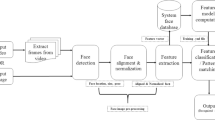
Abstract
Biometric-based authentication can provide strong security guarantee about the identity of users. However, security of biometric data is particularly important as the compromise of the data will be permanent. To protect the biometric data, we need to store it in a non-invertible transformed version. Thus, even if the transformed version is compromised, the actual biometric data remain safe. Fuzzy vault is a cryptographic construct to secure critical data with the fingerprint data. In this paper, we implement the fuzzy fingerprint vault, combining fingerprint verification and fuzzy vault scheme to protect fingerprint templates, for the smart card environment. To implement the fuzzy fingerprint vault as a complete system, we have to consider several practical issues such as automatic fingerprint alignment, verification accuracy, template size for storing in the smart card, execution time, error correcting code, etc. Especially, we handled the fingerprints having a few minutiae by applying an adaptive degree of the polynomial, and thus our implementation result can be used for real, large-scale applications.
Similar content being viewed by others
References
Bamasak O. (2010) Exploring consumers acceptance of mobile payments? An empirical study. International Journal of Information Technology, Communications and Convergence 1(2): 173–185
Berlekamp, E. (1984). Algebraic coding theory. McGraw-Hill: New York. (Revised edition, Laguna Hills: Aegean Park Press, 1984).
Bolle R., Connell J., Ratha N. (2002) Biometric perils and patches. Pattern Recognition 35: 2727–2738
Chong R., Tanaka T. (2010) Motion blur identification using maxima locations for blind colour image restoration. Journal of Convergence 1:1 49–56
Chung Y. et al (2005) Automatic alignment of fingerprint features for fuzzy fingerprint vault. LNCS 3822: 358–369
Clancy, T., et al. (2003). Secure smartcard-based fingerprint authentication. Proceedings of ACM SIGMM Multimedia Biome Met. & App (pp. 45–52).
FVC. (2002). http://bias.csr.unibo.it/fvc2002/databases.asp.
Gao, S. (2003) A new algorithm for decoding Reed-Solomon codes communications information and network security (pp. 55–68). Dordrecht: Kluwer.
Gil, Y. et al. (2001). Performance analysis of smart card-based fingerprint recognition for secure user authentication. Proceedings of IFIP on E-commerce, E-business, E-government (pp. 87–96).
Guruswami,V., Sudan, M. (1998). Improved secoding of Reed-Solomon and algebraic geometric codes. Proceedings of FOCS (pp. 28–39).
Janke, M. (2001). FingerCard project presentation, http://www.finger-card.org.
Juels, A., & Wattenberg, M. (1999). A fuzzy commitment scheme. Proceedings of ACM conference on computer and Commumication Security, pp. 28–36.
Juels, A., & Sudan, M. (2002). A fuzzy vault scheme. Proceedings of symposium on information theory (p. 408).
Kryvinska, N., et al. (2010). Integrated management platform for seamless services provisioning in converged network. International Journal of Information Technology, Communications and Convergence, 1(1), 77–91.
Ling, A., & Masao, M. (2011). Selection of model in developing information security criteria for smart grid security system. Journal of Convergence, 2(1), 39–46.
Maltoni D. et al (2003) Handbook of fingerprint recognition. Springer, NewYork
Moon D. et al (2007) Fingerprint template protection using fuzzy vault. LNCS 4707: 1141–1151
Nagar, A., et al. (2008). Securing fingerprint template: Fuzzy vault with minutiae descriptors. Proceedings of ICPR.
Nandakumar K. et al (2007) Fingerprint-based fuzzy vault: Implementation and performance. IEEE Transactions on Information Forensics and Security 2(4): 744–757
NitGen. www.nitgen.com.
Pan S. et al (2003) An ultra-low memory fingerprint matching algorithm and its implementation on a 32-bit smart card. IEEE Transactions on Consumer Electronics 49(2): 453–459
SAMSUNG. http://www.samsung.com.
Schneier B. (1999) The uses and abuses of biometrics. Communications of the ACM 42(8): 136
Scheirer, W., & Boult, T. (2007). Cracking Fuzzy Vaults and Biometric Encryption. Proceedings of IEEE biometrics research symposium at the National biometrics consortium conference.
Teoh A., Ngo D., Goh A. (2004) Biohashing: Two factor authentication featuring fingerprint data and tokenized random number. Pattern Recognition 37: 2245–2255
Uludag U. et al (2004) Biometric cryptosystems: Issues and challenges. Proceedings of IEEE 92(6): 948–960
Uludag, U., et al. (2005). Fuzzy vault for fingerprints. Proceedings of audio- and video-based biometric person authentication (pp 310–319).
Yang S., Verbauwhede I. (2005) Automatic secure fingerprint verification system based on fuzzy vault scheme. Proceeding of IEEE International Conference on Acoustics, Speech, and Signal Processing 5: 609–612
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Moon, D., Chung, Y., Seo, C. et al. A practical implementation of fuzzy fingerprint vault for smart cards. J Intell Manuf 25, 293–302 (2014). https://doi.org/10.1007/s10845-012-0656-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10845-012-0656-3