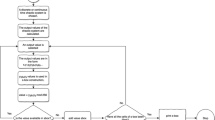
Abstract
Chaotic maps play a vital role in the development of cryptographic techniques being used in today’s world. Efficient and highly secure algorithms can be constructed based on chaotic maps. Chaotic maps have the intrinsic property of being highly sensitive to initial conditions. In this paper, we have presented a novel scheme for construction and optimization of substitution boxes (S-boxes) based on mixed two dimensional (2D) chaotic maps in which cryptographic properties of S-boxes are optimized based on initial conditions of their parent 2D chaotic map. The proposed scheme and the resulting substitution boxes are analyzed with existing cryptanalysis techniques and their results have been compared with some other algorithms available in literature. The proposed scheme has been found to be more efficacious than other algorithms. The outcomes of security analysis indicate that our proposed technique and resulting optimized non-linear component in the current era of information technology.































Similar content being viewed by others
References
Menezes, A.J., Oorschot, P.C.V., Vanstone, S.A.: Handbook of Applied Cryptography. CRC Press, Boca Raton (1997)
Stinson, D.R.: Cryptography: Theory and Practice. CRC Press, Boca Raton (2005)
Schneier, B.: Applied Cryptography: Protocols Algorithms and Source Code in C. Wiley, New York (1996)
Fatih, Ö., Ahmet, B.Ö.: A method for designing strong S-boxes based on chaotic Lorenz system. Phys. Lett. A. 374(36), 3733–3738 (2010)
Ahmad, M., Haleem, H.: A new chaotic substitution box design for block ciphers. International Conference on Signal Processing and Integrated Networks (SPIN). 1, 255–258 (2014)
Lambic, D.: A novel method of S-box design based of discrete chaotic map. Nonlinear Dynamics. 87, 2407–2413 (2017)
Chen, G., Chen, Y., Liao, X.F.: An extended method for obtaining S-boxes based on three-dimensional chaotic baker maps. Chaos, Solitons and Fractals. 31(3), 571–579 (2007)
Yin, J.Y., Wang, J., Shan, X.M., Wang, X.Q.: Designing key-dependent chaotic S-box with larger key space. Chaos, Solitons and Fractals. 42(4), 2582–2589 (2009)
Wang, Y., Wong, K.W., Li, C.B., Li, Y.: A novel method to design S-box based on chaotic map and genetic algorithm. Phys. Lett. A. 376(6), 827–833 (2012a)
Jakimoski, G., Kocarev, L.: Chaos and cryptography: block encryption ciphers based on chaotic maps. IEEE Transactions Circuits and Systems. 48(2), 163–169 (2001)
Özkaynak, F., Çelik, V., Özer, A.B.: A new S-box construction method based on the fractional-order chaotic Chen map. Signal Image Video Process. 11, 659–664 (2017)
Khan, M., Azam, N.A.: S-boxes based on affine mapping and orbit of power function. 3D Res. 6(2), 1–15 (2015)
Çavusoglu, Ü., Zengin, A., Pehlivan, I., Kaçar, S.: A novel approach for strong S-box generation algorithm design based on chaotic scaled Zhongtang map. Nonlinear Dynamics. 87, 1081–1094 (2017)
Ullah, A., Shaukat, S., Tariq, J.: A novel construction of substitution box using a combination of chaotic maps with improved chaotic range. Nonlinear Dynamics. 88, 2757–2769 (2017)
Isa, H., Jamil, N., Aba, M.R.Z.: Construction of cryptographically strong S-boxes inspired by bee waggle dance. N. Gener. Comput. 7, 221–238 (2016)
Cui, L., Cao, Y.: A new S-box structure named affine-power-affine. International Journal of Innovative Computing, Information and Control. 3(3), 751–759 (2007)
Hussain, I., Shah, T.: Literature survey on nonlinear components and chaotic nonlinear components of block ciphers. Nonlinear Dynamics. 74(4), 869–904 (2013)
Wang, Y.: "On cognitive informatics", brain and mind: a transdisciplinary. Journal of Neuroscience and Neurophilosophy. 4(3), 151–167 (2003)
Ahmad, M., Bhatia, D., Hassan, Y.: A novel colony optimization based scheme for substitution box design. Procedia Computer Science. 57, 572–580 (2015)
Wang, Y.: The theoretical framework of cognitive informatics. International Journal of Cognitive Informatics and Natural Intelligence. 1(1), 1–27 (2007)
Wang, Y., Wong, K.W., Li, C., Li, Y.: A novel method to design S-box based on chaotic map and genetic algorithm. Phys. Lett. A. 376(6), 827–833 (2012b)
Wang, Y.: On abstract intelligence: toward a unified theory of natural, artificial, machinable, and computational intelligence. International Journal of Software Science and Computational Intelligence. 1(1), 1–18 (2009). https://doi.org/10.4018/jssci.2009010101
Clark, J.A., Jacob, J.L., Stepney, S.: The design of S-boxes by simulated annealing. New Ge neration Computing. 23(3), 219–231 (2005)
Millan, W.: How to improve the nonlinearity of bijective S-boxes. In Australasian conference on information security and privacy, lecture notes in computer science. 1438, 181–192 (1998)
Fuller, J., Millan, W., Dawson, E.: Multi-objective optimisation of bijective S-boxes. N. Gener. Comput. 23(3), 201–218 (2005)
Laskari, E.C., Meletiou, G.C., Vrahatis, M.N.: Utilizing evolutionary computation methods for the design of S-boxes. In: International Conference on Computational Intelligence and Security, pp. 1299–1302 (2006)
Ahmad, M., Mittal, N., Garg, P., Khan, M.M.: Efficient cryptographic substitution box design using travelling salesman problem and chaos. Perspectives in Science. 8, 465–468 (2016)
Jamal, S.S., Shah, T., Attaullah, A.: A group action method for construction of strong substitution box. 3D Res. 8(2), 1–12 (2017)
Belazi, A., El-Latif, A.A.A.: A simple yet efficient S-box method based on chaotic sine map. Optik-International Journal for Light and Electron Optics. 130, 1438–1444 (2017)
Khan, M., Shah, T.: A novel construction of substitution box with Zaslavskii chaotic map and symmetric group. Journal of Intelligent and Fuzzy Maps. 28(4), 1509–1517 (2015a)
Waseem, H.M., Khan, M.: A new approach to digital content privacy using quantum spin and finite-state machine. Applied Physics B. 125(2), 27 (2019)
Khan, M., Shah, T.: A novel construction of substitution box with Zaslavskii chaotic map and symmetric group. Journal of Intelligent and Fuzzy Systems. 28(4), 1509–1517 (2015b)
Anees, A., Ahmed, Z.: A technique for designing substitution box based on van der pol oscillator. Wirel. Pers. Commun. 82(3), 1497–1503 (2015)
Gondal, M.A., Raheem, A., Hussain, I.: A scheme for obtaining secure S-boxes based on chaotic Baker’s map. 3D Res. 5(3), 1–8 (2014)
Khan, M., Shah, T., Batool, S.I.: Construction of S-box based on chaotic Boolean functions and its application in image encryption. Neural Comput. & Applic. 27(3), 677–685 (2016)
Islam, F., Liu, G.: Designing S-box based on 4D-4wing hyperchaotic system. 3D Research. 8(1), 1–9 (2017)
Burnett, L.: Heuristic optimization of boolean functions and substitution boxes for cryptography. Doctoral dissertation, Queensland University of Technology. (2005)
Khan, M., Asghar, Z.: A novel construction of substitution box for image encryption applications with Gingerbreadman chaotic map and S8 permutation. Neural Comput. & Applic. 29(4), 993–999 (2018)
Musheer, A., Doja, M.N., Sufyan, M.M., B.: ABC optimization based construction of strong substitution-boxes. Wirel. Pers. Commun. (2018). https://doi.org/10.1007/s11277-018-5787-1
Skiadas, C.H., Skiadas, C.: Chaotic Modelling and Simulation; Analysis of Chaotic Models, Attractors and Forms. Chapman & Hall/CRC Taylor & Francis Group, New York (2009)
Alamsyah, A.B., Adji, T.B.: The replacement of irreducible polynomial and affine mapping for the construction of a strong S-box. Nonlinear Dynamics. (2018). https://doi.org/10.1007/s11071-018-4310-2
Webster, A.F., Tavares, S.E.: On the design of S-boxes. Advances in Cryptology, Lecture Notes in Computer Science. 218, 523–534 (1986)
Adams, C., Tavares, S.: The structured design of cryptographically good S-boxes. J. Cryptol. 3(1), 27–41 (1990)
Biham, E., Shamir, A.: Differential cryptanalysis of DES-like cryptosystems. J. Cryptol. 4(1), 3–72 (1991)
Kazlauskas, K., Vaicekauskas, G., Smaliukas, R.: An algorithm for key-dependent S-box generation in block cipher system. Informatica. 26(1), 51–65 (2015)
Wei, Z., Moroz, I., Sprott, J.C., Akgul, A., Zhang, W.: Hidden hyperchaos and electronic circuit application in a 5D self-exciting homopolar disc dynamo. Chaos. 27(3), 033101 (2017a)
Wei, Z., Moroz, I., Sprott, J.C., Wang, Z., Zhang, W.: Detecting hidden chaotic regions and complex dynamics in the self-exciting homopolar disc dynamo. International Journal of Bifurcation and Chaos. 27(2), 1730008 (2017b)
Wei, Z., Zhu, B., Yang, J., Perc, M., Slavinec, M.: Bifurcation analysis of two disc dynamos with viscous friction and multiple time delays. Appl. Math. Comput. 347, 265–281 (2019)
Levnajic, Z., Mezic, I.: Ergodic theory and visualization. II. Fourier mesochronic plots visualize (quasi)periodic sets. Chaos. 25, 053105 (2015)
Shannon, C.E.: Communication theory of secrecy systems. Bell system technical journal. 28(4), 656–715 (1949)
Shannon, C.E.: A mathematical theory of communication. Bell system technical journal. 27(3), 379–423 (1948)
Rafiq, A., Khan, M.: Construction of new S-boxes based on triangle groups and its applications in co pyright protection. Multimed. Tools Appl. 1–18 (2018)
Younas, I., Khan, M.: A new efficient digital image encryption based on inverse left almost semi group and Lorenz chaotic system. Entropy. 20(12), 913 (2018)
Khan, M., Waseem, H.M.: A novel image encryption scheme based on quantum dynamical spinning and rotations. PLoS One. 13(11), e0206460 (2018)
Waseem, H.M., Khan, M., Shah, T.: Image privacy scheme using quantum spinning and rotation. Journal of Electronic Imaging. 27(6), 063022 (2018)
Waseem, H.M., Khan, M.: Information Confidentiali ty using quantum spinning, rotation and finite state machine. Int. J. Theor. Phys. 57(11), 3584–3594 (2018)
Munir, N., Khan, M.: A Generalization of Algebraic Expression for Nonlinear Component of Symmetric Key Algorithms of Any Characteristic p. In 2018 International Conference on Applied and Engineering Mathematics (ICAEM). IEEE. 48–52 (2018)
Khan, M., Munir, N.: A novel image encryption technique based on generalized advanced encryption standard based on field of any characteristic. Wireless and Personal Communications. https://doi.org/10.1007/s11277-019-06594-6
Belazi, A., Khan, M., El-Latif, A.A.A., Belghith, S.: Efficient cryptosystem approaches: S-boxes and permutation–substitution-based encryption. Nonlinear Dynamics. 87(1), 337–361 (2017)
Khan, M., Shah, T., Batool, S.I.: A new approach for image encryption and watermarking based on substitution box over the classes of chain rings. Multimed. Tools Appl. 76(22), 24027–24062 (2017)
Ali, K.M., Khan, M.: A new construction of confusion component of block ciphers. Multimed. Tools Appl. (2019). https://doi.org/10.1007/s11042-019-07866-w
Khan, M., Masood, F.: A novel chaotic image encryption technique based on multiple discrete dynamical maps. Multimed. Tools Appl. https://doi.org/10.1007/s11042-019-07818-4
Khan, M., Waseem, H.M.: A novel digital contents privacy scheme based on Kramer's arbitrary spin. Int. J. Theor. Phys. https://doi.org/10.1007/s10773-019-04162-z
Özkaynak, F.: Construction of robust substitution boxes based on chaotic systems. Neural Comput. & Applic. 1–10 (2017)
Özkaynak, F.: Brief review on application of nonlinear dynamics in image encryption. Nonlinear Dynamics. 92(2), 305–313 (2018)
Ahmad, M., Khurana, S., Singh, S., AlSharari, H.D.: A simple secure hash function scheme using multiple chaotic maps. 3D Res. 8(2), 13 (2017)
Al Solami, E., Ahmad, M., Volos, C., Doja, M., Beg, M.: A new hyperchaotic system-based design for efficient bijective substitution-boxes. Entropy. 20(7), 525 (2018a)
Ahmad, M., Al Solami, E., Wang, X.Y., Doja, M., Beg, M., Alzaidi, A.: Cryptanalysis of an image encryption algorithm based on combined chaos for a BAN system, and improved scheme using SHA-512 and hyperchaos. Symmetry. 10(7), 266 (2018a)
Ahmad, M., Seeru, F., Siddiqi, A.M., Masood, S.: Dynamic 9× 9 Substitution-Boxes Using Chaos-Based Heuristic Search. In Soft Computing: Theories and Applications, pp. 839–851. Springer, Singapore (2018b)
Ahmed, H.A., Zolkipli, M.F., Ahmad, M.: A novel efficient substitution-box design based on firefly algorithm and discrete chaotic map. Neural Comput. & Applic. 1–10
Al Solami, E., Ahmad, M., Volos, C., Doja, M., Beg, M.: A new hyper chaotic system-based design for efficient bijective substitution-boxes. Entropy. 20(7), 525 (2018b)
Ahmad, M., Alam, M.Z., Umayya, Z., Khan, S., Ahmad, F.: An image encryption approach using particle swarm optimization and chaotic map. Int. J. Inf. Technol. 10(3), 247–255 (2018c)
Alzaidi, A.A., Ahmad, M., Ahmed, H.S., Solami, E.A.: Sine-cosine optimization-based bijective substitution-boxes construction using enhanced dynamics of chaotic map. Complexity. 2018 (2018)
Vaidyanathan, S., Akgul, A., Kaçar, S., Çavuşoğlu, U.: A new 4-D chaotic hyperjerk system, its synchronization, circuit design and applications in RNG, image encryption and chaos-based steganography. The European Physical Journal Plus. 133(2), 46 (2018)
Akgul, A., Kacar, S., Pehlivan, I., Aricioglu, B.: Chaos-based encryption of multimedia data and design of security analysis interface as an educational tool. Comput. Appl. Eng. Educ. 26(5), 1336–1349 (2018)
Wang, X., Akgul, A., Cavusoglu, U., Pham, V.T., Vo Hoang, D., Nguyen, X.: A chaotic system with infinite equilibria and its S-box constructing application. Appl. Sci. 8(11), 2132 (2018)
Lai, Q., Akgul, A., Varan, M., Kengne, J., Erguzel, A.T.: Dynamic analysis and synchronization control of an unusual chaotic system with exponential term and coexisting attractors. Chin. J. Phys. (2018)
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The authors declare that there is no conflict of interest.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ali, K.M., Khan, M. Application Based Construction and Optimization of Substitution Boxes Over 2D Mixed Chaotic Maps. Int J Theor Phys 58, 3091–3117 (2019). https://doi.org/10.1007/s10773-019-04188-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-019-04188-3