Abstract
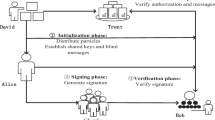
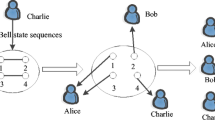
From the practical demand, this paper proposes a quantum (t,n) threshold proxy blind signature scheme based on Bell states. In our scheme, any t members of n proxy signers can cooperate to generate valid signatures on behalf of the original signer, and less than t can not. The original signer uses the quantum-controlled-not operations to expand the single particle quantum state into t-particle quantum states, and then uses the entanglement swapping to transmit the signature right of the original signer to t proxy signers. The proxy signers cooperate to complete signatures,through single particle measurements and performing the unitary operations of Pauli operator on arbitrarily Bell states. With the assistance of arbitration,the message receiver recovers the initial quantum information through single particle measurements and corresponding unitary operation to complete the verification. In order to ensure the secrecy of the message, the scheme also blinds the message, so that no one can know the content of the message except the owner and receiver of the message. The scheme is mainly completed by a series of quantum technologies and quantum algorithms, such as quantum key distribution protocol, quantum one-time pad algorithm, CNOT operation, Bell measurement, single particle measurement and unitary operation. So, it has the security of quantum signature. And the technologies used are general quantum technology, which is convenient for practice. Therefore, our quantum (t,n) threshold proxy blind signature scheme is a more practical signature scheme.
Similar content being viewed by others
Data Availability
The data in this article can be made public.
References
Rivest, R.L., Shamir, A., Aldleman, L.: A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21, 120–126 (1978)
Mambo, M., Usuda, K., Okamoto, E.: Proxy signatures for delegating signing operation. In: Proceedings of the 3rd ACM Conference on Computer and Communications Security, pp. 48–57, New Delhi (1966)
Chaum, D.: Blind signature for untraceable payments. In: Proceeding of CRTPTOi-82, pp. 199–203. Plenum Publishing (1982)
Lin, W.D., Jan, J.K.: A security personal learning tools using a proxy blind signature scheme. In: Proceedings of International Conference on Chinese Language Computing, pp. 273–277. IEEE Press Illinois, USA (2000)
Desmedt, Y., Frankel, Y.: Shared generation of authenticators and signatures[J]. Proc. CRYPTO91 Lect. Note Comput. Sci. 576, 457–469 (1992)
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26(5), 1484–1509 (1997)
Grover, L.K.: A fast quantum mechanical algorithm for database search. In: Twenty-eighth ACM Symposium on Theory of Computing, pp. 212–219 (1996)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441–444 (2000)
Mayers, D.: Unconditional security in quantum cryptography. J. ACM 48(3), 351–406 (2001)
Inamon, H., Lutkenhaus, N., Mayers, D.: Unconditional security of practical quantum key distribution. Eur. Phys. J. D 41(3), 599–627 (2007)
Deng, F.G., Long, G.L.: Secure direct communication with a quantum one-time pad. Phys. Rev. A 052319, 69 (2004)
Gottesman, D., Chuang, I.: Quantum digital signature arXiv:0105032v2 (2001)
Bamum, H., et al.: Authentication of quantum messages. In: Focs2002: 43rd Annual IEEE symposium on Foundations of Computer Science, Proceedings, pp 449–458 (2002)
Zeng, G., Keitel, C.H.: Arbitrated quantun-siganture scheme. Phys. Rev. A65(4), 0423 (2002)
Shi, R.H., Feng, Y.Y., Shi, J.J.: Arbitrated quantum signature scheme with quantum walks on regular graphs. J Electron. Inform. Technol. 42(1), 89–97 (2020)
Lou, X.P., Tang, W.S., Long, H., Cheng, Y.: A quantum blind signature scheme based on block encryption and quantum fourier transfer. Int. J Theor. Phys. 58, 3192–3202 (2019)
Li, X.Y., Chang, Y., Zhang, S.B., Dai, J.Q., Zheng, T.: Quantum blind signature scheme based on quantum walk. Int. J Theor. Phys. 59, 2059–2073 (2020)
Qin, H.W., Wallace, K.S., Tang, R.T.: Efficient quantum multi-proxy signature. Quantum Inform. Process. 18, 53 (2019)
Tan, R.M., Yang, Q.L.: Comments on the efficient quantum multi-proxy signature. Quantum Inf. Process 19, 288 (2020)
Zheng, T., Zhang, S.B., Chang, Y., Yan, L.L.: A quantum proxy arbitrated signature scheme based on two three-qubit GHZ states, pp 289–297. Springer, Switzerland (2020)
Liang, X.Q., Wu, Y.L., et al.: Quantum multi-proxy blind signature scheme based on four-qubit cluster states. Int. J Theor. Phys. 58, 31–39 (2019)
Liu, G., Ma, W.P., et al.: A novel quantum group proxy blind signature scheme based on five-qubit entangled state. Int. J Theor. Phys. 58, 1999–2008 (2019)
Zhou, B.M., Lin, L.D., Wang, W., Liu, Y.: Security analysis of particular quantum proxy blind signature against the forgery attack. Int. J. Theor. Phys. 59, 465–473 (2020)
Zhang, X., Zhang, J.Z., Xie, S.C.: A quantum proxy signature scheme by using random sequence to blind the message. Int. J. Theor. Phys. 58, 2081–2090 (2019)
Niu, X.F., Ma, W.P., Chen, B.Q., Liu, G., Wang, Q.Z.: A quantum proxy blind signature scheme based on superdense coding. Int. J. Theor. Phys. 59, 1121–1128 (2020)
Yang, Y.G., Wen, Q.Y.: Threshold proxy quantum signature scheme with threshold shared verifcation. Sci. China Phys. Mech. Astron. 51, 1079–1088 (2008)
Shamir, A.: How to share a secret. Commun. ACM 11, 612–613 (1979)
Shi, J.J., Shi, R.H., Guo, Y., Peng, X.Q., Lee, M.H., Park, D.S.: A (t, n)-threshold scheme of multiparty quantum group signature with irregular quantum Fourier transform. Int. J. Theor. Phys. 51, 1038–1049 (2012)
Qin, H.W., Wallace, K.S., Tang, R.T.: Quantum (t, n) threshold group signature based on bell state. Quantum Inform. Process. 19, 71 (2020)
Bennett, C.H., Brassard, G.: Quantum cryptography: public-key distribution and coin tossing. In: IEEE International Conference on Computers, Systems, and Signal Processing, Bangalore, pp. 175–179 (1984)
Lo, H.K., Ma, X.F., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 230504, 94 (2005)
Deng, F.G., Long, G.L.: Secure direct communication with a quantum one-time pad. Phys. Rev. A 052319, 69 (2004)
Hu, J.Y., Yu, B., Jing, M.Y., et al.: Experimental quantum secure direct communication with single photons. Light Sci. Appl. e16144, 5 (2016)
Vernam, G.: Cipher printing telegraph systems for secret wire and radio telegraphic communication. Trans. A. I. E. E. XLV, 295–301 (1926)
Zhao, Q.L., Li, X.Y.: A bargmann system and the involutive solutions associated with a new 4-order lattice hierarchy. Anal. Math. Phys. 6(3), 237–254 (2016)
Qin, H.W., Dai, Y.W.: Verifiable (t,n) threshold quantum secert sharing using d-dimensional Bell state. Inform. Process. Lett. 116, 351–355 (2016)
Fan, L., Zhang, K.J., Qin, S.J., Guo, F.Z.: A novel quantum blind signature scheme with four-particle GHZ states. Int. J. Theor. Phys. 55, 1028–1035 (2016)
Zeng, G.H., Keitel, C.H.: Arbitrated quantum-signature scheme. Phys. Rev. A 042312, 65 (2002)
Li, Q., Chan, W.H., Long, D.Y.: Arbitrated quantum signature scheme using Bell states. Phys. Rev. A 054307, 79 (2009)
Ma, M., Li, Z.H., Xu, T.T.: Verifiable (n,n) threshold quantum secret sharing scheme. Comput. Eng. 43(8), 169–172 (2017)
Funding
This work is supported by the Postdoctoral Science Foundation of China (Grant Nos. 2018M633456) and Natural Science Basic Research Program of Shaanxi Province(Grant Nos. 2019JQ-472)
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Ethics approval
There is no conflict of interest involved. All authors read and approved the final manuscript.
Conflicts of interest/Competing interests
The authors have no conflicts of interest to declare that are relevant to the content of this article.
Consent for Publication
Agree to publish
Additional information
Consent to participate
All authors contributed to the study conception and design. The first draft of the manuscript was written by Yu Jing. Mr. Zhang Jianhua revised the paper. All authors read and approved the final manuscript.
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Yu, J., Zhang, J. Quantum (t,n) Threshold Proxy Blind Signature Scheme Based on Bell States. Int J Theor Phys 61, 207 (2022). https://doi.org/10.1007/s10773-022-05112-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10773-022-05112-y