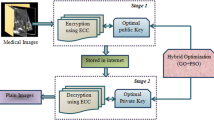
Abstract
Security is the most critical issue amid transmission of medical images because it contains sensitive information of patients. Medical image security is an essential method for secure the sensitive data when computerized images and their relevant patient data are transmitted across public networks. In this paper, the dual encryption procedure is utilized to encrypt the medical images. Initially Blowfish Encryption is considered and then signcryption algorithm is utilized to confirm the encryption model. After that, the Opposition based Flower Pollination (OFP) is utilized to upgrade the private and public keys. The performance of the proposed strategy is evaluated using performance measures such as Peak Signal to Noise Ratio (PSNR), entropy, Mean Square Error (MSE), and Correlation Coefficient (CC).




Similar content being viewed by others
References
Annaby, M. H., Rushdi, M. A., and Nehary, E. A., Color image encryption using random transforms, phase retrieval, chaotic maps, and diffusion. Opt. Lasers Eng. 103:9–23, 2018.
Abdel-Basset, M., Gunasekaran, M., Mohamed, M. et al., A novel method for solving the fully neutrosophic linear programming problems. Neural Comput & Applic. 1–11, 2018. https://doi.org/10.1007/s00521-018-3404-6.
Liao, X., Hahsmi, M. A., and Haider, R., An efficient mixed inter-intra pixels substitution at 2bits-level for image encryption technique using DNA and chaos. Optik 153:117–134, 2018.
Chen, J., Zhang, Y., Qi, L., Fu, C., and Xu, L., Exploiting chaos-based compressed sensing and cryptographic algorithm for image encryption and compression. Opt. Laser Technol. 99:238–248, 2018.
Xiong, Y., Quan, C., and Tay, C. J., Multiple image encryption scheme based on pixel exchange operation and vector decomposition. Opt. Lasers Eng. 101:113–121, 2018.
Abdel-Basset, M., Gunasekaran, M., Mohamed, M. and Chilamkurti, N., Three-way decisions based on neutrosophic sets and AHP-QFD framework for supplier selection problem. Future Generation Computer Systems. 89:19–30, 2018.
Ismail, S. M., Said, L. A., Radwan, A. G., Madian, A. H. and Abu-Elyazeed, M. F., Generalized double-humped logistic map-based medical image encryption. Journal of Advanced Research. 10:85–98, 2018.
Abdel-Basset, M., Manogaran, G., Fakhry, A.E. and El-Henawy, I., 2-Levels of clustering strategy to detect and locate copy-move forgery in digital images. Multimedia Tools and Applications. 1–19, 2018. https://doi.org/10.1007/s11042-018-6266-0.
Cao, W., Zhou, Y., Chen, C. P., and Xia, L., Medical image encryption using edge maps. Signal Process. 132:96–109, 2017.
Abdel-Nabi, H., Al-Haj, A., Medical imaging security using partial encryption and histogram shifting watermarking. In: Information Technology (ICIT), 2017 8th International Conference on (pp. 802–807). IEEE., 2017.
Shankar, K., and Eswaran, P., RGB based multiple share creation in visual cryptography with aid of elliptic curve cryptography. China Commun. 14(2):118–130, 2017.
Shankar, K., and Eswaran, P., An efficient image encryption technique based on optimized key generation in ECC using genetic algorithm. Artificial Intelligence and Evolutionary Computations in Engineering Systems. Springer, New Delhi. 705–714, 2016.
Puech, W., Image encryption and compression for medical image security. In: Image Processing Theory, Tools and Applications, 2008. IPTA 2008. First Workshops on (pp. 1–2). IEEE, 2008.
Abdmouleh, M. K., Khalfallah, A., and Bouhlel, M. S., A novel selective encryption scheme for medical images transmission based-on JPEG compression algorithm. Procedia Comput. Sci. 112:369–376, 2017.
Kester, Q. A., Nana, L., Pascu, A. C., Gire, S., Eghan, J. M., and Quaynor, N. N., A cryptographic technique for security of medical images in health information systems. Procedia Comput. Sci. 58:538–543, 2015.
Laiphrakpam, D. S., and Khumanthem, M. S., Medical image encryption based on improved ElGamal encryption technique. Optik 147:88–102, 2017.
Shankar, K., and Eswaran, P., Sharing a secret image with encapsulated shares in visual cryptography. Procedia Comput. Sci. 70:462–468, 2015.
Mahmood, A., Hamed, T., Obimbo, C., and Dony, R., Improving the security of the medical images. Int. J. Adv. Comput. Sci. Appl. 4(9):130–136, 2013.
Madhu, S., and Hussain, M. A., Securing medical images by image encryption usingthekey image. Int. J. Comput. Appl. 104(3):30–34, 2014.
Abdel-Basset, M., Manogaran, G., Rashad, H. and Zaied, A. N. H., A comprehensive review of quadratic assignment problem: variants, hybrids and applications. Journal of Ambient Intelligence and Humanized Computing. 1–24, 2018. https://doi.org/10.1007/s12652-018-0917-x.
Kester, Q. A., Nana, L., Pascu, A. C., Gire, S., Eghan, J. M., and Quaynor, N. N., A cryptographic technique for security of medical images in health information systems. Procedia Comput. Sci. 58:538–543, 2015.
Abdel-Basset, M., Manogaran, G., Gamal, A., Smarandache, F., A hybrid approach of neutrosophic sets and DEMATEL method for developing supplier selection criteria. Des. Autom. Embed. Syst.:1–22, 2018.
Kanso, A., and Ghebleh, M., An efficient and robust image encryption scheme for medical applications. Communications in Nonlinear Science and Numerical Simulation. 24:98–116, 2015.
Lima, J. B., Madeiro, F., and Sales, F. J. R., Encryption of medical images based on the cosine number transform. Signal Process. Image Commun. 35:1–8, 2015.
Mukhedkar, M., Powar, P., Gaikwad, P., Secure nonreal time image encryption algorithm development using cryptography & Steganography. In: India Conference (INDICON), 2015 Annual IEEE (pp. 1–6). IEEE, 2015.
Daniel, R. M., Rajsingh, E. B. and Silas, S. A., Forward secure signcryption scheme with ciphertext authentication for e-payment systems using conic curve cryptography. Journal of King Saud University-Computer and Information Sciences. 2018. https://doi.org/10.1016/j.jksuci.2018.02.004
Nabil, E., A modified flower pollination algorithm for global optimization. Expert Syst. Appl. 57:192–203, 2016.
Abdel-Basset, M., Manogaran, G. and Mohamed, M., Internet of Things (IoT) and its impact on supply chain: A framework for building smart, secure and efficient systems. Future Generation Computer Systems. 86:614–628, 2018.
Shankar, K., and Lakshmanaprabu, S. K., Optimal key based homomorphic encryption for color image security aid of ant lion optimization algorithm. International Journal of Engineering & Technology 7(9):22–27, 2018.
Janakiraman, S., Thenmozhi, K., Rayappan, J. B. B., and Amirtharajan, R., Lightweight chaotic image encryption algorithm for the real-time embedded system: Implementation and analysis on the32-bit microcontroller. Microprocess. Microsyst. 56:1–12, 2018.
Shankar, K., and Eswaran, P., RGB-based secure share creation in visual cryptography using optimal elliptic curve cryptography technique. J. Circuits Syst. Comp. 25(11):1650138, 2016.
Abdel-Basset, M., Manogaran, G., El-Shahat, D., and Mirjalili, S., A hybrid whale optimization algorithm based on local search strategy for the permutation flow shop scheduling problem. Futur. Gener. Comput. Syst. 85:129–145, 2018.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All the authors declare that there is no conflict of interest regarding the publication of this paper.
Ethical approval
This article does not contain any studies with human participants performed by any of the authors.
Additional information
This article is part of the Topical Collection on Systems-Level Quality Improvement
Rights and permissions
About this article
Cite this article
Avudaiappan, T., Balasubramanian, R., Pandiyan, S.S. et al. Medical Image Security Using Dual Encryption with Oppositional Based Optimization Algorithm. J Med Syst 42, 208 (2018). https://doi.org/10.1007/s10916-018-1053-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-018-1053-z