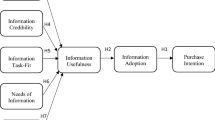
Abstract
Set in the backdrop of ever escalating data breach incidents, this paper investigates the seeming paradox between elevated consumer information security concerns reported in surveys and lax consumer security behavior exhibited online. Results from our experiment show that when asked about their information security perceptions, consumers evaluate the issue of information security based on the elaboration likelihood model. As a result, they express concerns. However, when consumers are actually shopping online, they do not separately evaluate the issue of information security. Instead, they mostly transfer their trust in an online retailer to the trusting belief that their information will be secure. This is one of the main reasons why, counter to their elevated security concerns expressed in surveys, consumers engage in lax security practices when they conduct business online.



Similar content being viewed by others
References
Aladwani, A. M., & Palvia, P. C. (2002). Developing and validating an instrument for measuring user-perceived web quality. Information and Management., 39(6), 467–476.
Amazon (2016). Product advertising API developer guide https://docs.aws.amazon.com/AWSECommerceService/latest/DG/Welcome.html. Accessed September 29, 2019.
Andrade, E. B., Kaltcheva, V., & Weitz, B. (2002). Self-disclosure on the web: The impact of privacy policy, reward, and company reputation. Advances in Consumer Research, 29(1), 350–353.
Baymard K. (2013). Which site seal do people trust the most? Baymard Institute. https://baymard.com/blog/site-seal-trust. Accessed September 29, 2019.
Beckwith, N. E., Kassarjian, H. H., & Lehmann, D. R. (1978). Halo effects in marketing research: Review and prognosis. Advances in Consumer Research, 5(1), 465–467.
Bhattacherjee, A. (2002). Individual trust in online firms: Scale development and initial test. Journal of Management Information Systems, 19(1), 211–241.
Blau, P. M. (1964). Exchange and power in social life. New York: John Wiley and Sons.
Bless, H., Mackie, D. M., & Schwarz, N. (1992). Mood effects on attitude judgements: Independent effects of mood before and after message elaboration. Journal of Personality and Social Psychology, 63(4), 585–595.
Breachlevelindex.com. (2018). 2017: the year of internal threats and accidental data breaches: findings from the 2017 breach level index. https://breachlevelindex.com/assets/Breach-Level-Index-Report-2017-Gemalto.pdf. Accessed September 29, 2019.
Bohner, G., & Weinerth, T. (2001). Negative affect can increase or decrease message scrutiny: The affect interpretation hypothesis. Personality and Social Psychology Bulletin, 27(11), 1417–1428.
Census.gov. (n.d.). Quarterly e-commerce report historical data. https://www.census.gov/retail/ecommerce/historic_releases.html. Accessed September 29, 2019.
Chang, H. H., & Chen, S. W. (2008). The impact of online store environment cues on purchase intention trust and perceived risk as a mediator. Online Information Review, 32(6), 818–841.
Chellappa, R. K., & Pavlou, P. A. (2002). Perceived information security, financial liability and consumer trust in electronic commerce transactions. Logistics Information Management, 15(5/6), 356–368.
Clemons, E. K., Wilson, J., Matt, C., Hess, T., Ren, F., Jin, F., & Koh, N. S. (2016). Global differences in online shopping behavior: Understanding factors leading to trust. Journal of Management Information Systems, 33(4), 1117–1148.
Cui, F., Lin, D., & Qu, H. (2018). The impact of perceived security and consumer innovativeness on e-loyalty in online travel shopping. Journal of Travel & Tourism Marketing, 35(6), 819–834.
Culnan, M. J., & Armstrong, P. K. (1999). Information privacy concerns, procedural fairness, and impersonal trust: An empirical investigation. Organization Science, 10(1), 104–115.
Dabholkar, P. A., & Sheng, X. (2012). Consumer participation in using online recommendation agents: Effects on satisfaction, trust, and purchase intentions. Service Industries Journal, 32(9), 1433–1449.
Dinev, T., & Hart, P. (2006). An extended privacy calculus model for e-commerce transactions. Information Systems Research, 17(1), 61–80.
Fang, Y., Qureshi, I., Sun, H., McCole, P., Ramsey, E., & Lim, K. H. (2014). Trust, satisfaction, and online repurchase intention: The moderating role of perceived effectiveness of e-commerce institutional mechanisms. MIS Quarterly, 38(2), 407–427.
FBI. (2017): 2016 Internet Crime Report. https://pdf.ic3.gov/2016_IC3Report.pdf. Accessed September 28, 2019.
Fogg, B.J., Marshall, J., Laraki, O., Osipovich, A., Varma, C., Fang, N., Paul, J., Rangnekar, A., Shon, J., Swani, P., and Treinen, M. (2001). What makes Web sites credible? A report on a large quantitative study, in Proceedings of the 2001 SIGCHI Conference on Human Factors in Computing Systems, Seattle, WA, 3/31/2001–4/5/2001, 61–68.
Fogg, B.J., Soohoo, C., Danielson, D.R., Marable, L., Stanford, J., & Tauber, E.R. (2003). How do users evaluate the credibility of Web sites? A study with over 2,500 participants. In Proceedings of DUX2003, Designing for User Experiences Conference.
Gemalto.com. (2016). Gemalto releases findings of 2016 breach level index. https://www.gemalto.com/press/pages/gemalto-releases-findings-of-2016-breach-level-index.aspx. Accessed September 28, 2019.
Goldberg, M. E., & Hartwick, J. (1990). The effects of advertiser reputation and extremity of advertising claim on advertising effectiveness. Journal of Consumer Research, 17(2), 172–179.
Ho, S. Y., & Bodoff, D. (2014). The effects of web personalization on user attitude and behavior: An integration of the elaboration likelihood model and consumer search theory. MIS Quarterly, 38(2), 497–520.
Holsapple, C. W., & Wu, J. (2008). Building effective online game websites with knowledge-based trust. Information Systems Frontier, 10(1), 47–60.
Janakiraman, R., Lim, J. H., & Rishika, R. (2018). The effect of a data breach announcement on customer behavior: Evidence from a multichannel retailer. Journal of Marketing, 82(2), 85–105.
Kassner, M. (2015). Anatomy of the target data breach: missed opportunities and lessons learned. https://www.zdnet.com/article/anatomy-of-the-target-data-breach-missed-opportunities-and-lessons-learned/. Accessed September 29, 2019.
Kim, J. (2017). Elaborating the halo effect of SCCT: How and why performance history affects crisis responsibility and organizational reputation. Journal of Public Relations Research, 29(6), 277–294.
Kim, J., Jin, B., & Swinney, J. L. (2009). The role of e-tail quality, e-satisfaction, e-trust in online loyalty development process. Journal of Retailing and Consumer Services, 16(4), 239–247.
Klein, J., & Dawar, N. (2004). Corporate social responsibility and consumers’ attributions and brand evaluations in a product-harm crisis. International Journal of Marketing, 21(3), 203–217.
Laczniak R.N., Muehling D.D. and Carlson L. (1991). Effects of motivation and ability on ad-induced cognitive processing. In Proceedings of the 1991 Conference of the American Academy of Advertising, 81–87, New York: D’Arcy Masius Benton and Bowles.
Lee, J., Lee, J.-N., & Tan, B. C. Y. (2015). Antecedents of cognitive trust and affective distrust and their mediating roles in building customer loyalty. Information Systems Frontier, 17(1), 159–175.
Liao, Z., & Shi, X. (2017). Web functionality, web content, information security, and online tourism service continuance. Journal of Retailing and Consumer Services, 39, 258–263.
Lim, K. H., Sia, C. L., Lee, M. K. O., & Benbasat, I. (2006). Do I trust you online, and if so, will I buy? An empirical study of two trust-building strategies. Journal of Management Information Systems, 23(2), 233–266.
Lowry, P. B., Wilson, D., & Haig, B. (2014). A picture is worth a thousand words: Source credibility theory applied to logo and website design for heightened credibility and consumer trust. Journal of Human Computer Interaction, 30(1), 63–93.
m-w.com: (n.d.). Merriam-Webster online dictionary. https://www.merriam-webster.com/dictionary/trust. Accessed September 29, 2019.
Mauldin, E., & Arunachalam, V. (2002). An experimental examination of alternative forms of web assurance for business-to-consumer eCommerce. Journal of Information Systems, 16(s1), 33–54.
Mayer, R. C., Davis, J. H., & Shoorman, F. D. (1995). An integrative model of organizational trust. Academy of Management Review, 20(3), 709–734.
McAllister, D. J. (1995). Affect- and cognition-based trust as foundations for interpersonal cooperation in organizations. The Academy of Management Journal, 38(1), 24–59.
McKnight, D. H., Choudhury, V., & Kacmar, C. (2002). The impact of initial consumer trust on intentions to transact with a website: A trust building model. Journal of Strategic Information Systems, 11(3–4), 297–323.
Mousavizadeh, M., Kim, D. J., & Chen, R. (2016). Effects of assurance mechanisms and consumer concerns on online purchase decisions: An empirical study. Decision Support Systems, 92, 79–90.
O’Keefe, D. (2016). Persuasion theory and research (3rd ed.). Los Angeles: Sage Publications.
Pavlou, P. A., & Gefen, D. (2004). Building effective online marketplaces with institution-based trust. Information Systems Research, 15(1), 37–59.
Petty, R. E., & Cacioppo, J. T. (1986). The elaboration likelihood model of persuasion. Advances in Experimental Social Psychology, 19(1), 123–205.
Petty, R. E., Cacioppo, J. T., & Goldman, R. (1981). Personal involvement as a determinant of argument-based persuasion. Journal of Personality and Social Psychology, 41(5), 847–856.
Petty, R., Cacioppo, J., & Schumann, D. (1983). Central and peripheral routes to advertising effectiveness: The moderating role of involvement. Journal of Consumer Research, 10(2), 135–146.
Pew Research. (2016). Online shopping and e-commerce. http://www.pewinternet.org/2016/12/19/online-shopping-and-e-commerce/. Accessed September 29, 2019.
PwC. (2017). Consumer intelligence series: protect.me. https://www.pwc.com/us/en/services/ consulting/library/consumer-intelligence-series/cybersecurity-protect-me.html. Accessed September 29, 2019.
Reuter. (2017). Target settles 2013 hacked customer data breach for $18.5 million. https://www.nbcnews.com/business/business-news/target-settles-2013-hacked-customer-data-breach-18-5-million-n764031. Accessed September 29, 2019.
Ring, P. S., & Van de Ven, A. H. (1994). Developmental processes of cooperative interorganizational relationships. Academy of Management Review, 19(1), 90–118.
Sahoo, N., Krishnan, R., Duncan, G., & Callan, J. (2012). The halo effect in multicomponent ratings and its implications for recommender systems: The case of yahoo! Movies. Information Systems Research, 23(1), 231–246.
Salisbury, W. D., Pearson, R. A., Pearson, A. W., & Miller, D. W. (2001). Perceived security and world wide web purchase intention. Industrial Management and Data Systems, 101(4), 165–176.
Shapiro, D. L., Sheppard, B. H., & Cheraskin, L. (1992). Business on a handshake. Negotiation Journal, 3(4), 365–377.
Sharma, S. K. (2019). Integrating cognitive antecedents into TAM to explain mobile banking behavioral intention: A SEM-neural network modeling. Information Systems Frontier, 21(4), 815–827.
Simons, H. W. (1976). Persuasion: Understanding, practice, and analysis. Reading: Addison-Wesley.
Steward, K. J. (2003). Trust transfer on the world wide web. Organization Science, 4(1), 5–17.
Symantec (2018a). Consumers’ overconfidence helps hackers up the ante and steal $172 billion in 2017. https://www.symantec.com/about/newsroom/press-releases/2018/symantec_0122_01. Accessed September 29, 2019.
Symantec. (2018b). 2019 Internet security threat report. https://www.symantec.com/security-center/threat-report. Accessed September 29, 2019.
Tam, K. Y., & Ho, S. Y. (2005). Web personalization as a persuasion strategy: An elaboration likelihood model perspective. Information Systems Research, 16(3), 271–291.
Touré-Tillery, M., & McGill, A. L. (2015). Who or what to believe: Trust and the differential persuasiveness of human and anthropomorphized messengers. Journal of Marketing, 79(4), 94–110.
USDHHS. 2015. U.S. Information memorandum, Department of Health and Human Services, Administration for Children and Families http://www.acf.hhs.gov/sites/default/files/cb/im1504.pdf. Accessed September 29, 2019.
Valdez, A. D. F., Cervantes, A. V., & Motyka, S. (2018). Beauty is truth: The effects of inflated product claims and website interactivity on evaluations of retailers’ websites. Journal of Business Research, 90, 67–74.
Wang, N., Shen, X. L., & Sun, Y. (2013). Transition of electronic word-of-mouth services from web to mobile context: A trust transfer perspective. Decision Support Systems, 54(3), 1394–1403.
Wood, W. (1982). Retrieval of attitude-relevant information from memory: Effects on susceptibility to persuasion and on intrinsic motivation. Journal of Personality and Social Psychology, 42(5), 798–810.
Wood, W., Kallgren, C. A., & Preisler, R. M. (1985). Access to attitude-relevant information in memory as a determinant of persuasion: The role of message attributes. Journal of Experimental Social Psychology, 21(1), 73–85.
Xu, H., Dinev, T., Smith, J., & Hart, P. (2011). Information privacy concerns: Linking individual perceptions with institutional privacy assurances. Journal of the Association for Information Systems, 12(2), 798–824.
Zhou, T., Lu, Y., & Wang, B. (2016). Examining online consumers’ initial trust building from and elaboration likelihood model perspective. Information Systems Frontier, 18(2), 265–275.
Ziegler, R. (2010). Mood, source characteristics and message processing: A mood-congruent expectancies approach. Journal of Experimental Social Psychology, 46(5), 743–752.
Acknowledgements
This paper is an extended version of a short paper presented at the 2018 International Conference on Information Systems, San Francisco, USA and published in its proceedings. We are grateful to the two anonymous reviewers, the AE, and the CE for their valuable comments and suggestions, which helped us improve this paper greatly.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A. Screenshots of Research eCommerce Website
Screenshot of the initial participant landing page for shopsabbas.com
Appendix B. Measurement Items
Trust in the Retailer: second-order formative construct with two dimensions: Perceived Trustworthiness and Perceived Expertise.
Perceived Trustworthiness: 7-point semantic differential scale using the following 8 pairs of adjectives.
dishonest | honest |
Trustworthy | Untrustworthy |
Bad | Good |
Unreliable | Reliable |
Disreputable | Reputable |
Dependable | Undependable |
Irresponsible | Responsible |
Consistent | Inconsistent |
Perceived Expertise: 7-point semantic differential scale using the following 7 pairs of adjectives:
Inexperienced | Experienced |
Unskilled | Skilled |
Informed | Uninformed |
Incompetent | Competent |
Knowledgeable | Ignorant |
Ineffective | Effective |
Weak | Strong |
Website Sophistication: 7-point Likert scale anchored on strongly disagree, disagree, somewhat disagree, neither agree nor disagree, somewhat agree, agree, and strongly agree.
- 1.
The shopsabbas.com website looks attractive.
- 2.
The shopsabbas.com website looks organized.
- 3.
The shopsabbas.com website uses fonts properly.
- 4.
The shopsabbas.com website looks color properly.
- 5.
The content of shopsabbas.com website is clear.
- 6.
The content of shopsabbas.com website is current.
- 7.
The content of shopsabbas.com website is concise.
- 8.
The content of shopsabbas.com website is accurate.
Perceived Information security: 7-point Likert scale anchored on strongly disagree, disagree, somewhat disagree, neither agree nor disagree, somewhat agree, agree, and strongly agree.
- 1.
I would feel secure sending sensitive information across shopsabbas.com.
- 2.
I would feel totally safe providing sensitive information about myself on shopsabbas.com.
- 3.
Shopsabbas.com is a secure website for sending sensitive information.
- 4.
Overall, shopsabbas.com is a safe place to transmit my sensitive information.
Intention to Purchase: 7-point Likert scale anchored on strongly disagree, disagree, somewhat disagree, neither agree nor disagree, somewhat agree, agree, and strongly agree.
- 1.
I would use shopsabbas.com for purchasing a product.
- 2.
Using shopsabbas.com for purchasing a product is something I would do.
- 3.
I could see myself using shopsabbas.com to buy a product.
- 4.
It is likely that I will transact with shopsabbas.com website in the future.
Rights and permissions
About this article
Cite this article
Mohr, H., Walter, Z. Formation of Consumers’ Perceived Information Security: Examining the Transfer of Trust in Online Retailers. Inf Syst Front 21, 1231–1250 (2019). https://doi.org/10.1007/s10796-019-09961-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10796-019-09961-7