Abstract
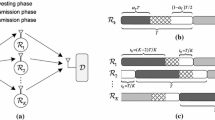
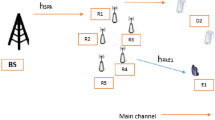
In this paper, an energy harvesting relay network over Nakagami-m fading is investigated. In the considered system, the power beacon can provide wireless energy for the source and relays which deploy time-switching-based radio frequency energy harvesting technique. Two relay selection schemes, namely partial relay selection and optimal relay selection, are proposed in order to enhance the system performance. In the former, the source only has the channel state information of the first hop, while in the latter it has the full knowledge of the channel state information. The eavesdropper is able to wiretap to the signal transmitted from the source and the relays. The exact closed-form expressions of secrecy outage probability are derived. The results show that optimal relay selection performs better than partial relay selection. With increasing number of relays, the considered system shows better performance. In addition, the energy harvesting duration has a significant effect on the secrecy outage probability.




Similar content being viewed by others

References
Yuen C, Elkashlan M, Qian Y, Duong TQ, Shu L, Schmidt F (2015) Energy harvesting communications: part 1 [Guest Editorial]. IEEE Commun Mag 53(6):54–55
Yuen C, Elkashlan M, Qian Y, Duong TQ, Shu L, Schmidt F (2015) Energy harvesting communications: part 2 [Guest Editorial]. IEEE Commun Mag 53(6):54–55
Yuen C, Elkashlan M, Qian Y, Duong TQ, Shu L, Schmidt F (2015) Energy harvesting communications: part 3 [Guest Editorial]. IEEE Commun Mag 53(6):54–55
Zhou X, Zhang R, Ho CK (2013) Wireless information and power transfer: architecture design and rate-energy tradeoff. IEEE Trans Commun 61(11):4754–4767
Nasir AA, Zhou X, Durrani S, Kennedy RA (2013) Relaying protocols for wireless energy harvesting and information processing. IEEE Trans Wireless Commun 12(7):3622–3636
Nasir AA, Zhou X, Durrani S, Kennedy RA (2015) Wireless-powered relays in cooperative communications: time-switching relaying protocols and throughput analysis. IEEE Trans Commun 63(5):1607–1622
Michalopoulos DS, Suraweera HA, Schober R (2015) Relay selection for simultaneous information transmission and wireless energy transfer: a tradeoff perspective. IEEE J Sel Areas Commun 33(8):1–1
Mohammadi M, Chalise BK, Suraweera HA, Zhong C, Zheng G, Krikidis I (2016) Throughput analysis and optimization of wireless-powered multiple antenna full-duplex relay systems. IEEE Trans Commun 64(4):1769–1785
Zhong C, Zheng G, Zhang Z, Karagiannidis G (2015) Optimum wirelessly powered relaying. IEEE Signal Process Lett 22(10):1–1
Nguyen V-D, Duong TQ, Tuan HD, Shin O-S, Poor HV (2017) Spectral and energy efficiencies in full-duplex wireless information and power transfer. IEEE Trans Commun 65(5):2220–2233
Rankov B, Wittneben A (2007) Spectral efficient protocols for half-duplex fading relay channels. IEEE J Sel Areas Commun 25(2):379–389
Bao VNQ, Duong TQ, da Costa DB, Alexandropoulos GC, Nallanathan A (2013) Cognitive amplify-and-forward relaying with best relay selection in non-identical Rayleigh fading. IEEE Commun Lett 17(3):475–478
Chen G, Tian Z, Gong Y, Chambers J (2014) Decode-and-forward buffer-aided relay selection in cognitive relay networks. IEEE Trans Veh Technol 63(9):4723–4728
Hoang TM, Duong TQ, Vo NS, Kundu C (2017) Physical layer security in cooperative energy harvesting networks with a friendly jammer. IEEE Wireless Commun Lett PP(99):1–1
Fan L, Lei X, Yang N, Duong TQ, Karagiannidis GK (2017) Secrecy cooperative networks with outdated relay selection over correlated fading channels. IEEE Trans Veh Technol PP(99):1–1
Yang M, Guo D, Huang Y, Duong TQ, Zhang B (2016) Secure multiuser scheduling in downlink dual-hop regenerative relay networks over Nakagami- m fading channels. IEEE Trans Wireless Commun 15(12):8009–8024
Fan L, Lei X, Yang N, Duong TQ, Karagiannidis GK (2016) Secure multiple amplify-and-forward relaying with cochannel interference. IEEE J Sel Topics Signal Process 10(8):1494–1505
Duong TQ, Hoang TM, Kundu C, Elkashlan M, Nallanathan A (2016) Optimal power allocation for multiuser secure communication in cooperative relaying networks. IEEE Wireless Commun Lett 5(5):516–519
Huang Y, Wang J, Zhong C, Duong TQ, Karagiannidis GK (2016) Secure transmission in cooperative relaying networks with multiple antennas. IEEE Trans Wireless Commun 15(10):6843–6856
Nguyen NP, Duong TQ, Ngo HQ, Hadzi-Velkov Z, Shu L (2016) Secure 5G wireless communications: a joint relay selection and wireless power transfer approach. IEEE Access 4:3349–3359
Fan L, Yang N, Duong TQ, Elkashlan M, Karagiannidis GK (2016) Exploiting direct links for physical layer security in multiuser multirelay networks. IEEE Trans Wireless Commun 15(6):3856–3867
Hoang TM, Duong TQ, Suraweera HA, Tellambura C, Poor HV (2015) Cooperative beamforming and user selection for improving the security of relay-aided systems. IEEE Trans Wireless Commun 63(12):5039–5051
Rodriguez LJ, Tran NH, Duong TQ, Le-Ngoc T, Elkashlan M, Shetty S (2015) Physical layer security in wireless cooperative relay networks: atate of the art and beyond. IEEE Commun Mag 53(12):32–39
Wang L, Kim KJ, Duong TQ, Elkashlan M, Poor HV (2015) Security enhancement of cooperative single carrier systems. IEEE Trans Inf Forensics Secur 10(1):90–103
Fan L, Lei X, Duong TQ, Elkashlan M, Karagiannidis GK (2014) Secure multiuser communications in multiple amplify-and-forward relay networks. IEEE Trans Commun 62(9):3299–3310
Wang L, Elkashlan M, Huang J, Tran NH, Duong TQ (2014) Secure transmission with optimal power allocation in untrusted relay networks. IEEE Wireless Commun Lett 3(3):289–292
Ng DWK, Lo ES, Schober R (2014) Robust beamforming for secure communication in systems with wireless information and power transfer. IEEE Trans Wireless Commun 13(8):4599–4615
Liu W, Zhou X, Durrani S, Popovski P (2016) Secure communication with a wireless-powered friendly jammer. IEEE Trans Wireless Commun 15(1):401–415
Zhang J, Nguyen N-P, Zhang J, Garcia-Palacios E, Le NP (2016) Impact of primary networks on the performance of energy harvesting cognitive radio networks. IET Commun 10(18):2559–2566
Gradshteyn IS, Ryzhik IM (2007) Table of integrals, series, and products, 7th edn. Academic Press, San Diego
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix A: Proof of lemma 1
The SNR of first hop and second hop in PRS scheme can be written as
The CDF of γ 1P R S is expressed as

The CDF of γ 2P R S is expressed as

The SOP of the considered system in PRS scheme is formulated as follows
After performing some mathematical manipulations, Eq. 22 can be achieved with the help of [30, Eq. (3.471.9)].
Appendix B: Proof of lemma 2
In ORS scheme, the SNR of the first and second hop can be derived as
We denote that Y o = |h B S |2, and Z o = |h S E |2. The SOP of the considered system in the ORS scheme is calculated as follows
Where in the first hop

Where in the second hop
After performing some mathematical manipulations, Eq. 26 can be achieved with the help of [30, Eq. (3.471.9)].
Rights and permissions
About this article
Cite this article
Yin, C., Nguyen, NP., Garcia-Palacios, E. et al. Secure Energy Harvesting Communications with Relay Selection over Nakagami-m Fading Channels. Mobile Netw Appl 23, 1555–1562 (2018). https://doi.org/10.1007/s11036-017-0919-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-017-0919-5