Abstract
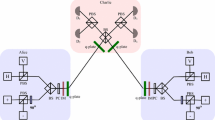
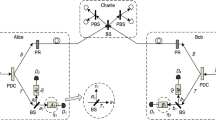
Measurement-device-independent quantum key distribution (MDI-QKD) not only eliminates all detector side channel attacks, but also doubles the secure transmission distance. To improve the performance of MDI-QKD, we propose a high dimensional encoding scheme. By a spatial-temporal mode conversion circuit and quantum state fusion operation, two polarization modes of two photons are converted into the temporal-polarization mode of one photon. Also, by adding a temporal-spatial mode conversion circuit to quantum state fission apparatus, the temporal-polarization mode of one photon can be split into two polarization modes of two photons. By these two processes, each of the two legitimate parties is able to send photons in high dimensional temporal and polarization modes, and the measurement server still performs Bell state measurements (BSMs) after states fission. Hence, the total output rate can be improved. In addition, one of the recovered polarization states keeps stable for channel noise. The numerical simulation results show that by this new scheme, the key generation rate increases by 2∼10 times and transmission distance increases by 6∼60 km for different polarization misalignment errors.






Similar content being viewed by others
References
BENNET, C.H.: Quantum cryptography: Public key distribution and coin tossing. In: Proc. of IEEE Int. Conf. on Comp., Syst. and Signal Proc., Bangalore, India, Dec. 10–12, 1984 (1984)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74, 145 (2002)
Scarani, V., Bechmann-Pasquinucci, H., Cerf, N.J., Dušek, M., Lütkenhaus, N., Peev, M.: The security of practical quantum key distribution. Rev. Mod. Phys. 81, 1301 (2009)
Lo, H.K., Curty, M., Tamaki, K.: Secure quantum key distribution. Nat. Photonics 8(8), 595 (2015)
Shor, P.W., Preskill, J.: Simple proof of security of the bb84 quantum key distribution protocol. Phys. Rev. Lett. 85, 441 (2000)
Huttner, B., Imoto, N., Gisin, N., Mor, T.: Quantum cryptography with coherent states. Phys. Rev. A 51, 1863 (1995)
Brassard, G., Lütkenhaus, N., Mor, T., Sanders, B.C.: Limitations on practical quantum cryptography. Phys. Rev. Lett. 85, 1330 (2000)
Fung, C.H.F., Qi, B., Tamaki, K., Lo, H.K.: Phase-remapping attack in practical quantum-key-distribution systems. Phys. Rev. A 75, 032314 (2007)
Zhao, Y., Fung, C.H.F., Qi, B., Chen, C., Lo, H.K.: Quantum hacking: Experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys. Rev. A 78, 042333 (2008)
Qi, B., Fung, C.H.F., Lo, H.K., Ma, X.: Time-shift attack in practical quantum cryptosystems. Quantum Information & Computation 7(1), 73 (2005)
Makarov, V., Anisimov, A., Skaar, J.: Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys. Rev. A 74, 022313 (2006)
Lydersen, L., Wiechers, C., Wittmann, C., Elser, D., Skaar, J., Makarov, V.: Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photonics 4(10), 686 (2010)
da Silva, T.F., Xavier, G.B., ao, G.P.T., von der Weid, J.P.: Real-time monitoring of single-photon detectors against eavesdropping in quantum key distribution systems. Opt. Express 20(17), 18911 (2012)
Yuan, Z.L., Dynes, J.F., Shields, A.J.: Resilience of gated avalanche photodiodes against bright illumination attacks in quantum cryptography. Appl. Phys. Lett. 98(23), 231104 (2011)
Acín, A., Brunner, N., Gisin, N., Massar, S., Pironio, S., Scarani, V.: Device-independent security of quantum cryptography against collective attacks. Phys. Rev. Lett. 98, 230501 (2007)
Pironio, S., Acín, A., Brunner, N., Gisin, N., Massar, S., Scarani, V.: Device-independent quantum key distribution secure against collective attacks. New J. Phys. 11(4), 045021 (2009)
Gisin, N., Pironio, S., Sangouard, N.: Proposal for implementing device-independent quantum key distribution based on a heralded qubit amplifier. Phys. Rev. Lett. 105, 070501 (2010)
Curty, M., Moroder, T.: Heralded-qubit amplifiers for practical device-independent quantum key distribution. Phys. Rev. A 84, 010304 (2011)
Lo, H.K., Curty, M., Qi, B.: Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012)
Biham, E., Huttner, B., Mor, T.: Quantum cryptographic network based on quantum memories. Phys. Rev. A 54, 2651 (1996)
Inamori: Security of practical time-reversed epr quantum key distribution. Algorithmica 34(4), 340 (2002)
Hwang, W.Y.: Quantum key distribution with high loss: Toward global secure communication. Phys. Rev. Lett. 91, 057901 (2003)
Lo, H.K., Ma, X., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005)
Wang, X.B.: Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94, 230503 (2005)
Ma, X., Qi, B., Zhao, Y., Lo, H.K.: Practical decoy state for quantum key distribution. Phys. Rev. A 72, 012326 (2005)
Yin, H.L., Chen, T.Y., Yu, Z.W., Liu, H., You, L.X., Zhou, Y.H., Chen, S.J., Mao, Y., Huang, M.Q., Zhang, W.J., Chen, H., Li, M.J., Nolan, D., Zhou, F., Jiang, X., Wang, Z., Zhang, Q., Wang, X.B., Pan, J.W.: Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett. 117, 190501 (2016)
Vitelli, C., Spagnolo, N., Sciarrino, F., Marrucci, L., Santamato, E.: Joining the quantum state of two photons into one. Nat. Photonics 7(7), 521 (2013)
Wei, H., Zhu, C., Pei, C.: . In: 2017 IEEE 9th International Conference on Communication Software and Networks (ICCSN), pp. 97–101 (2017)
Xu, F., Curty, M., Qi, B., Lo, H.K.: Practical aspects of measurement-device-independent quantum key distribution. New J. Phys. 15(11), 113007 (2013)
U’Ren, A.B., Silberhorn, C., Banaszek, K., Walmsley, I.A.: Efficient conditional preparation of high-fidelity single photon states for fiber-optic quantum networks. Phys. Rev. Lett. 93, 093601 (2004)
Fasel, S., Alibart, O., Tanzilli, S., Baldi, P., Beveratos, A., Gisin, N., Zbinden, H.: High-quality asynchronous heralded single-photon source at telecom wavelength. New J. Phys. 6(1), 163 (2004)
Ding, X., He, Y., Duan, Z.C., Gregersen, N., Chen, M.C., Unsleber, S., Maier, S., Schneider, C., Kamp, M., Höfling, S., Lu, C.Y., Pan, J.W.: On-demand single photons with high extraction efficiency and near-unity indistinguishability from a resonantly driven quantum dot in a micropillar. Phys. Rev Lett. 116, 020401 (2016)
Somaschi, N., Giesz, V., Santis, L.D., Loredo, J.C., Almeida, M.P., Hornecker, G., Portalupi, S.L., Grange, T., Antón, C., Demory, J.: Near-optimal single-photon sources in the solid state. Nat. Photonics 10, 340–345 (2016)
Acknowledgements
This work was supported by the National Natural Science Foundation of China (Grant Nos. 61372076, 61701375), Shaanxi Key Research and Development Program (Grant No. 2017GY-080), Foundation of Science and Technology on Communication Networks Laboratory (KX172600031) and the 111 Project (No. B08038).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Li, L., Zhu, C., Quan, D. et al. A High Dimensional Measurement-Device-Independent Quantum Key Distribution Scheme Based on Optical Quantum State Fusion and Fission. Int J Theor Phys 57, 3902–3911 (2018). https://doi.org/10.1007/s10773-018-3902-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-018-3902-4