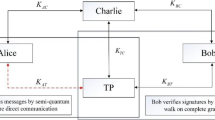
Abstract
In recent years, some quantum proxy signature schemes based on controlled teleportation are proposed by Cao et al.. In these schemes, the properties of quantum mechanics are directly applied to ensure the security. In this paper, we have summarized a general model from the quantum proxy signature schemes. Furthermore, it can be seen that there exist some loopholes which have not been considered in the previous analysis. Specifically, the receiver can forge a valid signature. And these schemes can not be immune to collusive attack. To overcome these loopholes, some improved ideas are presented in this paper.

Similar content being viewed by others
References
Grover, L.K.: Fast quantum mechanical algorithm for database search. In: Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, pp. 212–219. ACM (1996)
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 41(2), 303–332 (1999)
Gottesman, D., Chuang, I.: Quantum digital signatures arXiv:quant-ph/0105032 (2001)
Barnum, H, Crpeau, C, Gottesman, D, et al.: Authentication of quantum messages. In: The 43rd Annual IEEE Symposium on Foundations of Computer Science. Proceedings, pp. 449–458. IEEE (2002)
Zeng, G, Keitel, CH.: Arbitrated quantum-signature scheme. Phys. Rev. A 65(4), 042312 (2002)
Lee, H, Hong, C, Kim, H, et al.: Arbitrated quantum signature scheme with message recovery. Phys. Lett. A 321(5), 295–300 (2004)
Li, Q., Chan, W.H., Long, D.Y.: Arbitrated quantum signature scheme using Bell states. Phys. Rev. A 79(5), 054307 (2009)
Zou, X., Qiu, D.: Security analysis and improvements of arbitrated quantum signature schemes. Phys. Rev. A 82(4), 042325 (2010)
Yang, Y.G., Wen, Q.Y.: Arbitrated quantum signature of classical messages against collective amplitude damping noise. Opt. Commun. 283(16), 3198–3201 (2010)
Gao, F., Qin, S.J., Guo, F.Z., et al.: Cryptanalysis of the arbitrated quantum signature protocols. Phys. Rev. A 84, 022344 (2011)
Yu, C.H., Guo, G.D., Lin, S.: Arbitrated quantum signature scheme based on reusable key. Sci. Chin. Phys. Mech. Astron. 57(11), 2079–2085 (2014)
Mambo, M., Usuda, K., Okamoto, E.: Proxy signatures: Delegation of the power to sign messages. IEICE Trans. Fund. Electron. Commun. Comput. Sci. 79(9), 1338–1354 (1996)
Zhou, J.X., Zhou, Y.J., Niu, X.X., et al.: Quantum proxy signature scheme with public verifiability. Sci. Chin. Phys. Mech. Astron. 54(10), 1828–1832 (2011)
Wang, T.Y., Wei, Z.L.: One-time proxy signature based on quantum cryptography. Quant. Inf. Process 11(2), 455–463 (2012)
Yi, L., Bai, G., Xiao, G.: Proxy multi-signature scheme: A new type of proxy signature scheme. Electron. Lett. 36(6), 527–528 (2000)
Yi, L., Bai, G., Xiao, G.: New multi-proxy multi-signature schemes. Electron. Lett. 36(6), 527–528 (2000)
Hwang, S.J., Chen, C.C.: New multi-proxy multi-signature schemes. Appl. Math. Comput. 147(1), 57–67 (2004)
Shin-Jia, H., Chiu-Chin, C.: New multi-proxy multi-signature schemes. Appl. Math. Comput. 147(1), 57–67 (2004)
Wen, X.J., Liu, Y., Sun, Y.: Quantum multi-signature protocol based on teleportation. Zeitschrift fr Naturforschung A 62(3-4), 147–151 (2007)
Zuo, H., Zhang, K., Song, T.: Security analysis of quantum multi-signature protocol based on teleportation. Quant. Inf. Process. 12(7), 2343–2353 (2013)
Ding, W., Zhang, J.Z.: New multi-proxy multi-signature scheme. Jisuanji Yingyong Yanjiu 27(8), 3081–3082 (2010)
Wang, T.Y., Cai, X.Q., Zhang, J.Z.: Off-line e-cash system with multiple banks based on elliptic curve. Jisuanji Gongcheng/ Comput. Eng. 33(15), 155–157 (2007)
Cao, F., Cao, Z.: A secure identity-based proxy multi-signature scheme. Inform. Sci. 179(3), 292–302 (2009)
Gao, F., Guo, F.Z., Wen, Q.Y., et al.: Comment on Experimental demonstration of a quantum protocol for byzantine agreement and liar detection. Phys. Rev. lett. 101 (20), 208901 (2008)
Zhang, Y.S., Li, C.F., Guo, G.C.: Comment on quantum key distribution without alternative measurements. Phys. Rev. A 63(3), 036301 (2001)
Wang, T.Y., Wen, Q.Y., Chen, X.B.: Cryptanalysis and improvement of a multi-user quantum key distribution protocol. Opt. Commun. 283(24), 5261–5263 (2010)
Fei, G., Qiao-Yan, W., Fu-Chen, Z.: Teleportation attack on the QSDC protocol with a random basis and order. Chin. Phys. B 17(9), 3189 (2008)
Wang, T., Wen, Q., Gao, F., et al.: Cryptanalysis and improvement of multiparty quantum secret sharing schemes. Phys. Lett. A 373(1), 65–68 (2008)
Qin, S.J., Gao, F., Wen, Q.Y., et al.: Improving the security of multiparty quantum secret sharing against an attack with a fake signal. Phys. Lett. A 357(2), 101–103 (2006)
Wjcik, A.: Eavesdropping on the ping-pong quantum communication protocol. Phys. Rev. Lett. 90(15), 157901 (2003)
Wjcik, A.: Comment on Quantum dense key distribution. Phys. Rev. A 71(1), 016301 (2005)
Cai, Q.: The Ping-Pong protocol can be attacked without eavesdropping. Phys. Rev. Lett. 91(10), 109801 (2003)
Gao, F., Guo, F.Z., Wen, Q.Y., et al.: Consistency of shared reference frames should be reexamined. Phys. Rev. A 77(1), 014302 (2008)
Fei, G., Song, L., Qiao-Yan, W., et al.: A special eavesdropping on one-sender versus N-receiver QSDC protocol. Chin. Phys. Lett. 25(5), 1561 (2008)
Gao, F., Qin, S.J., Wen, Q.Y., et al.: Cryptanalysis of multiparty controlled quantum secure direct communication using GreenbergerCHorneCZeilinger state. Opt. Commun. 283(1), 192–195 (2010)
Deng, F.G., Li, X.H., Zhou, H.Y., et al.: Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A 72(4), 044302 (2005)
Gisin, N., Fasel, S., Kraus, B., et al.: Trojan-horse attacks on quantum-key-distribution systems. Phys. Rev. A 73(2), 022320 (2006)
Gao, F., Qin, S.J., Wen, Q.Y., et al.: A simple participant attack on the brdler-dusek protocol. Quant. Inf. Comput. 7(4), 329–334 (2007)
Wang, T.Y., Wen, Q.Y.: Security of a kind of quantum secret sharing with single photons. Quant. Inf. Comput. 11(5), 434–443 (2011)
Chen, X.B., Yang, S., Su, Y., et al.: Cryptanalysis on the improved multiparty quantum secret sharing protocol based on the GHZ state. Physica Scripta 86(5), 055002 (2012)
Wang, T.Y., Wen, Q.Y., Zhu, F.C.: Cryptanalysis of multiparty quantum secret sharing with Bell states and Bell measurements. Opt. Commun. 284(6), 1711–1713 (2011)
Lin, S., Yu, C.H., Guo, G.D.: Reexamining the security of fair quantum blind signature schemes. Quant. Inf. Process 13(11), 2407–2415 (2014)
Cao, H.J., Huang, J., Yu, Y.F., et al.: A quantum proxy signature scheme based on genuine five-qubit entangled state. Int. J. Theor. Phys. 53(9), 3095–3100 (2014)
Cao, H.J., Wang, H.S., Li, P.F.: Quantum proxy multi-signature scheme using genuinely entangled six qubits state. Int. J. Theor. Phys. 52(4), 1188–1193 (2013)
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283(5410), 2050–2056 (1999)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441 (2000)
Gobby, C., Yuan, Z.L., Shields, A.J.: Quantum key distribution over 122 km of standard telecom fiber. Appl. Phys. Lett. 84(19), 3762–3764 (2004)
Allaume, R., Branciard, C., Bouda, J., et al.: Using quantum key distribution for cryptographic purposes: A survey. Theor. Comput. Sci. 560, 62–81 (2014)
Acknowledgments
This work is supported by National Natural Science Foundation of China under Grant No.11647128; the Natural Science Foundation of Heilongjiang Province under Grant No.A2016007; the China Scholarship Council (Grant No. 201506470043, 201607320084) and Youth Foundation of Heilongjiang University under Grant No.QL201501.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhang, L., Zhang, HY., Zhang, KJ. et al. The Security Analysis and Improvement of Some Novel Quantum Proxy Signature Schemes. Int J Theor Phys 56, 1983–1994 (2017). https://doi.org/10.1007/s10773-017-3342-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-017-3342-6