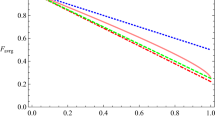
Abstract
As is known, quantum key distribution (QKD) can theoretically realize information-theoretic security with a reliable identity authentication protocol. However, the most commonly used identity authentication protocol based on public-key cryptography cannot resist the attacks from the adversaries with the ability of quantum computing, so quantum identity authentication (QIA) is one of the alternatives to be considered. By adjusting the length of interference circuit, we propose a QIA protocol based on the communication circuit of GV95 protocol and prove its security in theory. On this basis, an authenticated QKD protocol based on orthogonal-state-encoding is designed by mixing the process of QKD and QIA randomly. Compared with a similar protocol proposed in 2020, our protocol is simpler and requires less quantum communication equipment. Therefore, both the cost and difficulty of implementing our protocol is lower than the previous protocol.




Similar content being viewed by others
Change history
25 July 2022
A Correction to this paper has been published: https://doi.org/10.1007/s10773-022-05155-1
References
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441 (2000)
Bennett, C.H., Brassard, G.: Quantum cryptography: Public key distribution and coin tossing. arXiv:2003.06557 (2020)
Ekert, A.K.: Quantum Cryptography and Bells Theorem[M]//Quantum Measurements in Optics, pp 413–418. Springer, Boston (1992)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68(21), 3121 (1992)
Goldenberg, L., Vaidman, L.: Quantum cryptography based on orthogonal states. Phys. Rev. Lett. 75(7), 1239 (1995)
Sun, Y., Wen, Q.Y., Gao, F., et al.: Robust variations of the Bennett-Brassard 1984 protocol against collective noise. Phys. Rev. A 80(3), 032321 (2009)
Song, T.T., Wen, Q.Y., Guo, F.Z., et al: Finite-key analysis for measurement-device-independent quantum key distribution. Phys. Rev. A 86(2), 022332 (2012)
Lin, S., Guo, G.D., Gao, F., et al.: Quantum key distribution: defeating collective noise without reducing efficiency. Quantum Inf. Comput. 14 (9&10), 845–856 (2014)
Li, Y.B.: Analysis of counterfactual quantum key distribution using error-correcting theory. Quantum Inf. Process. 13(10), 2325–2342 (2014)
Richard, C., Daniel, G., Lo, H.K.: How to share a quantum secret. Phys. Rev. Lett 83, 648–651 (1999)
Yang, Y.G., Wen, Q., Zhang, X.: Multiparty simultaneous quantum identity authentication with secret sharing. Sci. China Series G Phys. Mech. Astron. 51(3), 321–327 (2008)
Qina, S.J., Gao, F., Wen, Q.Y., et al.: Security of quantum secret sharing with two-particle entanglement against individual attacks. Quantum Inf. Comput. 9(9), 765–772 (2009)
Wang, Q., Yu, C., Li, Y., et al.: Authenticated quantum sortition and application in “Picking at random” problems. IEEE Commun. Lett. 25 (2), 518–522 (2020)
Lin, S., Wen, Q.Y., Qin, S.J., et al.: Multiparty quantum secret sharing with collective eavesdropping-check. Opt. Commun. 282(22), 4455–4459 (2009)
Xu, G.B., Jiang, D.H.: Novel methods to construct nonlocal sets of orthogonal product states in an arbitrary bipartite high-dimensional system. Quantum Inf. Process 20(4), 1–38 (2021)
Wang, T.Y., Wen, Q.Y.: Security of a kind of quantum secret sharing with single photons. Quant. Inf. Comput. 11(5), 434–443 (2011)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829 (1999)
Long, G.L., Liu, X.S.: Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A 65(3), 032302 (2002)
Wang, Q., Li, Y., Yu, C., et al.: Quantum-based anonymity and secure veto. Quantum Inf. Process 20(3), 1–22 (2021)
Deng, F.G., Long, G.L.: Controlled order rearrangement encryption for quantum key distribution. Phys. Rev. A 68(4), 042315 (2003)
Boström, K., Felbinger, T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89(18), 187902 (2002)
Lin, S., Wen, Q.Y., Gao, F., et al: Quantum secure direct communication with χ-type entangled states. Phys. Rev. A, 7(6), 064304 (2008)
Gao, F., Qin, S.J., Wen, Q.Y., et al.: Cryptanalysis of multiparty controlled quantum secure direct communication using Greenberger–Horne–Zeilinger state. Opt. Commun. 283(1), 192–195 (2010)
Huang, W., Wen, Q-Y, Jia, H-Y, Qin, S-J, Gao, F.: Fault tolerant quantum secure direct communication with quantum encryption against collective noise. Chinese Phys. B 21(10) (2012)
Giovannetti, V., Lloyd, S., Maccone, L.: Quantum private queries. Phys. Rev. Lett. 100(23), 230502 (2008)
Jakobi, M., Simon, C., Gisin, N., et al: Practical private database queries based on a quantum-key-distribution protocol. Phys. Rev. A 83(2), 022301 (2011)
Gao, F., Liu, B., Huang, W., et al.: Postprocessing of the oblivious key in quantum private query. IEEE J. Sel. Top. Quantum Electron. 21(3), 98–108 (2014)
Liu, B., Gao, F., Huang, W., et al.: QKD-Based quantum private query without a failure probability. Sci. China Phys. Mech. Astron. 58(10), 1–6 (2015)
Wei, C.Y., Cai, X.Q., Liu, B., et al.: A generic construction of quantum-oblivious-key-transfer-based private query with ideal database security and zero failure. IEEE Trans. Comput. 67(1), 2–8 (2017)
Liu, B., Xia, S., Xiao, D., et al.: Decoy-state method for quantum-key-distribution-based quantum private query. Sci. China Phys. Mech. Astron. 65(4), 1–8 (2022)
Wegman, M.N., Carter, J.L.: New hash functions and their use in authentication and set equality. J. Comput. Syst. Sci. 22(3), 265–279 (1981)
Dušek, M, Haderka, O., Hendrych, M., et al.: Quantum identification system. Phys. Rev. A 60(1), 149 (1999)
Goldenberg, L., Vaidman, L.: Quantum cryptography based on orthogonal states. Phys. Rev. Lett. 75(7), 1239 (1995)
Liu, B., Gao, Z., Xiao, D., et al.: Quantum identity authentication in the orthogonal-state-encoding QKD system. Quantum Inf. Process 18(5), 1–16 (2019)
Hou, F., Zhou, Q., Jin, Z., et al.: Authenticated QKD protocol based on Single-Photon interference. IEEE Access 8, 135357–135370 (2020)
Funding
This work is supported by National Natural Science Foundation of China (Grant Nos 62171418, U19A2076, 61901425, 61702061), Natural Science Foundation of Chongqing, China (Grant Noscstc220jcyj-msxmX0719), National Science Key Lab Fund project(Grant Nos 6142103200105), Fundamental Research Funds for the Central Universities (Grant Nos. 2020CDJQY-A018, 2020CDJ-LHZZ-056), Sichuan Science and Technology Program (Grant2019JDJQ0060).
Author information
Authors and Affiliations
Contributions
All authors contributed to study conception and design. Qiaoling Xiong, Fen Hou and Bin Liu completed the design of QIA and QKD protocols. Bin Liu, Wei Huang, Bingjie Xu and Yang Li completed the security analysis of protocols. And Qiaoling Xiong and Fen Hou co-wrote this paper. All authors read and proved the final manuscript.
Corresponding author
Ethics declarations
Conflict of Interests
The authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The original online version of this article was revised: The department of the authors of Bin Liu, Wei Huang, Bingjie Xu and Yang Li are wrong in the online published version. Bin Liu‘s department should be affiliations 1 and 2, and Wei Huang's, Bingjie Xu's and Yang Li's should be 2.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Xiong, Q., Fen, H., Liu, B. et al. Authenticated QKD Based on Orthogonal States. Int J Theor Phys 61, 151 (2022). https://doi.org/10.1007/s10773-022-05140-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10773-022-05140-8