Abstract
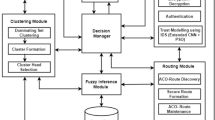
In Multimedia Sensor Networks (WMSNs) the devices are interconnected in the wireless manner that is able to ubiquitously retrieve multimedia content such as video and audio streams, still images, and scalar sensor data from environments. Many research works have been undertaken to enhance the quality of multimedia contents and energy consumption, but not security. Till, security problems are critical issue in WMSNs. Trust inference is one of the methods that solve security problems in wireless sensor networks (WSNs) and mobile ad hoc networks (MANET). In this paper, we propose an energy efficient trusted cluster (E2TC) based routing protocol for WMSNs for overcome multi-objective problems, which can eventually maximize the network lifetime. The proposed routing protocol consist of two algorithms, first the multi-dimension differential evolution based trust (MDET) inference model used to compute trust value for each node in the network, then the energy efficient cluster formation is performed using load balance enhanced chemical reaction optimization (LBCRO) algorithm. The routing path between the source nodes to destination nodes framed by computed trust values. The result obtained through Network simulator tool and shows that the proposed routing protocol performs better than existing protocols in terms of energy consumption, QoS metrics, and network lifetime.








Similar content being viewed by others
References
Czarlinska, A., Kundur, D.: Reliable event-detection in wireless visual sensor networks through scalar collaboration and game-theoretic consideration. IEEE Trans. Multimed. 10(5), 675–690 (2008)
La, H.M., Sheng, W.: Distributed sensor fusion for scalar field mapping using mobile sensor networks. IEEE Trans. Cybern. 43(2), 766–778 (2013)
Akyildiz, I.F., Melodia, T., Chowdhury, K.R.: Wireless multimedia sensor networks: applications and testbeds. Proc. IEEE 96(10), 1588–1605 (2008)
Huang, H., Gong, T., Chen, P., Malekian, R., Chen, T.: Secure two-party distance computation protocol based on privacy homomorphism and scalar product in wireless sensor networks. Tsinghua Sci. Technol. 21(4), 385–396 (2016)
Tian, D., Georganas, N.D.: A coverage-preserving node scheduling scheme for large wireless sensor networks. In: Proceedings of the 1st ACM International Workshop on Wireless Sensor Networks and Applications—WSNA ‘02 (2002)
Megerian, S., Koushanfar, F., Qu, G., Veltri, G., Potkonjak, M.: Exposure in wireless sensor networks: theory and practical solutions. Wirel. Netw. 8(5), 443–454 (2002)
Chan, E., Han, S.: Energy efficient residual energy monitoring in wireless sensor networks. Int. J. Distrib. Sens. Netw. 5(6), 748–770 (2009)
Narula, P., Dhurandher, S.K., Misra, S., Woungang, I.: Security in mobile ad-hoc networks using soft encryption and trust-based multi-path routing. Comput. Commun. 31(4), 760–769 (2008)
Refaei, M.T., DaSilva, L.A., Eltoweissy, M., Nadeem, T.: Adaptation of reputation management systems to dynamic network conditions in ad hoc networks. IEEE Trans. Comput. 59(5), 707–719 (2010)
Li, X., Zhou, F., Du, J.: LDTS: a lightweight and dependable trust system for clustered wireless sensor networks. IEEE Trans. Inf. Forensics Secur. 8(6), 924–935 (2013)
Basilico, N., Gatti, N., Monga, M., Sicari, S.: Security games for node localization through verifiable multilateration. IEEE Trans. Dependable Secure Comput. 11(1), 72–85 (2014)
Kundur, D., Luh, W., Okorafor, U.N., Zourntos, T.: Security and privacy for distributed multimedia sensor networks. Proc. IEEE 96(1), 112–130 (2008)
Wang, H.: Communication-resource-aware adaptive watermarking for multimedia authentication in wireless multimedia sensor networks. J. Supercomput. 64(3), 883–897 (2010)
Newell, A., Akkaya, K.: Distributed collaborative camera actuation for redundant data elimination in wireless multimedia sensor networks. Ad Hoc Netw. 9(4), 514–527 (2011)
Zhang, Y., Li, X., Yang, J., Liu, Y., Xiong, N., Vasilakos, A.: A real-time dynamic key management for hierarchical wireless multimedia sensor network. Multimed. Tools Appl. 67(1), 97–117 (2012)
Xiang, T., Yu, C., Chen, F.: Secure MQ coder: an efficient way to protect JPEG 2000 images in wireless multimedia sensor networks. Signal Process. Image Commun. 29(9), 1015–1027 (2014)
Guerrero-Zapata, M., Zilan, R., Barceló-Ordinas, J.M., Bicakci, K., Tavli, B.: The future of security in wireless multimedia sensor networks. Telecommun. Syst. 45(1), 77–91 (2009)
Lin, Q., Wang, R., Ye, N., Wang, Z.: Energy efficient distributed steganography for secure communication in wireless multimedia sensor networks. J. Electron. 30(1), 9–16 (2013)
Sun, Y., Luo, H., Das, S.K.: A trust-based framework for fault-tolerant data aggregation in wireless multimedia sensor networks. IEEE Trans. Dependable Secure Comput. 9(6), 785–797 (2012)
Ghadi, M., Laouamer, L., Moulahi, T.: Securing data exchange in wireless multimedia sensor networks: perspectives and challenges. Multimed. Tools Appl. 75(6), 3425–3451 (2015)
Deebak, B.D.: Secure and efficient mutual adaptive user authentication scheme for heterogeneous wireless sensor networks using multimedia client–server systems. Wirel. Pers. Commun. 87(3), 1013–1035 (2015)
Sun, Y., Ma, H., Liu, L., Zheng, Y.E.: ASAR: an ant-based service-aware routing algorithm for multimedia sensor networks. Front. Electr. Electron. Eng. China 3(1), 25–33 (2008)
Li, Z.Y., Wang, R.C.: Load balancing-based hierarchical routing algorithm for wireless multimedia sensor networks. J. China Univ. Posts Telecommun. 17, 51–59 (2010)
Shu, L., Zhang, Y., Yang, L.T., Wang, Y., Hauswirth, M., Xiong, N.: TPGF: geographic routing in wireless multimedia sensor networks. Telecommun. Syst. 44(1–2), 79–95 (2009)
Cobo, L., Quintero, A., Pierre, S.: Ant-based routing for wireless multimedia sensor networks using multiple QoS metrics. Comput. Netw. 54(17), 2991–3010 (2010)
Lin, K., Chen, M.: Research on energy efficient fusion-driven routing in wireless multimedia sensor networks. EURASIP J. Wirel. Commun. Netw. 2011(1), 142 (2011)
Kim, J.M., Seo, H.S., Kwak, J.: Routing protocol for heterogeneous hierarchical wireless multimedia sensor networks. Wirel. Pers. Commun. 60(3), 559–569 (2011)
Kandris, D., Tsagkaropoulos, M., Politis, I., Tzes, A., Kotsopoulos, S.: Energy efficient and perceived QoS aware video routing over wireless multimedia sensor networks. Ad Hoc Netw. 9(4), 591–607 (2011)
Li, B.Y., Chuang, P.J.: Geographic energy-aware non-interfering multipath routing for multimedia transmission in wireless sensor networks. Inf. Sci. 249, 24–37 (2013)
Huang, H., Cao, X., Wang, R., Wen, Y.: A QoS-aware routing algorithm based on ant-cluster in wireless multimedia sensor networks. Sci. China Inf. Sci. 57(10), 1–16 (2014)
Shen, H., Bai, G., Tang, Z., Zhao, L.: QMOR: QoS-aware multi-sink opportunistic routing for wireless multimedia sensor networks. Wirel. Pers. Commun. 75(2), 1307–1330 (2013)
Magaia, N., Horta, N., Neves, R., Pereira, P.R., Correia, M.: A multi-objective routing algorithm for wireless multimedia sensor networks. Appl. Soft Comput. 30, 104–112 (2017)
Han, L., Sun, S., Joo, B., Jin, X., Han, S.: QoS-aware routing mechanism in OpenFlow-enabled wireless multimedia sensor networks. Int. J. Distrib. Sens. Netw. 12(7), 9378120 (2016)
Misra, S., Mali, G., Mondal, A.: Distributed topology management for wireless multimedia sensor networks: exploiting connectivity and cooperation. Int. J. Commun. Syst. 28(7), 1367–1386 (2014)
Mali, G., Misra, S.: TRAST: trust-based distributed topology management for wireless multimedia sensor networks. IEEE Trans. Comput. 65(6), 1978–1991 (2016)
Li, H., Zhang, L.: A discrete hybrid differential evolution algorithm for solving integer programming problems. Eng. Optim. 46(9), 1238–1268 (2013)
Shahid, N., Naqvi, I.H., Qaisar, S.B.: Characteristics and classification of outlier detection techniques for wireless sensor networks in harsh environments: a survey. Artif. Intell. Rev. 43(2), 193–228 (2012)
Bechikh, S., Chaabani, A., Said, L.B.: An efficient chemical reaction optimization algorithm for multi objective optimization. IEEE Trans. Cybern. 45(10), 2051–2064 (2015)
Heinzleman, W.R., Chandrakasan, A., Balakrishnan, H.: Energy efficient communication protocol for wireless micro sensor networks. In: Proceedings of the 33rd Hawaii International Conference on System Sciences, p. 10 (2000)
Wright, S., Nocedal, J.: Numerical Optimization vol. 35, no. (67–68), p. 7. Springer Science, Berlin (1999)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ranjith Kumar, A., Sivagami, A. Security Aware Multipath Routing Protocol for WMSNs for Minimizing Effect of Compromising Attacks. J Netw Syst Manage 27, 573–599 (2019). https://doi.org/10.1007/s10922-018-9477-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10922-018-9477-9