings of the ninth ACM conference on Emerging networking experiments and technologies. ACM, New York, NY, pp 25–30
Dridi L, Zhani MF (2016) SDN-guard: Dos attacks mitigation in sdn networks. In: 2016 5th IEEE International Conference on Cloud Networking (Cloudnet). IEEE, Pisa, Italy, pp 212–217
Achleitner S, Burke Q, McDaniel P, Jaeger T, Porta TL, Krishnamurthy S (2019) MLSNet: A Policy Complying Multilevel Security Framework for Software Defined Networking. Tech. Rep. INSR-500-TR-0500–2019, Institute of Networking and Security Research, Department of Computer Science and Engineering, Pennsylvania State University, University Park, PA, USA. http://patrickmcdaniel.org/papers-ct.html
Yu M, He T, McDaniel P, Burke QK (2020) Flow table security in SDN: adversarial reconnaissance and intelligent attacks. In: IEEE INFOCOM 2020-IEEE Conference on Computer Communications. IEEE, Toronto, ON, pp 1519–1528
Kang MS, Gligor VD, Sekar V et al (2016) Spiffy: Inducing cost-detectability tradeoffs for persistent link-flooding attacks. NDSS 1:53–55
Yu H, Shen Z, Miao C, Leung C, Niyato D (2010) A survey of trust and reputation management systems in wireless communications. Proc IEEE 98(10):1755–1772
Tan S, Li X, Dong Q (2015) Trust based routing mechanism for securing oslr-based manet. Ad Hoc Netw 30:84–98
Zhang J (2011) A survey on trust management for VANETs. In: 2011 IEEE International Conference on Advanced Information Networking and Applications. IEEE, Biopolis, Singapore, pp 105–112
Lopez J, Roman R, Agudo I, Fernandez-Gago C (2010) Trust management systems for wireless sensor networks: Best practices. Comput Commun 33(9):1086–1093
Buchegger S, Le Boudec JY (2002) Performance analysis of the confidant protocol. In: Proceedings of the 3rd ACM international symposium on Mobile ad hoc networking & computing. ACM, New York, NY, pp 226–236
Aliyu AL, Bull P, Abdallah A (2017) A trust management framework for network applications within an SDN environment. In: 2017 31st International Conference on Advanced Information Networking and Applications Workshops (WAINA). IEEE, Taipei, Taiwan, pp 93–98
Betg´e-Brezetz S, Kamga GB, Tazi M (2015) Trust support for SDN controllers and virtualized network applications. In: Proceedings of the 2015 1st IEEE Conference on Network Softwarization (NetSoft). IEEE, London, UK, pp 1–5
Funding
This research was sponsored by the U.S. Army Combat Capabilities Development Command Army Research Laboratory and was accomplished under Cooperative Agreement Number W911NF-13–2-0045 (ARL Cyber Security CRA). The views and conclusions contained in this document are those of the authors and should not be interpreted as representing the official policies, either expressed or implied, of the Combat Capabilities Development Command Army Research Laboratory or the U.S. Government. The U.S. Government is authorized to reproduce and distribute reprints for Government purposes notwithstanding any copyright notation here on. This work was also supported in part by the National Science Foundation under award CNS-1946022.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Burke, Q., McDaniel, P., La Porta, T. et al. Misreporting Attacks Against Load Balancers in Software-Defined Networking. Mobile Netw Appl (2024). https://doi.org/10.1007/s11036-023-02156-0
Accepted:
Published:
DOI: https://doi.org/10.1007/s11036-023-02156-0