Abstract
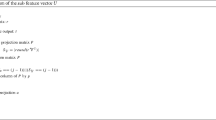
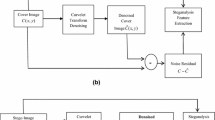
As the number of methods for implementing steganography (the hiding of data within a cover) increases, steganalysis, which can detect the presence of such hidden data, is also accompanied by an increase. To improve the accuracy of detection, we propose a new algorithm for processing feature that makes two optimizations into a random vector functional link (RVFL) network. The first optimization locates the processing phase of RVFL, where we model the eigenspectrum by the eigenvalue distribution of the scatter matrix. This eigenspectrum is used to generate the transpose matrix and obtain final features after feature reduction. The second optimization is the use of the random subspace Fisher linear discriminant (FLD) instead of random weights in RVFL. The weights between the input and enhancement nodes more accurately represent the relative importance of the features. The experiments compare the performance of other classifiers with the proposed method using five high-dimensional features. It is shown that the proposed method outperforms other classifiers in these steganalysis methods.











Similar content being viewed by others
References
Zhang X, Wang S (2006) Efficient steganographic embedding by exploiting modification direction. IEEE Commun Lett 10(11):781–783
Holub V, Fridrich J (2012) Designing steganographic distortion using directional filters. In: IEEE International workshop on information forensics and security, pp 234–239
Holub V, Fridrich J, Denemark T (2014) Universal distortion function for steganography in an arbitrary domain. EURASIP J Inf Secur 1:1–13
Guo L, Ni J, Su W, Tang C, Shi Y (2015) Using statistical image model for JPEG steganography: uniform embedding revisited. IEEE Trans Inf Forens Secur 10(12):2669–2680
Qin C, Chen X, Ye D, Wang J, Sun X (2016) A novel image hashing scheme with perceptual robustness using block truncation coding. Inf Sci 361–362:84–99
Luo XY, Song XF, Li XL, Zhang WM, Lu JC, Yang CF, Liu FL (2016) Steganalysis of HUGO steganography based on parameter recognition of syndrome-trellis-codes. Multimed Tools Appl 75(21):13557–13583
Dumitrescu S, Wu X, Wang Z (2003) Detection of LSB steganography via sample pair analysis. IEEE Trans Signal Process 51(7):1995–2007
Fridrich J, Kodovský J (2012) Rich models for steganalysis of digital images. IEEE Trans Inf Forens Secur 7(3):68–82
Kodovský J, Fridrich J (2012) Steganalysis of JPEG images using rich models. In: Proceedings of IS&T/SPIE electronic imaging, international society for optics and photonics, pp 83030A
Holub V, Kodovský J (2015) Low-complexity features for JPEG steganalysis using undecimated DCT. IEEE Trans Inf Forens Secur 10(2):219–228
Song X, Liu F, Yang C, Luo X, Zhang Y (2015) Steganalysis of adaptive JPEG steganography using 2D Gabor filters. In: Proceedings of the 3rd ACM workshop on information hiding and multimedia security, pp 15–23
Cortes C, Vapnik V (1995) Support vector networks. Mach Learn 20:273–297
Kodovský J, Fridrich J, Holub V (2012) Ensemble classifiers for steganalysis of digital media. IEEE Trans Inf Forens Secur 7(2):432–444
Schmidt WF, Kraaijveld MA, Duin RP (1992) Feedforward neural networks with random weights. In: Proceedings of 11th IAPR international conference on pattern recognition, conference B: pattern recognition methodology and systems, pp 1–4
Chen YF, Chen FL, Wu T, Hu WT, Xu XH (2018) A deep learning model for secure cyber-physical transportation systems. In: Proceedings of IEEE conference on computer communications (INFOCOM 2018): POSTER, pp 1–2
Pao YH, Park GH, Sobajic DJ (1994) Learning and generalization characteristics of the random vector functional-link net. Neurocomputing 6(2):163–180
Chen YF, Shu L, Wang L (2017) Traffic flow prediction with big data: a deep learning based time series model. In: Proceedings of IEEE conference on computer communications (INFOCOM 2017), pp 1010–1011
Zhang L, Suganthan PN (2016) A comprehensive evaluation of random vector functional link networks. Inform Sci 367:1094–1105
Ren Y, Suganthan PN, Srikanth N, Amaratunga G (2016) Random vector functional link network for short-term electricity load demand forecasting. Inform Sci 367:1078–1093
Park GH, Pao YH (2000) Unconstrained word-based approach for off-line script recognition using density-based random-vector functional-link net. Neurocomputing 31(1):45–65
Wold S, Esbensen K, Geladi P (1987) Principal component analysis. Chemometrics Intell Lab Syst 2 (1–3):37–52
Jiang X, Mandal B, Kot A (2008) Eigenfeature regularization and extraction in face recognition. IEEE Trans Pattern Anal Mach Intell 30(3):383–394
Serre D (2002) Matrices: theory and applications. Springer, New York
Image data available at http://www.agents.cz/boss/BOSSFinal/index.php?mode=VIEW&tmpl=materials
Acknowledgements
This work was supported by the National Natural Science Foundation of China under Grants (61702149, U1536109, U1709220 and 61373151).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Fan, L., Sun, W. & Feng, G. Image Steganalysis via Random Subspace Fisher Linear Discriminant Vector Functional Link Network and Feature Mapping. Mobile Netw Appl 24, 1269–1278 (2019). https://doi.org/10.1007/s11036-018-1167-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-018-1167-z