Abstract
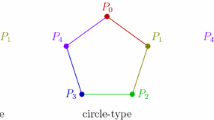
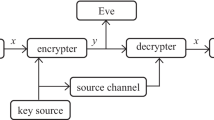
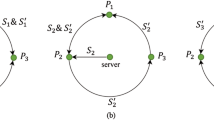
It's conceivable to have a few dishonest participants when you want to exchange a secret key among participants in a certain network. Due to dishonest participants, a secret key could be altered and disclosed outside of a network. It is reasonable that each participant's involvement would be assessed by a certain organization. The same approach that a secret key must be protected by a header. The protocol to identify two dishonest members in a circular network was proposed by Liu et al. To identify conspirators, Sun et al. expand on the work of Liu et al. Sun et al. suggested a multiparty quantum key agreement protocol based on a circular-type, in which the dishonesty of each member was unknown. To investigate dishonesty, we append a header with a secret key to the Liu et al. and Sun et al. works. Because of the header, the following participants are aware of secret key tampering. Even if some participants became dishonest about a secret key, a circle-type network provided absolute security. There is no performance degradation of the proposed multiparty quantum key agreement protocol with addition of a header.










Similar content being viewed by others
Data Availability
The data used to support the finding of this study are included in https://arxiv.org/pdf/1604.01112.pdf.
References
Stallings, W.: Network security essentials: Applications and standards, 4th edn. Pearson Education, India (2003)
Moore, G.E.: Cramming more components onto integrated circuits. 114–117 (1965)
Stallings, W..: Cryptography and network security, 4th edn. Pearson Education, India (2006)
Stinson, D.R.: Cryptography: theory and practice. Chapman and Hall/CRC (2005)
Nielsen, M.A., Chuang, I.: Quantum computation and quantum information. 558–559 (2002)
Perry, R.T.: The temple of quantum computing. Riley Perry standard, Australia, Available on: http://www.toqc.com/TOQCv1_1.pdf. Accessed 10 Mar 2022.
Pittenger, A.O. An introduction to quantum computing algorithms, Vol. 19. Springer Science & Business Media (2012)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68(21), 3121 (1992)
Bennett, C.H., et al.: Teleporting an unknown quantum state via dual classical and Einstein-Podolsky-Rosen channels. Phys. Rev. Lett. 70(13), 1895 (1993)
Bennett, C.H., et al.: Strengths and weaknesses of quantum computing. SIAM J. Comput. 26(5), 1510–1523 (1997)
Bennett, C.H., Shor, P.W.: Quantum information theory. IEEE Trans. Inf. Theory 44(6), 2724–2742 (1998)
Bennett, C.H., DiVincenzo, D.P.: Quantum information and computation. Nature 404(6775), 247–255 (2000)
Bennett, C.H., Brassard G.: Quantum cryptography: Public key distribution and coin tossing. arXiv preprint arXiv:2003.06557 (2020)
Ekert, A.K.: Quantum Cryptography and Bell’s Theorem. Quantum Measurements in Optics, pp. 413–418. Springer, Boston (1992)
Chun-Yan, L., et al.: Secure quantum key distribution network with Bell states and local unitary operations. Chin. Phys. Lett. 22(5):1049 (2005) https://arxiv.org/pdf/0705.1746.pdf. Accessed 10 Mar 2022
Branciard, Cyril, et al.: Security of two quantum cryptography protocols using the same four qubit states. Phys. Rev. A 72(3), 032301 (2005)
Bernstein, E., Vazirani, U.: Quantum complexity theory. SIAM J. Comput. 26(5), 1411–1473 (1997)
Sun, Z., Huang, J., Wang, P.: Efficient multiparty quantum key agreement protocol based on commutative encryption. Quantum Inf. Process. 15(5), 2101–2111 (2016)
Mohajer, R., Eslami, Z.: Cryptanalysis of a multiparty quantum key agreement protocol based on commutative encryption. Quantum Inf. Process. 16(8), 1–9 (2017)
Huang, W., et al.: Cryptanalysis of a multi-party quantum key agreement protocol with single particles. Quantum Inf. Process. 13(7), 1651–1657 (2014)
Cao, H., Ma, W.: Multiparty quantum key agreement based on quantum search algorithm. Sci. Rep. 7(1), 1–10 (2017)
Gu, J., Hwang, T.: Improvement of “Novel multiparty quantum key agreement protocol with GHZ states.” Int. J. Theor. Phys. 56(10), 3108–3116 (2017)
Liu, B., et al.: Multiparty quantum key agreement with single particles. Quantum Inf. Process. 12(4), 1797–1805 (2013)
Liu, H.-N., et al.: Multi-party quantum key agreement protocol with bell states and single particles. Int. J. Theor. Phys. 58(5), 1659–1666 (2019)
Liu, B., et al.: Collusive attacks to “circle-type” multi-party quantum key agreement protocols. Quantum Inf. Process. 15(5), 2113–2124 (2016)
Min, S.-Q., Chen, H.-Y., Gong, L.-H.: Novel multi-party quantum key agreement protocol with g-like states and bell states. Int. J. Theor. Phys. 57(6), 1811–1822 (2018)
Sun, Z., Jianping, Yu., Wang, P.: Efficient multi-party quantum key agreement by cluster states. Quantum Inf. Process. 15(1), 373–384 (2016)
Wang, P., Sun, Z., Sun, X.: Multi-party quantum key agreement protocol secure against collusion attacks. Quantum Inf. Process. 16(7), 1–10 (2017)
Xu, G.-B., et al.: Novel multiparty quantum key agreement protocol with GHZ states. Quantum Inf. Process. 13(12), 2587–2594 (2014)
Yin, X.-R., Ma, W.-P., Liu, W.-Y.: Three-party quantum key agreement with two-photon entanglement. Int. J. Theor. Phys. 52(11), 3915–3921 (2013)
Cabello, A.: Multiparty key distribution and secret sharing based on entanglement swapping. arXiv preprint quant-ph/0009025 (2000)
Zhao, X.-Q., et al.: Multiparty quantum key agreement protocol with entanglement swapping. Int. J. Theor. Phys. 58(2), 436–450 (2019)
Bennett, C.H., Brassard, G.: Public-key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, pp. 175–179. Ban-galore (1984)
Sihare, S., Nath, V.V.: Multiple Entities Search through Simon's Quantum Algorithm. 2017 IEEE 7th International Advance Computing Conference (IACC). IEEE, (2017)
Sihare, S., Nath, V.: Revisited quantum protocols. Int. J. Math. Sci. Comput. (IJMSC) 3(2), 11–21 (2017)
Sihare, S.R., Nath, V.V.: Application of quantum search algorithms as a web search engine. 2016 International Conference on Global Trends in Signal Processing, Information Computing and Communication (ICGTSPICC). IEEE, (2016)
Nath, V.V.: Time and space complexies of Shor’s, Grover’s Algorithms Over Classical Algorithms.
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 85(26), 5635 (2000)
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The author declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sihare, S.R. Multi-party Quantum Key Agreement Protocol for Detection of Collusive Attacks in each Sub-Circle Segment by Headers. Int J Theor Phys 61, 208 (2022). https://doi.org/10.1007/s10773-022-05184-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10773-022-05184-w